IT Asset Disposition Best Practices
All good things eventually come to an end, and in the IT asset lifecycle, organizations eventually have to replace IT systems. Over time, IT assets deliver less value than they once did. That’s why PC towers with floppy drives, fax machines, and CRT screens are no longer staples of modern corporate environments.
But getting rid of old IT assets is not as easy as dumping them in the garbage. The IT asset disposition (ITAD) process must take points such as financial accounting, information security, and environmental concerns into account.
IT asset disposition is the practice of securely retiring IT assets from active service through decommissioning and subsequent disposal. According to Globe Newswire, the global ITAD market continues to grow annually, and its size is projected to reach US$ 15.9 billion by 2027. Key trends that have led to IT asset disposition gaining importance in recent years include:
- Information security – The realization that IT assets hold valuable organizational data and as such IT asset disposition must consider how the data held is erased or prevented from falling into the wrong hands
- Data privacy – The growing awareness of individual rights regarding their personal information coupled with punitive penalties that have come with regulation and laws such as GDPR, HIPAA, PCI-DSS and many others. has meant that IT asset disposition practices must ensure personal data is protected since the risk is high at this juncture
- Sustainability – Movements like the United Nations (UN) Sustainable Development Goals and Green IT are raising awareness about the impact of technology on the environment including climate change. As such, IT asset disposition comes to the forefront due to the negative ecological effect that plastics, metals, and other materials could cause if the disposal is not done in a sustainable manner.
- Circular economy – Going hand-in-hand with sustainability, is the concept of the circular economy, which incentivizes the reuse, repair, and sharing of aged or unwanted IT assets over simply throwing them away. IT asset disposition provides options to lengthen the life of IT assets by extending their use through such means.
When it comes to technology, the scope is wide in IT asset disposition. Reasons organizations decide to retire IT assets include financial valuation, technology upgrades, vendor changes, and remote work requirements to name a few.
The approach differs with the type of technology. For example, a mobile device is treated differently than enterprise equipment such as servers or routers based on risk and value.
While IT asset disposition covers multiple domains, this article will focus mostly on data center asset disposition. We will look at the disposition journey in a lifecycle approach, addressing the key activities and considerations to meet business needs and address emerging IT asset disposition issues.
Key IT Asset Disposition Concepts
Imagine you have just been assigned a project to dispose of your organization’s IT assets for migration from a data center to the public cloud and need to have a blueprint for executing the project. What to do first? What not to forget? What tooling functionality is important?
This article will answer those questions by outlining the steps and key concepts to consider in your IT asset disposition journey. Let’s begin that process with a high-level overview of each step.
IT Asset Disposition Process Overview
| Step | Description |
|---|---|
| Disposition Planning | Business strategy provides a foundation for IT asset disposition. Organizations must consider the internal and external environment and bring together the resources required to execute disposition activities. |
| IT Asset Retrieval | Actually retiring assets begins with removing them from active service in a way that limits the impact on other services and components in the production environment. |
| Media Sanitization | Due to the huge risk of data loss and regulatory penalties, IT asset disposition practices must remove data from retrieved assets in a way that meets information security and data sanitization requirements. |
| IT Asset Disposal | This is the core IT asset disposition activity. In this step, organizations take the actions required to remove retired and sanitized IT assets from their environment completely. The actions in this step must align with the organization’s risk appetite and perspectives concerning the circular economy and sustainability. |
| Records Update and Reporting | Governance requires that the IT organization keeps records for audit and compliance requirements. Organizations should ensure due care is taken to track the activities of the previous steps and report their impact on the organization and the external environment. |
Disposition Planning
Failing to plan for IT asset disposition is a recipe for disaster. The strategic decision to migrate to the cloud does not diminish the financial value of assets held in a data center, even though the business case may indicate long-term savings by moving from a CAPEX to an OPEX model.
Because IT asset value is recorded in the balance sheet, a disposition plan and the organization’s asset management policies must consider it. The plan must also consider the organization’s strategy concerning sustainability and stakeholder needs.
A quality IT asset disposition plan will include:
- The sequence of steps in the IT asset disposition process
- Stakeholder roles and responsibilities
- Resources required
- Timelines
The plan should be shared with key stakeholders for buy-in before getting executive approval. This alignment is critical because the plan will directly impact business outcomes and financial records.
A risk assessment is a key component for IT asset disposition planning, as the potential for things to go wrong is high during data center decommissioning. Improper disposal of IT assets may lead to environmental pollution, regulatory penalties (for non-compliance to standards such as HIPAA, PCI-DSS, etc.), data breaches, and other adverse outcomes. A comprehensive data center assessment can help identify risks, analyze their probability, quantify their impact, prioritize them, and identify appropriate mitigations.
Planning should also consider engaging third-party organizations to conduct IT asset disposition activities. A formal contract should comprehensively address all relevant areas that protect the organization from the risks mentioned above if a third party is engaged.
Careful evaluation of potential providers includes considering aspects such as:
- Government licensing for handling and disposing of IT assets
- Relevant standards certifications such as ISO/IEC 27001:2013 for Information Security Management Systems and ISO 14001:2015 for Environmental management systems
- Security clearances from various government agencies for staff involved in the disposition activities
- Chain of custody processes and issuance of disposal certificates
- Track record, presence of relevant tools and resources, as well as references from similar organizations
IT Asset Retrieval
Once plans are in place, IT asset retrieval (a.k.a. decommissioning) is next. Risk assessments and sound change management practices ensure appropriate care is taken before IT assets are removed from the data center. A formal change request should be raised, evaluated, and authorized by relevant stakeholders.
Usually, organizations will conduct an audit by comparing what is in an IT asset register to the physical components within the rooms and racks. Due to the risk involved, a cross-functional team covering the different service and component domains should validate the information and then carry out the steps per the established deployment plan within the change request.
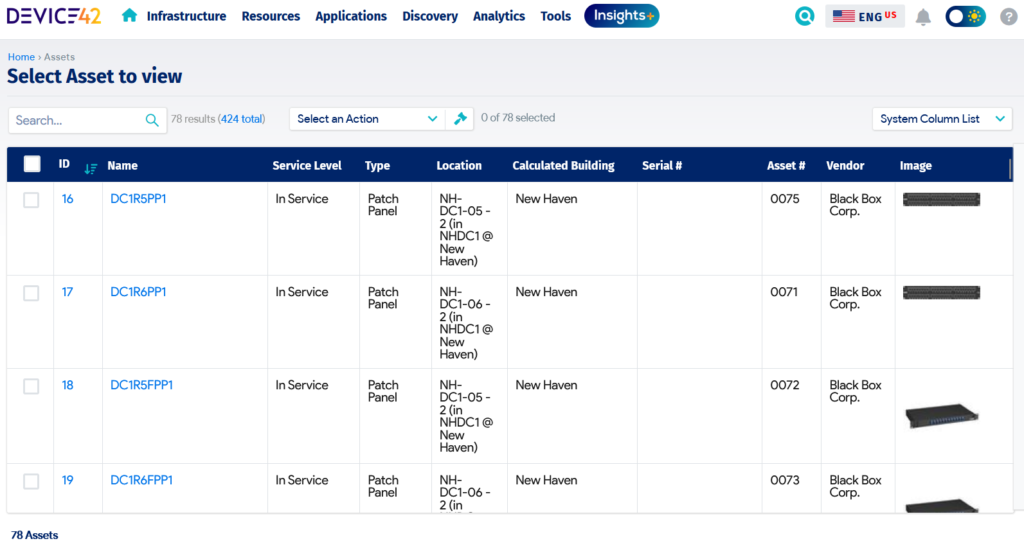
An asset register in Device42 details essential IT asset data.
The deployment management practice must be anchored on a risk-based approach to ensure that decommissioning and transfer of IT assets out of the IT Data Center is controlled. IT (or the third-party provider) should execute the deployment plan during off-peak hours to minimize disruptions to other production assets.
During the execution of the deployment plan, shutdown and relocation of active systems like servers and network equipment should be coordinated and controlled to prevent component damage and data loss. Finally, IT should move the decommissioned equipment to a secure staging area for transfer out of the data center.
Checks at the end of the deployment should confirm that:
- The plan was followed.
- The risks identified during the planning and change evaluation have been contained.
What about spares and software assets?
The IT asset retrieval process also inherently addresses the management of spare IT assets. Spares are cataloged and suited along with production assets.
Organizations must check vendor contracts for software assets, including cloud services, to see if they can reuse their licenses. If they can’t, the remaining option is to unsubscribe or cancel contracts.
Media Sanitization
To address the regulatory requirements related to information security and data privacy, data within decommissioned equipment should be comprehensively removed. This removal process is known as sanitization.
Sanitization prevents unauthorized data recovery once the equipment falls into the hands of a third party. In IT asset disposition, media sanitization can happen before, in parallel, or just after the IT asset retrieval activities.
The NIST SP 800-88 Rev. 1 Guidelines for Media Sanitization lists three categories of sanitization techniques:
- Clear – Applies logical techniques to sanitize target data in all user-addressable storage locations. This is the simplest method and involves overwriting the data or resetting the device. It is also the least secure as chances of retrieval through specialized tools remain.
- Purge – Applies physical or logical techniques that render target data recovery infeasible using state-of-the-art laboratory techniques such as overwrite, block erase, degaussing, and cryptographic erase. Purged data is significantly harder to retrieve than cleared data.
- Destroy – Renders target data recovery infeasible using state-of-the-art laboratory techniques like incineration, melting, shredding, disintegrating, and pulverizing. Destruction is permanent, modifies the physical state of assets, and is the best technique for risk-averse organizations. However, destruction may have environmental tradeoffs that are misaligned with the circular economy. For example, IT assets often cannot be recycled or reused after destruction.
An organization’s choice of sanitization technique will vary based on risk appetite, security categorization, cost-benefit analysis, and disposal arrangements. Follow-up audits and a verification certificate are required to ensure compliance when a third party performs sanitization.
IT Asset Disposal
Once sanitization is complete, the next step in IT asset disposition is disposal. The business context will determine what options an organization chooses for disposal. For leased IT, the available option is to return them to the vendor and cancel the maintenance contract. For assets the organization owns, options include:
- Resale – Organizations can resell their decommissioned data center IT assets to other organizations or individuals. Stakeholders should perform valuations to establish base prices that avoid significant losses.
- Donation – Organizations can donate data center IT assets to institutions such as charities and schools as part of corporate social responsibility. Some organizations may require recipients of the donations to sign a contract restricting their transfer or resale to any third party without the donor’s consent.
- Destruction – Organizations can have their data center IT assets destroyed. Most IT organizations cannot destroy assets in-house, so they often engage a third party. IT asset disposition providers are better suited to destroy IT assets while remaining compliant with e-waste regulations. In some of the most common destruction processes, providers break IT assets down into constituent materials (metal, plastics, rubber, etc.), then recycle them for reuse or shred and dump them. Providers usually issue a certificate of destruction to the organization.
Records Update and Reporting
Following the disposal, the last stage in IT asset disposition is records update and reporting. From a governance perspective, the IT asset register should be updated with data center asset status. The records should be available for future financial and compliance audits when required.
Apart from the IT asset register, other records that need updating include:
- Configuration items in the CMDB
- Vendor contracts for hardware maintenance
- Software license subscriptions
The organization should also store relevant IT asset disposition records from contracted vendors, including chain of custody and certificates of destruction.
In addition, governance expects reporting to management and stakeholders on IT asset disposition activity completion. The reports should include:
- Assurance that risks were adequately controlled
- Validation that the disposal followed appropriate regulations (sustainability reporting),
- Updates of IT asset values in the organization’s financial systems (ROI reporting)
- Lessons learned from the IT asset disposition for stakeholder review and continuous improvement
3 Tips For Effective IT Asset Dispositions
Given the information we’ve covered in this article, what are the top 3 tips to avoid common IT asset disposition mistakes? Our recommendations are
- Make planning a priority. Effective planning is a prerequisite for effective IT asset disposition. Alignment with business and IT strategy and consideration of stakeholder requirements concerning confidentiality and sustainability are key inputs before disposition activities begin.
- Continuously assess risk. Protecting the organization’s and their stakeholders’ information is paramount during disposition. So risks must be identified, analyzed, and evaluated before any decommissioning or disposal activities.
- Track progress and update records. The IT asset disposition journey has a lot of data points. Failure to track and update them can result in serious compliance issues or data breaches. The IT asset register should be the source of truth for all disposition activities.
In summary, all stakeholders involved in IT asset disposition must see the big picture from governance, risk, and compliance perspectives. With those perspectives in mind, organizations should take a strategic approach to ensure all stakeholder needs are met.