Transforming ITAM: The Role of IT Asset Tracking in Modern IT Management
The management of IT hardware and software as well as their associated data is a major challenge for digital enterprises, whether on-premises or in the cloud. Increasing complexity due to innovation and transformation initiatives, coupled with pressures to demonstrate more cost-effectiveness, are just some of the headaches that CTOs have to deal with daily.
According to a Deloitte survey, 90% of respondents believed that the rapidly changing business, regulatory, and technology environment is straining their efforts to enhance IT asset management (ITAM) maturity. IT asset management is the coordinated activity required to extract business and technical value from IT assets. To succeed in ITAM, a plan is required that specifies the activities, resources, and timelines necessary to achieve organizational objectives.
IT asset tracking is one of the activities within the ITAM plan that is fundamental to realizing value, especially where IT service management best practices are applicable. Tackling asset sprawl on a massive scale is no joke, yet the only way that value for money can be achieved is when the journey of each asset or group of assets is traceable across the IT asset lifecycle and status information is available for relevant ITSM processes when needed. IT asset tracking is the basis for optimal asset usage, effective asset maintenance, and proper asset disposal. Risks related to security, investment loss, and noncompliance are rife where IT asset tracking approaches are suboptimal.
This article explores a variety of techniques used in IT asset tracking. The scope includes IT asset tracking across the IT asset lifecycle but not tracking at the procurement level. The reader should expect technical guidance on techniques related to IT asset tracking, including benefits and challenges.
Summary of IT asset tracking techniques
The table below summarizes the five techniques to be considered in IT asset tracking that this article covers.
| Technique | Description |
|---|---|
| Manual tracking | Deployment of non-digital tags on IT assets, such as barcodes, that require physical scanning for tracking purposes |
| Tracking via discovery | Exploiting IT protocols to identify active IT assets on the network and populate their attributes in a CMDB |
| Tracking via GPS | Deployment of GPS receivers on IT assets to track their location via satellite terminals |
| Tracking via RFID | Deployment of passive radio tags on IT assets to transmit their information over a short distance |
| Tracking via IoT | Deployment of Internet of things (IoT) sensors on IT assets to transmit information over cellular and Internet networks |
Manual tracking
The most basic approach to IT asset tracking is a manual technique where physical methods are used to ascertain the location and status of IT assets after deployment. Paper records, spreadsheets, or simple databases are used as IT asset registers to record IT asset details such as make, model, serial number, assignee, or location. The asset is then assigned a physical tag having the organization’s name/logo and a unique identifier or barcode. This tag is usually secured to the asset using a permanent adhesive to prevent tampering.
To track IT assets manually, a physical audit is required, where staff go around the general location where the assets are kept and ascertain their current status. They then compare the information against the physical IT asset register and record any status variances. Where barcodes are in use, a barcode scanner can be deployed to read the IT asset tag, which would populate the information into an automated asset register. The operator can then add information on the status of the IT asset based on the visible status.
The main benefits for organizations of manually tracking IT assets are simplicity and cost-effectiveness.
Simple paper records can be deployed quickly for asset tracking. Where asset tags are required, they can be applied to the IT asset before it is assigned to users or deployed in a server room or data center.
Cost-effectiveness depends on scope. For example, an organization operating in one location and having 20-50 IT assets will experience minimal tracking costs since it only takes a few hours to audit the assets and determine their status. In contrast, the manual tracking approach is unsuitable for a large scope of IT assets or many assets located in multiple areas. Tracking large quantities of IT assets physically is time-consuming and inefficient.
In addition to scaling poorly, the manual technique is error-prone because incorrect information could be manually populated into the asset register. It also lacks any sort of real-time tracking capability since the organization can only ascertain the asset status during a physical audit.
Manual tracking is only suitable for certain IT asset types, such as hardware within a designated area. In addition, organizations that have invested in cloud assets cannot track them using this technique. Finally, another downside is that the IT asset register becomes outdated as soon as the asset has been deployed since the status changes during interactions in the live environment.
Tracking via discovery
The discovery technique is an automated approach to IT asset tracking that addresses most of the challenges encountered during manual tracking. This approach involves deploying IT systems that utilize protocols to identify networked IT assets and populate a configuration management database (CMDB). These discovery tools scan an enterprise network to gather information about IT assets such as IP addresses, manufacturers, versions, and configured device status.
Discovery tools employ two main ways to identify and track IT asset status: agent and agentless. The agent approach involves deploying specialized lightweight software in IT assets during initial configuration, which relays information to the discovery tool regarding device configuration and status. The agentless way does not require any software installation within the IT assets—the discovery tool directly polls the IT assets and gathers configured information.
Some of the common discovery protocols deployed by modern tools include the following:
- Ping sweep: This involves using the Internet Control Message Protocol (ICMP) to send packets (pings) to an IT asset to confirm that it is reachable on the network.
- SSH: This method uses the Secure Shell (SSH) protocol that exchanges device information on a Windows or Linux environment, such as operating system, make, model, BIOS information, CPU, drives, and installed software.
- WMI: The Windows Management Instrumentation (WMI) protocol retrieves information on Windows components, services, state, and installed software.
- SNMP: The Simple Network Management Protocol (SNMP) sends out queries using object identifiers (OIDs) to network IT assets. They respond with information that is maintained in a management information base (MIB), which is a formatted text file containing properties related to network devices.
- API: An application programming interface (API) enables communication between software elements, which is useful for discovering software components hosted across networks such as the Internet or in cloud environments.
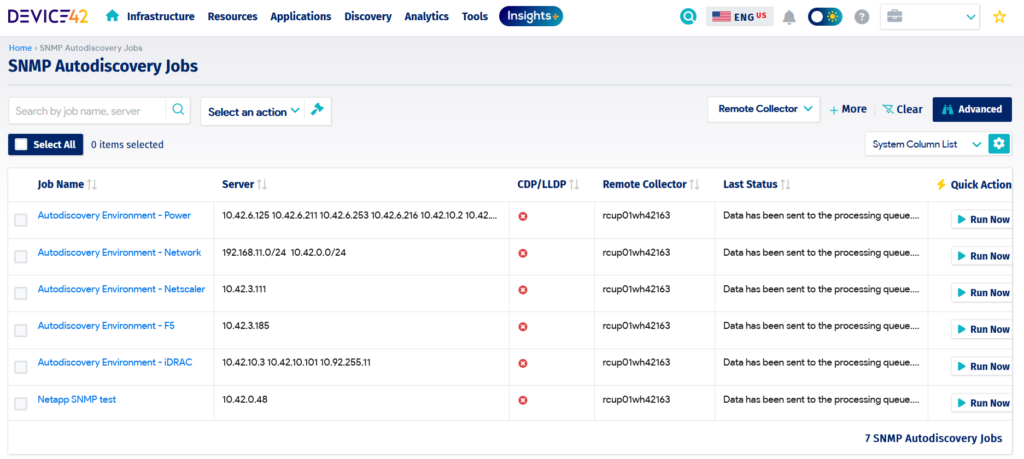
SNMP discovery configuration in a CMDB (source: Device42)
The main benefit of the discovery technique is its automated approach that gives near-real-time tracking capability. An organization’s confidence level in the status of its IT assets is highest when it can access current information within the CMDB.
In addition, the discovery approach is unlimited in terms of the number of IT asset devices that can be tracked and also covers complex hybrid environments, including on-premises and the cloud. A CMDB in IT asset discovery gives the added benefit of dependency information that enhances the value of IT asset tracking. This dependency information is invaluable while conducting change impact assessment and root cause analysis activities in IT service management.
The discovery technique is not without some limitations, though.
One of the challenges arising from discovery is that only active IT assets on the network can be discovered. If an asset is disconnected from the network, its status is unknown and cannot be tracked. This may include IT assets that are in storage or undergoing repair.
Organizations also incur significant costs in investing in appropriate discovery systems, which come with training and administration requirements. Where organizations adopt the agent discovery method, this comes with an overhead administrative effort in deploying software agents to all IT assets and ensuring that they are updated.
Finally, IT asset discovery has to be conducted regularly to prevent CMDB data from becoming stale and rendering IT asset tracking ineffective. The value of the CMDB to IT service management practices can only be extracted when the data reflects the current state of IT assets and their dependencies.
Tracking via GPS
Some IT assets are highly mobile and valuable and need to be tracked, especially when they are transported to important locations. These include containerized data centers, IT kits, and satellite devices. The Global Positioning System (GPS) is best suited to tracking these types of IT assets across the world.
As you may know, GPS is a 24/7 space-based radio navigation system that can pinpoint a three-dimensional position worldwide to meter-level accuracy and time to the 10-nanosecond level. The IT asset is embedded with a GPS receiver that communicates with the Global Navigation Satellite System (GNSS) network and, through a trilateration process using at least three satellites, determines its latitude, longitude, and elevation at a particular time. IT administrators are then able to access the location information through an online portal that has access to the GNSS information for their assets.
GPS tracking app screen (source: Google Play)
The main benefit to an organization from adopting GPS tracking for IT assets is the ability to locate the exact location anywhere in the world in real time. This is particularly handy for valuable IT assets where loss or theft can result in a significant negative impact. In addition, GPS receivers are designed for low power consumption, with modern devices consuming less than 25 mW in continuous tracking mode.
However, GPS tracking is mainly beneficial for a specific type of IT asset that is rare in typical IT functions. Most IT departments are not required to trace the exact locations of their IT assets, which are usually in fixed locations such as office buildings or data centers. Mobile devices such as laptops and cellphones are ordinarily assigned to an individual, so tracking simply involves asking the assignees for their exact locations.
Another limitation is that most IT assets are used indoors, while GPS is better suited to outdoor tracking. In addition, installing GPS trackers within IT assets may result in administrative overhead and compatibility challenges. Also, tracking cloud assets may prove impossible through GPS tracking, as these assets are generally inaccessible to IT administrators.
Tracking via RFID
Another technique that has become popular in the tracking of IT assets is using radio frequency identification (RFID) technology. RFID exploits electromagnetic fields to transmit information between IT systems that are near each other.
There are two main components of an RFID system:
- Readers: These are fixed or portable sensors whose antennas detect and communicate with RFID tags.
- Tags: These are small radio transponders attached to IT assets that respond to nearby reader devices and transmit preconfigured information.
There are two types of RFID tags: active and passive. Active tags have their own power source (usually a battery) and a long range of up to 150 m. They are also bigger, their cost is higher, and their usable life is a few years. Passive RFID tags do not have an internal power source, utilizing the reader’s radio signals to send information back to them. This gives them a short range of under 5 m but also makes them smaller and cheaper than active tags, and they have a long useful life of 20 years. Regardless of the type of tag, no direct line of sight is required for RFID readers to communicate with them.
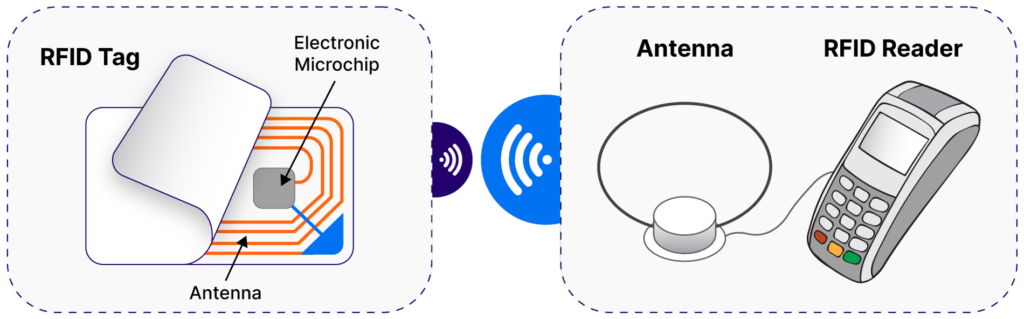
RFID components
IT asset tracking most often uses passive RFID tags, where no power is required. The tags are simply attached to the IT assets. Because these tags are lightweight and inexpensive, RFID tags have little administrative overhead.
However, deploying sensors can prove costly, especially where real-time tracking is necessary, since this requires many sensors to cover passive RFID tags over a single location. RFID is also prone to radio interference—multiple RFID tags operating in a small area can interfere with each other and cause collision issues. This technique is also unsuitable for tracking IT assets in a cloud environment due to a lack of access. Security is also a major concern for RFID because anyone with the appropriate sensor can capture information from passive tags.
Tracking via IoT
Another tracking technique that deploys electronic tags appended to IT assets is the Internet of Things (IoT). IoT leverages the Internet to establish network connectivity among physical devices with built-in sensors and gateways that communicate with little or no human interaction. IoT uses existing IT infrastructure such as cellular networks, Wi-fi, or Bluetooth to transfer information to IoT gateways or edge devices that collect data that is then transferred to the cloud for processing. IoT devices number in the billions because all modern devices are being designed and built as “smart” to take advantage of the ubiquity of the Internet. These devices can be configured to share information about their status, location, and usage.
The benefits of IoT tracking include real-time tracking and wide geographical range since devices can share their current status when connected from anywhere across the world. IT asset tracking information transfer options are also widespread, including Bluetooth and Wi-fi for short range and cellular networks for long range. Because no additional devices are required apart from the standard internet connectivity, IoT is seen as having a low environmental footprint and thus being more eco-friendly.
Some challenges exist with IoT as an IT asset tracking technique. It works with preconfigured smart devices, so this capability cannot be automatically extended to legacy systems. In addition, compatibility issues between IoT devices and IT asset management systems may complicate the transfer and processing of IT tracking information. This may be exacerbated by the IoT devices transmitting large amounts of complex data that can be difficult to manage. IoT works well in tracking on-premises IT assets but not those in cloud environments.
Tips for Choosing a Technique
Depending on the context, any of the listed IT asset tracking techniques, or a combination, may be well suited to a particular operating environment of an IT function. For example, smart IT assets may be labeled with barcodes and discovered using a CMDB solution. By considering all aspects—such as the number and type of assets, the scope of coverage (especially if the cloud is involved), and cost-benefit concerns—IT administrators can make an informed decision on what technique serves their situation effectively. Any change in asset tracking technique should be carefully managed, starting with a small scope that can be used to demonstrate value before an enterprise-wide deployment takes place.
Regardless of the technique selected, IT administrators should endeavor to make the IT asset tracking activity as close to real time as possible to assure the status information’s validity in supporting ITSM processes. While real-time location information may only be relevant where security is an issue, tracking IT asset status is more important, especially where a customer is at the end of the service being delivered. Investing in the right asset-tracking solution should translate into tangible asset management benefits, such as pinpointing overprovisioned or underutilized assets, redundant software, and data center power and thermal issues, all while providing insights into existing resources and usage.
Last thoughts
Only when IT asset records are accurate, updated, consistent, and aligned with other IT records does IT asset tracking generate full value for the enterprise from an IT service delivery perspective. The decision to adopt any IT asset tracking technique or a combination thereof has to be informed by business value and implemented to suit the operational context. The right tracking technique will ensure that the organization maximizes the return on its IT asset investments by facilitating the accurate forecasting of future needs, optimizing resource allocation, and ensuring smooth operations.