NIST CSF Categories: Description, Examples, and Best Practices
This article delves into the elements of NIST CSF v1.1, which was released in 2018. It also dedicates a section to the NIST CSF v2.0 framework (shared for public feedback in 2023 for release in 2024) to highlight the upcoming changes. These include revisions to subcategory naming for clarity and the addition of a “Govern” function to ensure comprehensive integration of governance within the cybersecurity program.
Summary of NIST CSF categories
In the ever-evolving landscape of cybersecurity threats, organizations need a robust but flexible framework to guide their cybersecurity risk management programs. The National Institute of Standards (NIST) Cybersecurity Framework (CSF) stands as just such a beacon, providing a structured and usable approach to identifying, protecting, detecting, responding to, and recovering from cyber risks. In this article, we delve into the core elements of the NIST CSF, exploring its five functions and the 23 categories that form the backbone of this framework.
Before we plunge into the specifics of the CSF, let’s set the stage by explaining the significance of the NIST CSF in the current cybersecurity landscape. Unlike a maturity or capability model, the NIST CSF is designed to allow organizations to tailor it to fit their needs. This flexibility means that the NIST CSF is a great framework for all types of organizations, whether or not they already have very mature cybersecurity programs.
The CSF consists of five functions—Identify, Protect, Detect, Respond, and Recover—which are summarized in the table below. Each function is associated with a set of categories that form the basis for actionable cybersecurity processes and is described in the sections that follow.
| Function | Description |
|---|---|
| Identify | This function focuses on understanding and managing cybersecurity risk to systems, assets, data, and capabilities. |
| Protect | The Protect function is oriented toward developing and implementing appropriate safeguards to ensure the delivery of critical services. |
| Detect | This function emphasizes developing and implementing the activities required to identify the occurrence of cybersecurity events. |
| Respond | This part of the model focuses on developing and implementing activities to take action on detected cybersecurity incidents. |
| Recover | Finally, the Recover function describes how to ensure organization resilience by developing and implementing activities to maintain plans and restore capabilities and/or services impaired by cybersecurity incidents. |
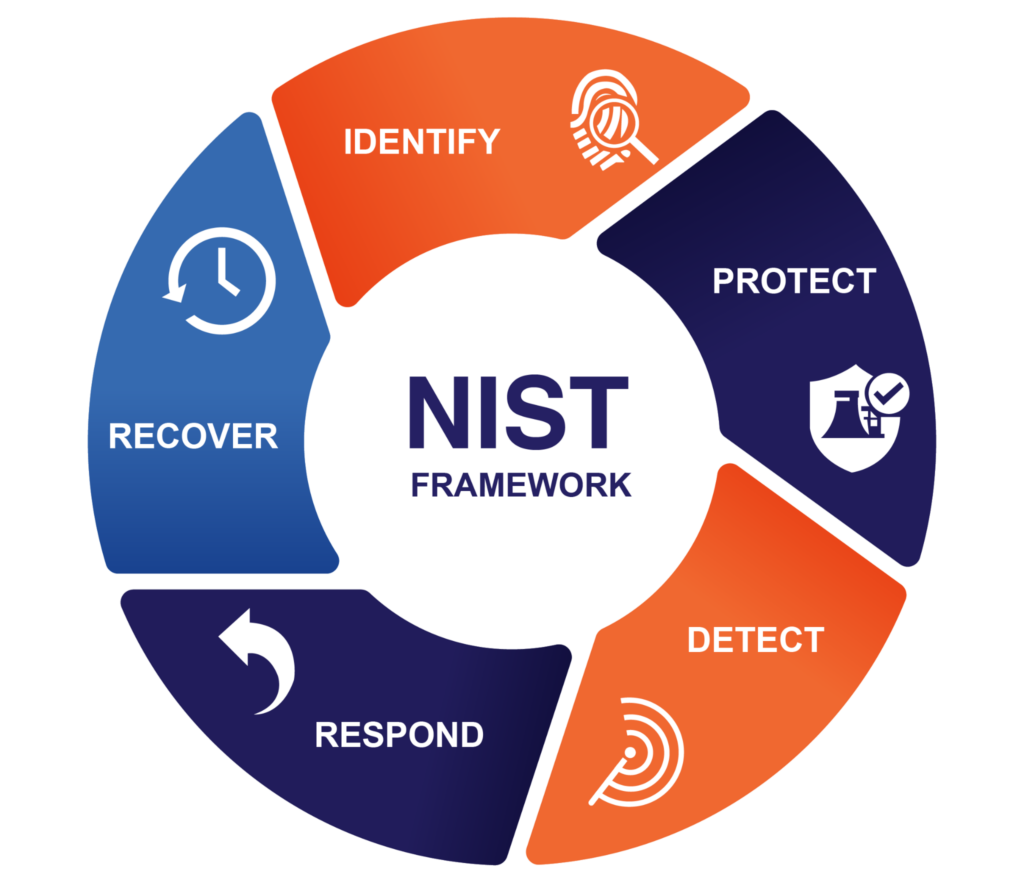
The NIST Cybersecurity Framework (CSF) and its categories (source)
Identify (ID)
The Identify function is all about understanding and managing cybersecurity risk, so you can develop an overall risk management approach. It encompasses six categories, which are summarized in the table below and described in detail in the subsections that follow the table.
| Category | Description of activities |
|---|---|
| Asset Management (ID.AM) | Identify and manage the data, personnel, devices, systems, and facilities that enable the organization to achieve its objectives. |
| Business Environment (ID.BE) | Understand the business context, resources that support critical functions, and organizational risk. |
| Governance (ID.GV) | Establish and implement policies, processes, and procedures to manage and monitor the organization’s regulatory, legal, risk, and environmental requirements. |
| Risk Assessment (ID.RA) | Identify and assess the risks to the organization’s operations, assets, and individuals. |
| Risk Management Strategy (ID.RM) | Establish the organization’s overall cyber risk priorities, constraints, risk tolerances, and assumptions. |
| Supply Chain Risk Management (ID.SC) | Establish the organization’s priorities, constraints, risk tolerances, and assumptions used to support risk decisions when managing supply chain risk. Establish and implement processes to identify, assess, and manage supply chain risks. |
Asset Management (ID.AM)
This category includes inventorying the physical hardware, devices, and software assets within the organization to establish the basis of an asset management program. In addition, you should include the cataloging of external systems, such as those owned by vendors or other third parties, if you have them.
As these assets are identified, it is helpful to map or identify the flow of information within your organization. Also, look at prioritizing your organization’s resources, such as data, devices, personnel, and other important parts of the asset management program.
Many of these components may exist both internally and externally. It is vital to ensure that cybersecurity roles and responsibilities are established and understood by your own employees as well as those third-party stakeholders with physical and logical access to your organization.
Using an automation tool like Device42 can greatly reduce the time and effort required to discover IT assets and map them to critical applications. We will share a bit more about this when we recommend best practices later in the article.
Business Environment (ID.BE)
This includes identifying your organization’s role within the supply chain and its place in the industry or sector in which it operates. It also encompasses establishing and communicating your organization’s mission, objectives, and the activities necessary for it to operate.
Essentially, what are those critical services your organization is reliant upon to perform its primary function, and have you established resilience requirements for them?
Governance (ID.GV)
The Governance category covers understanding the cybersecurity legal and regulatory requirements your organization must follow and ensuring that they are properly managed by the appropriate organizational authority.
In addition, this category builds on the cybersecurity roles and responsibilities identified in Asset Management. It adds another layer to ensure that they are coordinated and aligned with both internal roles and external partners.
Finally, this category covers the establishment and communication of your organization’s cybersecurity policies as well as whether your organization addresses its cybersecurity risks through governance and risk management processes.
Risk Assessment (ID.RA)
The Risk Assessment category includes identifying the vulnerabilities and threats to your organization and its assets. There are many ways to do this, such as leveraging Information Sharing Analysis Centers (ISACs) for critical infrastructure organizations, threat feeds from third parties, and vulnerability scanning of your network and assets. Once this information has been gathered, your organization should look at the potential impact and likelihood of these threats before determining the organization’s risk and corresponding risk response.
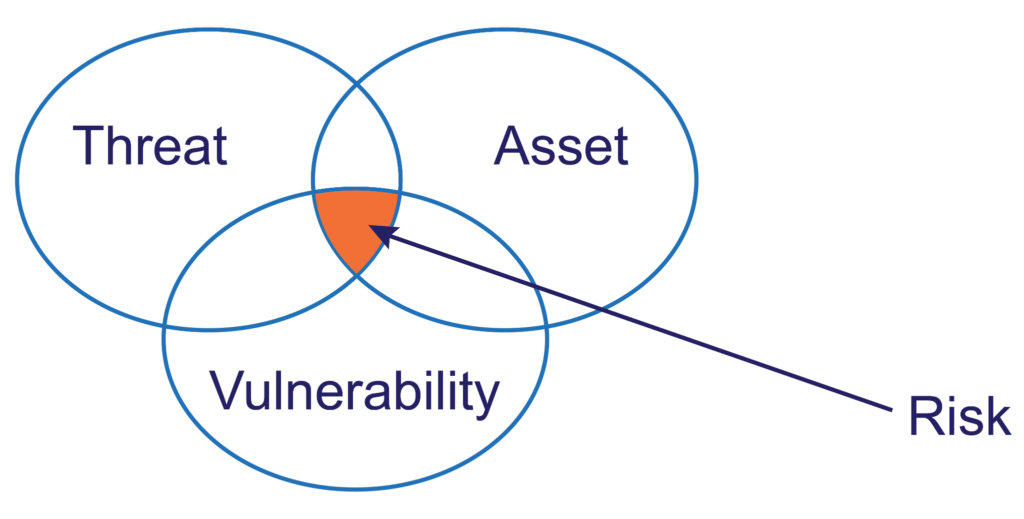
The three fundamental cybersecurity concepts (source)
Risk Management Strategy (ID.RM)
Your organization needs to consider the appropriate risk responses that leadership is comfortable with and supports, as informed by risk analysis. For instance, since not all risk can be eliminated, it is important that your organization look at several options, such as mitigating risk when it makes sense financially and transferring risk onto third parties (such as cyber insurance providers) when that is appropriate. Being able to identify and document these risk responses is vital to an effective risk management strategy.
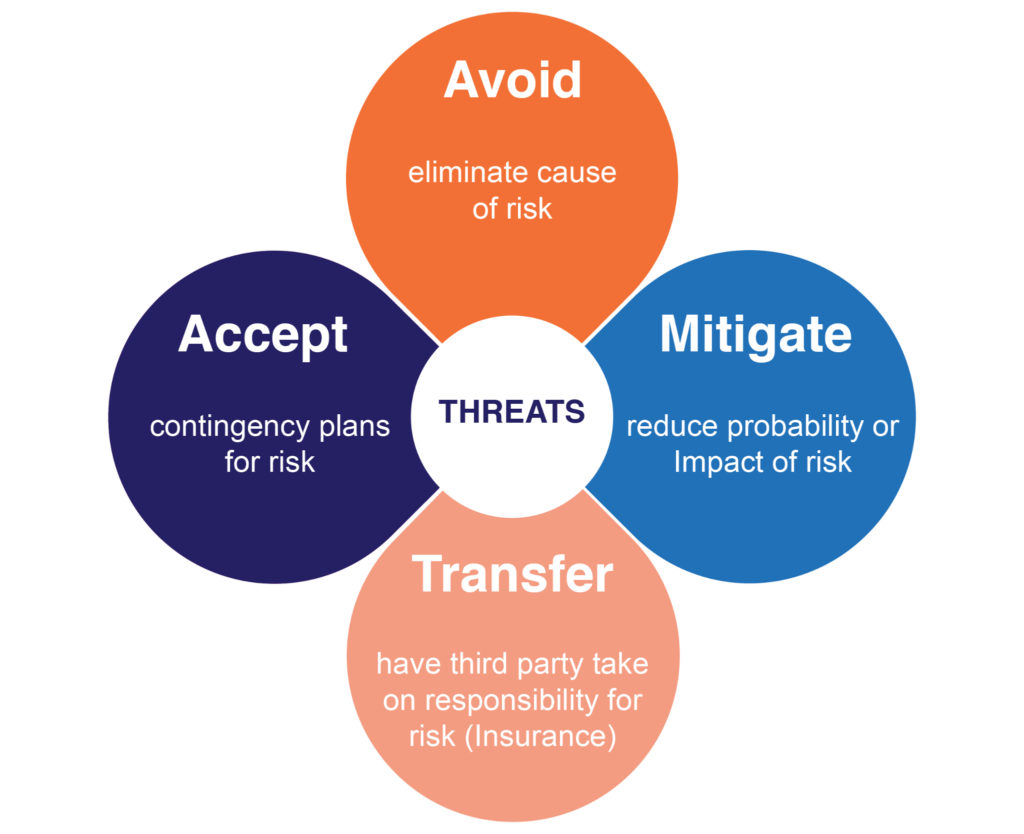
The four risk responses (source)
Supply Chain Risk Management (ID.SC)
This category includes managing third parties and supply chain risk in line with the organization’s overall cyber risk management strategy. Supply chain risk is complex and poses many challenges for organizations in all industries, as evidenced by a recent report indicating that 98% of organizations are connected to a third party that has been breached.
Managing third parties properly means applying cyber risk management processes to them throughout the lifecycle. This must be done while ensuring that contracts are reviewed and updated, performing assessments and audits on those vendors with access, and planning appropriate response and recovery activities with those deemed critical to your organization.
Protect (PR)
The Protect function helps you implement appropriate defenses based on your needs and requirements to ensure ongoing business operations. It includes identity management, training, data security, processes and procedures, maintenance, and more, as summarized in the table below and described in more detail in the subsections that follow.
| Category | Description of activities |
|---|---|
| Identity Management, Authentication and Access Control (PR.AC) | Manage access to physical and logical assets in a way consistent with the assessed risk of unauthorized access to authorized activities and transactions. |
| Awareness and Training (PR.AT) | Educate and train organization personnel and partners to perform their cybersecurity-related duties and responsibilities as necessary based on related policies, procedures, and agreements. |
| Data Security (PR.DS) | Manage data and information as needed based on the organization’s risk strategy in order to protect the confidentiality, integrity, and availability of data operations. |
| Information Protection Processes and Procedures (PR.IP) | Manage the protection of systems and assets, consistent with security policies, processes, and procedures. |
| Maintenance (PR.MA) | Perform maintenance and repairs of assets based on relevant policies and procedures. |
| Protective Technology (PR.PT) | Manage technical security solutions in a way that is consistent with policies, procedures, and agreements to ensure the security and resilience of systems and assets. |
Identity Management, Authentication, and Access Control (PR.AC)
This category encompasses the users, assets, and other devices attempting to access your organization both physically and logically. You may wonder why cybersecurity would be concerned with physical access, but cyber incidents can be carried out via physical means. Consider an unsecured data center; it might allow a malicious actor to waltz in and plug a USB drive infected with malware into a critical application’s server, bringing the application down and the organization’s business or operations to a complete halt.
This category also focuses on security principles and ensuring that anything connecting to your organization or accessing critical data is verified, trusted, and managed.
Awareness and Training (PR.AT)
This area of concern is all about ensuring that cybersecurity awareness is established and training is performed that reaches all facets of the organization, including external parties and senior leaders. All users should be well-informed of cybersecurity trends and potential threats.
Privileged users should know that they play a critical role in the organization and that it’s essential that they understand and execute on maintaining security principles when accessing critical data and systems as part of their daily operations. Additionally, senior leadership should not be overlooked because many cyber campaigns are known to target senior executives.
Data Security (PR.DS)
We have all heard about the CIA triad model when it comes to information security. This category focuses on the confidentiality, integrity, and availability of data and information within your organization during its lifecycle:
- Confidentiality requires a multifaceted process that involves securing data at rest and in transit to protect against unauthorized access to data or tampering, interception, or manipulation. Protections such as DLP solutions can be used here as well to prevent unauthorized disclosure through email, network, removable media, or other mechanisms. Organizational assets storing and processing data should have formal management throughout their lifecycles, including acquisition/development, removal, transfer, and disposal (or “sunsetting”) of assets.
- Availability means ensuring that adequate capacity is maintained or, at least, available to spin up. Additional resources may be needed in the event of a major spike in demand or, more nefariously, something like a DDoS attack against your organization.
- Integrity in the context of data and information is ensured by separating testing environments from production and conducting integrity checks on software, hardware, firmware, and information.
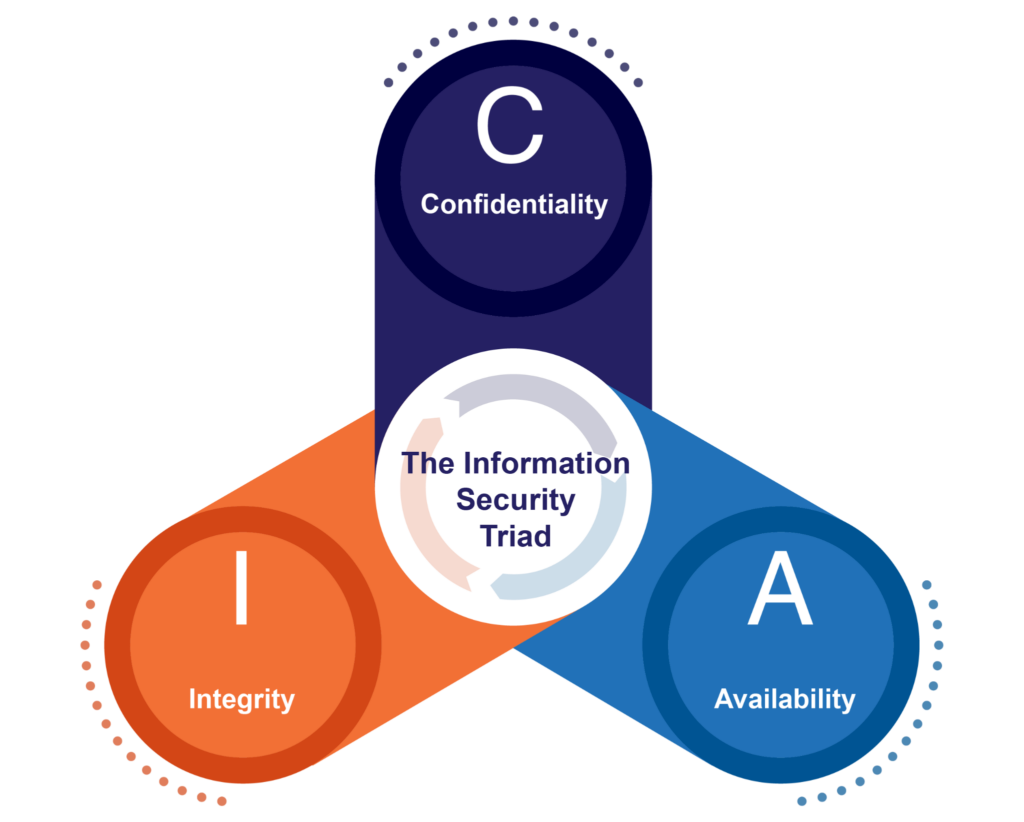
The “CIA” information security triad (source)
Information Protection Processes and Procedures (PR.IP)
This category is the largest in the NIST CSF, with 12 subcategories. As the name suggests, it is about managing and communicating the organization’s information protection throughout the lifecycle and begins to build the link to response and recovery activities that are covered in the later functions.
Begin with implementing a set of configuration baselines for systems, which will allow the organization to consistently deploy proven, verified, and secure systems. This activity sets the stage for implementing a system development lifecycle (SDLC). This can come across as confusing to some organizations but essentially means applying a standard of privacy and security requirements on systems that are either procured or developed through their lifecycles, going all the way through their disposal or retirement.
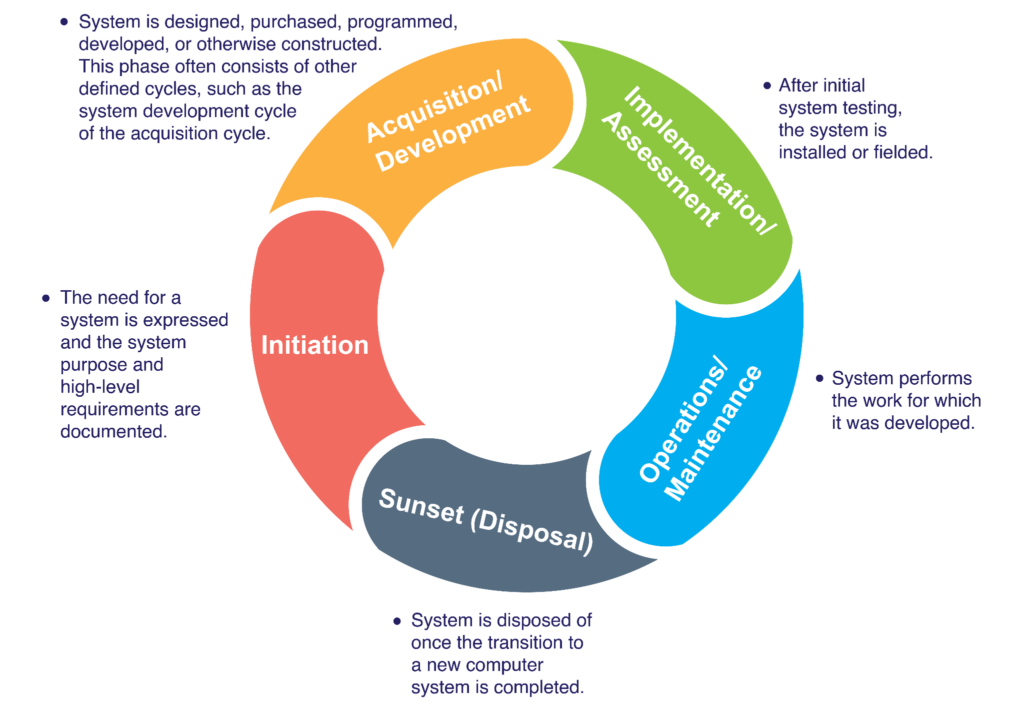
NIST CSF information protection system development life cycle (SDLC) (source)
The CSF then goes into conducting, maintaining, and testing backups of critical information and adhering to policies and regulations governing the physical operating environment—remember the importance of physical security to the Identity Management, Authentication and Access Control category above? From there, the category pivots to “future” activities. These may include developing a vulnerability management plan addressing the remediation of known vulnerabilities, continuously improving protection processes, sharing insights on the effectiveness of protection technologies and processes, and, finally, moving toward managing and testing incident response, business continuity, and disaster recovery plans.
Maintenance (PR.MA)
This category addresses not just the maintenance of organizational assets to ensure their availability but doing so in a secure manner that is comprehensively managed. Addressing both on-site and remote maintenance, this part of the CSF asks organizations to establish an approval process for maintenance that is reviewed, logged, and monitored. This must be done with organization-approved tools and methods to prevent any unauthorized access, tampering, or misconfiguration.
Protective Technology (PR.PT)
The final category in the Protect function consists of a sprinkling of other items discussed above in the CSF but focused on aligning some of the protective measures with approved policy. Crucial activities include controlling removable media, enforcing least functionality when configuring systems, and protecting communication and control networks. These are layered with audit and log records so the organization can continuously monitor the effectiveness of protective technologies and activities, establish resilience requirements, and set the organization up for success when it comes to the remaining functions.
Detect (DE)
The Detect function covers activities that are necessary to quickly identify cybersecurity events by finding anomalies, investigating events, and using thorough monitoring and detection. It includes three categories, which are described below.
| Category | Description of activities |
|---|---|
| Anomalies and Events (DE.AE) | Detect anomalous activity and understand the potential impact of cybersecurity events. |
| Security Continuous Monitoring (DE.CM) | Monitor and identify information assets and systems and verify the effectiveness of protective measures. |
| Detection Processes (DE.DP) | Maintain and test detection processes and procedures to ensure awareness of anomalous events. |
Anomalies and Events (DE.AE)
To properly detect anomalies and events, there must be a baseline of network operations and expected data flows for users and systems—otherwise, it is worse than trying to find a needle in a haystack when it comes to a potential cybersecurity incident. With the baseline established, your organization can begin collecting and correlating data, allowing the detection of anomalies and events. However, just collecting this data doesn’t do much; it must then be analyzed to determine the potential impact and measured against thresholds that enable the timely identification of incidents.
Security Continuous Monitoring DE.CM)
This category builds on the prior one, focusing on monitoring and detecting a variety of aspects of the organization for unauthorized personnel, connections, devices, and software. These include the network, physical environment, personnel activity, malicious code, third-party activity, and the overall environment itself.
Also included in this area is unauthorized mobile code. Some organizations take this to mean mobile devices, but this actually addresses scripts, macros, and other code elements that can be delivered to platforms. These can cause a serious headache for organizations and have become a focus for major tech providers.
Detection Processes (DE.DP)
The final category in the Detect function aims to wrap a layer of governance around the process of detecting cybersecurity incidents. It does this in part by ensuring that roles and responsibilities are clearly defined, understood, and communicated. From there, it makes sure your organization is testing detection processes—“How do we know if it’s working if it hasn’t been tested?”—and then communicating the detection of events, which opens the door to continuously improving those processes.
Respond (RS)
The Respond function focuses on activities related to quickly taking action when a cybersecurity incident occurs. It encompasses planning, communications, analysis, mitigation, and continuous improvement, as described below.
| Categories | Description |
|---|---|
| Response Planning (RS.RP) | Maintain and execute response processes and procedures to ensure appropriate action when cybersecurity incidents occur. |
| Communications (RS.CO) | Coordinate response activities with internal and external stakeholders. |
| Analysis (RS.AN) | Analyze incidents to ensure that response and recovery activities are supported. |
| Mitigation (RS.MI) | Perform activities to contain and resolve incidents. |
| Improvements (RS.IM) | Incorporate lessons learned from detection and response activities to improve organizational response activities. |
Response Planning (RS.RP)
This category has a single subcategory that focuses on ensuring that your organization executes a response plan during a cybersecurity incident. This is the culmination of the incident response (IR) subcategories addressed throughout the NIST CSF, ensuring that all of the documentation, accountability, and testing leads to a successful incident response by your organization.
Communications (RS.CO)
As the NIST CSF has demonstrated up to this point, communication is critical to the success of an organization, and this continues with the Respond function. This category covers a wide range of response communications, starting with personnel understanding what their roles are when a response is needed, reporting incidents when they occur according to established and known criteria, and sharing incident information in line with documented response plans. It also covers the all-too-important coordination of response plans with stakeholders. The final subcategory addresses voluntary information sharing, which includes membership in an Information Sharing Analysis Center (ISAC) specific to your organization’s industry as well as forums and outreach programs involving fellow organizations.
Analysis (RS.AN)
This includes analyzing and investigating cybersecurity incidents. Having an established network baseline makes this much easier because your organization can set up notifications to alert the appropriate personnel to investigate events promptly, determine the impact, categorize them according to the documented response plans, and provide the necessary foundation for forensics analysis of the incident.
Additionally, this category addresses the process of receiving, analyzing, and responding to vulnerabilities that are disclosed to the organization from internal and external sources such as internal testing teams, security bulletins, security researchers, and even bug bounty programs.
Mitigation (RS.MI)
This area covers the containment and mitigation of cybersecurity incidents to prevent an incident from expanding to other areas of your organization. Additionally, it builds on earlier mentions of vulnerabilities by ensuring that your organization conducts scanning and then performs mitigation activities.
Improvements (RS.IM)
Much like the prior category, this one is straight to the point: Make sure your organization is incorporating lessons learned into its response plans and that it continues to update response strategies as changes occur in the organization. Examples include major technology acquisitions/deprecations, changes to data centers (such as moving from on-premises to the cloud), and disaster recovery (DR) updates, just to name a few.
Recover (RC)
The Recover function is focused on activities that take place after an attack has been identified and dealt with. It is concerned with developing organizational resilience and organizational knowledge through recovery planning, improvement implementation, and high-quality communications.
| Category | Description of activities |
|---|---|
| Recovery Planning (RC.RP) | Maintain and execute recovery processes and procedures to ensure the restoration of systems and/or assets affected by cybersecurity incidents. |
| Improvements (RC.IM) | Improve recovery planning and processes by incorporating lessons learned. |
| Communications (RC.CO) | Coordinate restoration activities with internal and external stakeholders. |
Recovery Planning (RC.RP)
Just as the planning subcategory above, this category also consists of a single subcategory focused on the execution of a recovery plan. This may seem like a given, but it’s important that there be a documented and communicated recovery plan that enables your organization to quickly restore operations as efficiently and effectively as possible.
Improvements (RC.IM)
Like the category addressed in the Respond function, this is focused on incorporating lessons learned into your recovery plans and ensuring that recovery strategies are routinely updated as business and technology changes occur.
Communications (RC.CO)
It’s crucial to the future success of your organization to properly manage communications during and after a cybersecurity incident. Some organizations are better at this than others, and reputational damage is costly. However, it doesn’t need to be a long-term drag on the organization as long as proper public relations (PR) management is performed and recovery activities are communicated to all appropriate internal and external stakeholders.
Best practices to implement the NIST CSF
Consisting of 108 subcategories across 23 categories and five domains, implementing the NIST CSF is no cakewalk. With that said, the framework is meant to enable organizations to measure their cybersecurity programs and improve them. Here are some best practices your organization can follow that will make the adoption and implementation of the CSF a success:
- Ensure executive leadership engagement: Secure commitment and involvement from executive leadership to ensure successful framework adoption.
- Conduct a gap analysis: Evaluate current cybersecurity practices against the NIST CSF to identify areas for improvement.
- Prioritize actions: Use the results of the gap analysis to prioritize actions, focusing on high-impact, high-risk areas.
- Set a target profile: Set realistic goals for improving the organization based on the current NIST CSF assessment.
- Develop action plans: Develop detailed and achievable action plans, starting with higher-priority actions.
- Use an automation tool to discover IT assets and map them to applications: Identifying IT assets and associating them with individual applications for security and compliance management can be a daunting, endless, and incomplete effort, but it doesn’t have to be. With Device42’s Discovery, IT asset management, and dependency mapping capabilities, your environment can be discovered and updated in real time. From ports and MAC addresses to virtual machines, from network physical equipment to Linux OS versions.
Self-evaluation
There are a variety of ways to have your organization self-evaluate against the NIST CSF; the best approach really depends on what fits your organizational culture and approach to metrics. Here are a few ways to measure or “score” yourself against the CSF:
- Simple “Yes/No”: This is straightforward; your organization either addresses each subcategory, or it doesn’t.
- FILIPINI scale: This evaluation scale is used in the Cybersecurity Capability Maturity Model (C2M2) and adds some complexity because it requires your organization to score across four grades: fully implemented (FI), largely implemented (LI), partially implemented (PI), or not implemented (NI). While FI and NI are simple to establish criteria for, the other two are more shades of gray. Partially implemented should be considered if the organization performs some of the subcategories but has material gaps that need to be addressed. A subcategory can be considered largely implemented if your organization performs many of the activities in the subcategory but has some minor gaps that could be addressed.
- People, Process, and Technology: This is perhaps the most complex scale to use as your organization will consider the people, process, and technology (where relevant to the subcategory) to determine how well your organization is performing.
Updates to NIST CSF Categories
So far, this article has discussed the elements of NIST CSF v1.1, which was originally published in 2018. However, the publication of NIST CSF v2.0 is expected in early 2024.
The new version includes many changes. Some are simple, such as minor edits to the wording of subcategories to make them more understandable. The core structure of the framework still has the original five functions: Identify, Protect, Detect, Respond, and Recover. However, they are now wrapped in a “Govern” function to emphasize that governance is not just a one-off category, but instead, must be fully incorporated throughout your organization’s cybersecurity program. This function encompasses risk management, policies, procedures, roles, and responsibilities subcategories that were previously scattered throughout the other categories.
The changes are reflected in the new CSF image, as shown in the diagram below.
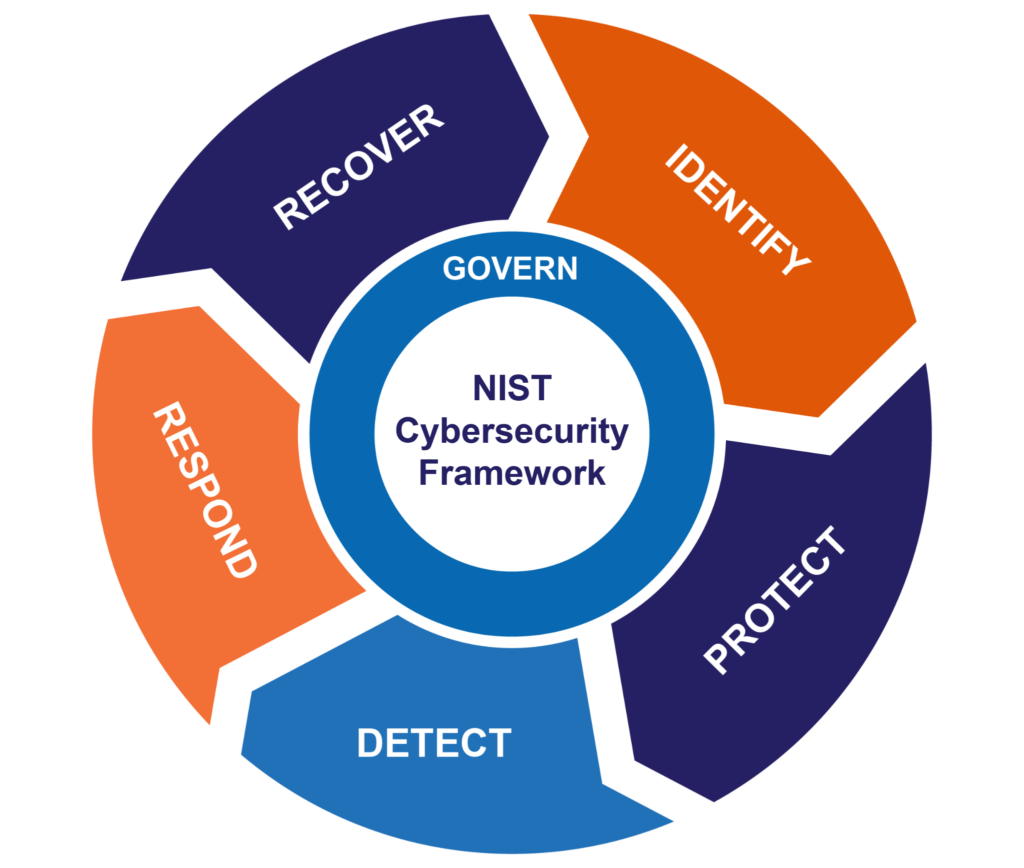
NIST CSF v2.0 (source)
The six functions and their new category descriptions are summarized in the sections and tables that follow.
There are additional material improvements expected in this new version to enhance the value and relevance of the CSF to organizations that adopt or already use it, including the following:
- An emphasis on how integral cybersecurity risk is to the organization’s enterprise risk management
- Integration of supply chain risk management into the organization’s overall cybersecurity risk management instead of treating it as a misunderstood outlier
- Acknowledgement of a quantitative approach to risk management
- Enhanced functionality of profile development by providing examples and templates
- Promotion of alignment with the NIST Privacy Framework
Another important update that greatly increases the practicality of the CSF involves the addition of implementation examples for subcategories, which eliminates some of the ambiguity in v1.1 when self-assessing your organization.
Governance (GV)
This new function focuses on establishing and monitoring the organization’s cybersecurity risk management strategy, expectations, and policy.
| Category | Description of activities |
|---|---|
| Organizational Context (GV.OC) | Understand the circumstances surrounding the organization’s cybersecurity risk management decisions (formerly category ID.BE in v1.1). |
| Risk Management Strategy (GV.RM) | Establish, communicate, and use the organization’s priorities, constraints, risk tolerance, and appetite statements and assumptions to support operational risk decisions. |
| Cybersecurity Supply Chain Risk Management (GV.SC) | Identify, establish, manage, monitor, and improve cyber supply chain risk management processes. |
| Roles, Responsibilities, and Authorities (GV.RR) | Establish and communicate cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement. |
| Policies, Processes, and Procedures (GV.PO) | Establish, communicate, and enforce organizational cybersecurity policies, processes, and procedures (formerly ID.GV-01 in v1.1). |
| Oversight (GV.OV) | Use the results of organization-wide cybersecurity risk management activities and performance to inform, improve, and adjust the risk management strategy. |
Identify (ID)
This category focuses on determining the current cybersecurity risk to the organization.
| Categories | Description of activities |
|---|---|
| Asset Management (ID.AM) | Understand the circumstances surrounding the organization’s cybersecurity risk management decisions (formerly category ID.BE in v1.1). |
| Risk Assessment (ID.RA) | Understand the cybersecurity risk to the organization, assets, and individuals. |
| Improvement (ID.IM) | Identify improvements to organizational cybersecurity risk management processes, procedures, and activities. |
Protect (PR)
As in the earlier version, this category deals with using safeguards to prevent or reduce cybersecurity risk.
| Categories | Description of activities |
|---|---|
| Identity Management, Authentication, and Access Control (PR.AA) | Limit access to physical and logical assets to authorized users, services, and hardware and manage the access commensurate with the assessed risk of unauthorized access. |
| Awareness and Training (PR.AT) | Understand the cybersecurity risk to the organization, assets, and individuals. |
| Information Protection Processes and Procedures (PR.IP) | Identify improvements to organizational cybersecurity risk management processes, procedures, and activities. |
| Platform Security (PR.PS) | Manage the hardware, software, and services of physical and virtual platforms consistent with the organization’s risk strategy to protect their confidentiality, integrity, and availability. |
| Technology Infrastructure Resilience (PR.IR) | Manage the security architectures with the organization’s risk strategy to protect asset confidentiality, integrity, and availability as well as organizational resilience. |
Detect (DE)
This function focuses on finding and analyzing possible cybersecurity attacks and compromises.
| Categories | Description of activities |
|---|---|
| Continuous Monitoring (DE.CM) | Monitor assets to find anomalies, indicators of compromise (IoC), and other potentially adverse events. |
| Adverse Event Analysis (DE.AE) | Analyze anomalies, IoCs, and other potentially adverse events to characterize the events and detect cybersecurity incidents. |
Respond (RS)
This function focuses on taking action when a cybersecurity incident is detected.
| Categories | Description |
|---|---|
| Incident Management (RS.MA) | Manage responses to detected cybersecurity incidents. |
| Incident Analysis (RS.AN) | Investigate cybersecurity incidents to ensure effective response and to support recovery activities. |
| Incident Response Reporting and Communication (RS.CO) | Coordinate response activities with internal and external stakeholders as required by laws, regulations, or policies. |
| Incident Mitigation (RS.MI) | Perform activities to prevent the expansion of an event and mitigate its effects. |
Recover (RC)
The Recover function focuses on restoring assets and operations impacted by a cybersecurity incident.
| Categories | Description |
|---|---|
| Incident Recovery Plan Execution (RC.RP) | Perform restoration activities to ensure the operational availability of systems and services affected by the cybersecurity incidents. |
| Incident Recovery Communication (RC.CO) | Coordinate restoration activities with internal and external parties. |
Conclusion
The NIST CSF v1.1 consists of 108 subcategories across 23 categories and five functions, which is changing to 106 subcategories, 21 categories, and six functions in v2.0. Compared to some other models and frameworks, this is a very manageable variety of objectives for any organization to take on in order to measure and improve its cybersecurity program.
The necessary practices avoid getting bogged down in technical speak and, instead, seek to address whether your organization is addressing a range of objectives. These include identifying what your organization has, protecting its assets, detecting cybersecurity incidents, responding to them, and completing the cycle by recovering and incorporating lessons learned from cybersecurity incidents.
The NIST CSF is flexible and can be tailored to the needs of organizations of any size, whether they are just getting started with their cybersecurity programs or have experienced and mature programs. With the release of v2.0, this framework will be even more practical and useful. For those organizations who decide to adopt the NIST CSF, it will be a worthwhile journey.