ITSM CMDB for Improved Service Delivery: A Practical Approach
As an IT environment evolves, its complexity level increases due to device proliferation, hybrid cloud adoption, and system integrations. In IT service management (ITSM), having a grasp of the state of critical components that underpin IT services is a vital capability that separates leaders from laggards. And that’s where a configuration management database (CMDB) comes into play.
A CMDB is a system or tool that supports configuration management by managing configuration item records throughout the IT service lifecycle. By maintaining accurate information on attributes and relationships between components that constitute IT services, the CMDB facilitates more accurate solution design, minimizes risk in change execution, and enables more effective technical support.
This article explores best practices in implementing and using a CMDB within ITSM processes. It provides practical insights on leveraging the CMDB to drive operational excellence in IT service management.
Key best practices for ITSM CMDB
Here is a summary of best practices to consider when deploying a CMDB to support ITSM processes.
| Best practice | Description |
|---|---|
| Leverage CMDB automated discovery | Deploy automated scans to capture all active IT assets into the CMDB. |
| Scope and map critical IT services as a priority | Use the CMDB mapping capability to visualize relationships and dependencies for critical services. |
| Deploy the CMDB as the single source of ITSM truth | Apply the CMDB as the main reference for incident and problem investigation and change impact analysis. |
| Provide CMDB access and training to key ITSM stakeholders | Empower stakeholders across the IT service lifecycle to maximize CMDB usage in ITSM processes. |
| Establish robust CMDB data quality verification mechanisms | Formalize regular auditing of the CMDB to ensure accurate and updated data. |
| Demonstrate CMDB value through ITSM goals and metrics | Report CMDB outcomes and benefits to entrench adoption and usage across IT. |
Leverage CMDB automated discovery
The foundation of a usable CMDB is the data it contains, which is determined by the scope of coverage that configuration management and other ITSM practices desire. Populating the CMDB with the attributes of and relationships between configuration items can be tedious and prone to error if carried out manually.
In a complex environment with a substantial number of IT systems, it makes sense to populate the CMDB automatically, and this is where device discovery comes to the fore. As a best practice, it is recommended that enterprise IT teams implement different automated discovery techniques to provide coverage for existing IT assets.
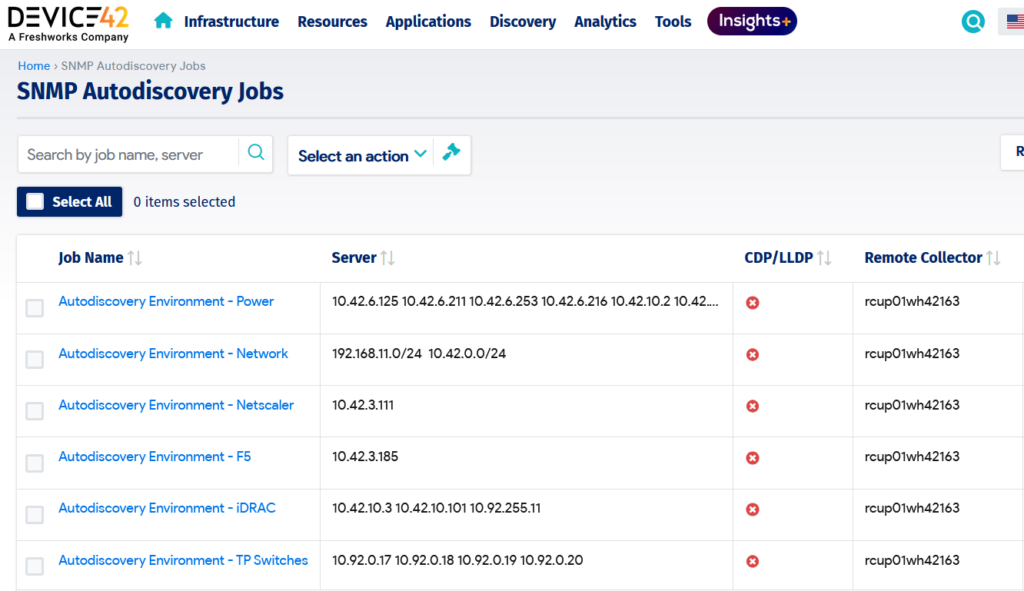
Autodiscovery configuration (source: Device42 Demo Platform)
Examples of CMDB discovery techniques include ICMP ping, reverse DNS lookup, SSH, WMI, SNMP, and IPMI. By deploying different methods, the CMDB attributes and their associated relationships can be comprehensively captured, ensuring that various CI categories in an environment are onboarded, such as virtual assets and installed software instances. Leveraging automated discovery is a no-brainer from the perspective of efficiency and effectiveness, which is the surest way to populate the CMDB with the correct information upon which ITSM practices depend.
In complex environments, the right CMDB solution enables the correlation of discovery data across multiple integrations to get a complete view of CI attributes. For medium-sized and large IT enterprises, it’s common to find hundreds or even thousands of IT components, including physical devices, storage volumes, containers, DevOps toolchains, and other virtual elements. In addition, different discovery techniques extract contrasting information, meaning that to obtain a complete view, there is a need to correlate this information. The CMDB serves as the platform for this very purpose, consolidating data across multiple integrations to provide that singular view that is relevant for IT service management.
While automated discovery is the recommended approach to populating the CMDB, verifying the capture of IT configuration changes is equally important. For example, if your discovery runs across a predefined IP range but then the infrastructure team makes changes to the network, it is likely that the new addresses will be outside the discovery scope. Regular auditing of CMDB configurations and validation through inspection to identify possible duplications, omissions, and inconsistencies can go a long way toward fine-tuning discovery to capture the true picture of the IT environment. To address this, configure a CMDB report that flags configuration items not rediscovered within a defined timeframe.
Scope and map critical IT services as a priority
In an ideal world, the CMDB can have visibility into every IT service and underlying component within an enterprise environment. However, due to IT sprawl and constant changes driven by business and technology needs, capturing everything may not prove to be valuable from both effort and cost perspectives.
Successful CMDB implementations are heavily focused on achieving a specific set of outcomes and benefits, so they track only the CIs that support these outcomes. Scoping of the configuration items to be populated in the CMDB should be informed by business needs and risk assessment information. By prioritizing IT services for CMDB onboarding, the IT function ensures that it excludes irrelevant configuration items, resulting in reduced administrative headaches and more optimal information to support ITSM practices.
Once the scoped configuration items are onboarded on the CMDB, the next logical step is to generate a map or topology of IT services based on how the underlying components interact. CMDB service mapping dynamically visualizes all the CIs in an IT service into a hierarchical model with the focal point being the elements that the end user consumes. By building the service map from a business point of view, IT administrators can capture a holistic picture of the underlying elements that contribute to functionality and performance, such as authentication, licenses, applications, and associated data sources.
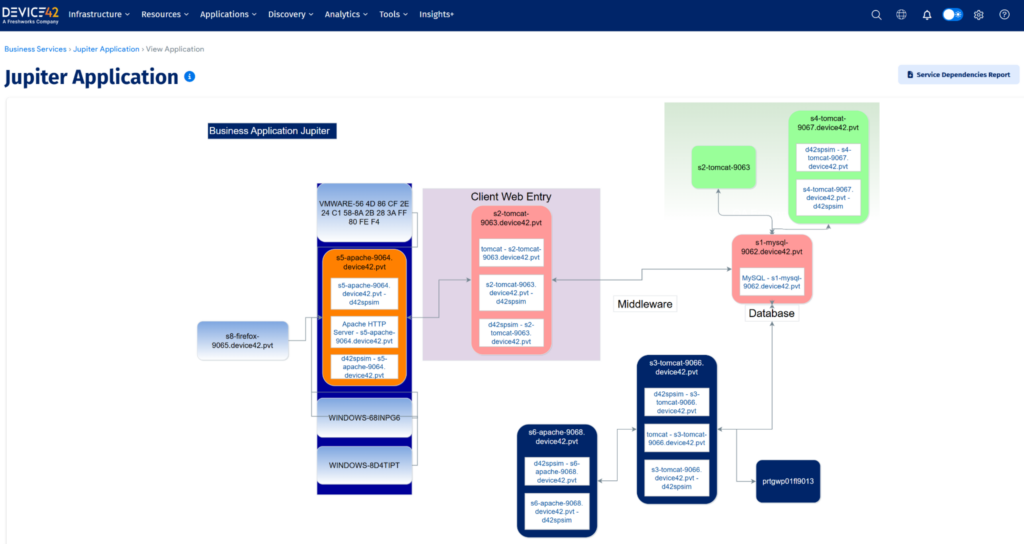
Sample CMDB service map (source: Device42 Demo Platform)
CMDB business service maps are a rich source of information that facilitates effective ITSM practices. The visualization of interconnections and dependencies can make a big difference in solution design, change planning, and troubleshooting investigations among a host of activities. For this reason, the accuracy of CMDB service maps plays a big role in their adoption and trust by ITSM stakeholders.
It is advisable for IT administrators to regularly review and update service maps based on stakeholder feedback. This is critical whenever changes to the IT environment have taken place, as validation information provides insights into the true state of IT configurations. Both positive and negative feedback should be welcomed in equal measure since the value of the CMDB is fully realized when the data is put to use throughout the IT service lifecycle.
Deploy the CMDB as the single source of ITSM truth
After the CMDB has been populated per the agreed scope, service maps generated, and the information verified as accurate, the next logical step is to ensure that ITSM stakeholders extract value from it by referencing the CMDB as the “single source of ITSM truth.” This does not mean that no other truth exists outside the CMDB regarding configuration item attributes and relationships but rather that a well-scoped and validated CMDB should be the first reference point for ITSM practitioners. This arrangement ensures speed in decision-making during critical periods such as incident investigation and change planning. It also provides room for additional information picked directly from the components themselves, monitoring tools, third parties, and other sources to be used for cross-referencing the state of the IT environment.
The CMDB should be deployed as the primary reference for conducting impact analysis during the evaluation of change requests. The ITIL 4 change enablement practice guide states that it is important to control the unintended negative outcomes from changes, such as service degradation and unhappy users. Adverse impacts can come from limited visibility on dependent systems or unpredictable effects from cascading events. The CMDB becomes a useful resource in impact analysis by helping change planners simulate the change effects on dependent configuration items, which informs the risk profile, approval actions, as well as scheduling and communication requirements.
During incident and problem investigations, speed is the most critical measure of how an IT team is rated by customers. Responding to and resolving incidents quickly based on SLAs requires the assigned teams to have the right information on the source of the service disruption and the related components that have been affected. CMDB service maps shed light on the investigation activities by providing up-to-date information on IT service configurations and visualization of dependencies, which can speed up triage activities, enrich swarming, and enhance root cause analysis, translating to more effective resolution actions.
While the aforementioned ITSM practices are the most common use cases for deriving value from the CMDB, other practices are also beneficiaries of a properly configured and validated CMDB. IT teams can use the CMDB to support IT audits and other compliance activities such as asset lifecycle tracking, cybersecurity control implementation, and service architecture and design reviews. Any ITSM practice where impact analysis, cost allocation, risk analysis, availability planning, or cause-and-effect analysis are required will benefit greatly from a highly functional CMDB.
Provide CMDB access and training to key ITSM stakeholders
Gatekeeping access to the CMDB is an obstacle to the extraction of its maximum value in service delivery. A deliberate approach to providing access and training for ITSM practitioners can go a long way in raising the effectiveness of service management practices. Whenever CMDB service maps are exposed to relevant ITSM stakeholders, they appreciate their value from the standpoint of informing decisions that affect the IT service lifecycle. It is prudent that teams involved in all areas of service management be trained on how to use the CMDB to query information on attributes, relationships, and dependencies so that when the need arises, they are well-equipped to harness it.
In addition to training, IT teams can document use cases of leveraging the CMDB in solution design, impact analysis, and root cause analysis. By creating knowledge articles or videos that highlight success stories, CMDB administrators can both educate ITSM practitioners and influence the uptake of CMDB querying in all relevant practices. Testimonials from subject matter experts on different service value stream activities that have benefited from the CMDB can be a great motivator for other IT staff members to join the bandwagon.
IT teams who are interested in the CMDB data but want to harness it on their terms (i.e., their preferred tools of trade) may find that it makes sense to configure the CMDB to make its data accessible to other IT solutions such as asset tracking systems, analytics dashboards, monitoring systems, and collaborative tools. With generative AI becoming the go-to option for querying and analyzing enterprise data, API integration can lead to a more user-friendly interaction with CMDB data. The more the CMDB data is made readily available to ITSM practitioners, the greater the chances of developing a culture of adoption and utilization in day-to-day activities.
Establish robust CMDB data quality verification mechanisms
The characteristics that greatly influence the adoption of the CMDB within the IT enterprise are completeness and accuracy. Data quality in configuration management systems plays a major role in building trust and encouraging usage among IT staff. For this reason, data quality metrics should be defined, tracked, reported, and reviewed by key stakeholders. Examples of CMDB data quality metrics defined under the COBIT 2019 Configuration Management objective include:
- Percentage of the accuracy of configuration baselines of a service, application, or infrastructure
- Frequency of changes/updates to the configuration item repository (CMDB)
- Number of discrepancies relating to incomplete or missing configuration information
The importance of involving ITSM stakeholders in maximizing the value of the CMDB cannot be understated: It is only when CMDB data is used in decision-making that benefits are realized. Service outages, lost productivity, and costly overruns due to inaccurate configuration information leave a bad taste in the mouths of IT staff, resulting in a negative perception of the CMDB. For this reason, stakeholder satisfaction with the CMDB data quality should be monitored, and feedback on data accuracy and completeness improvements should be incorporated where possible.
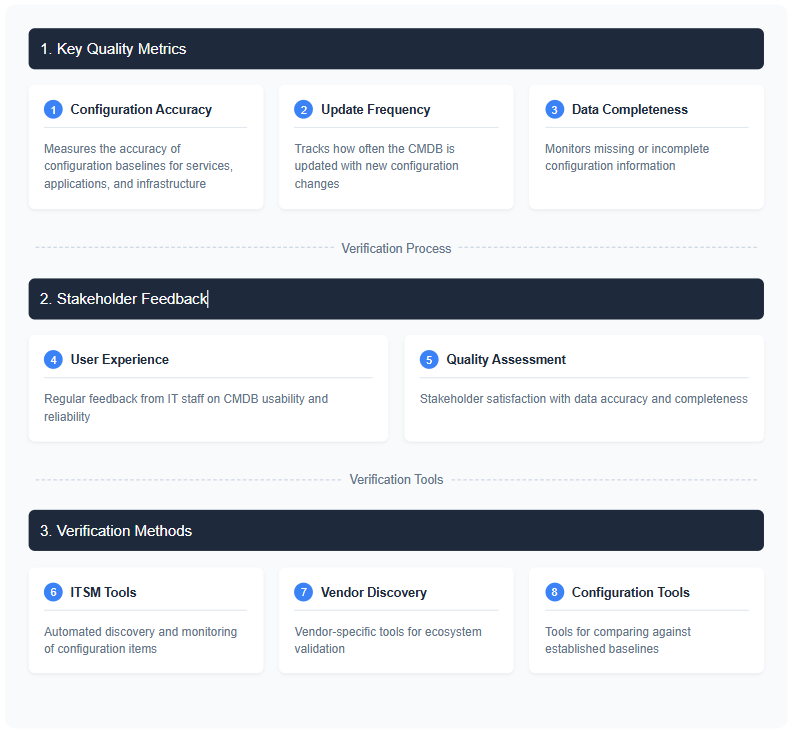
Components of CMDB data quality verification as a process map
Additional measures to enhance CMDB data quality validation include regular verification by comparing its information with that contained in existing ITSM monitoring and configuration tools. These tools come with discovery functionality, so they can act as a reference point to validate the CMDB information. Vendor tools, in particular, can capture a subset of the IT ecosystem, which can then be compared with a CMDB baseline and deviations addressed.
Demonstrate CMDB value through ITSM goals and metrics
Finally, the outcomes that the CMDB supports and the associated benefits should be demonstrated to ITSM and business stakeholders. Apart from the earlier mentioned metrics, stakeholder satisfaction with the CMDB should be regularly tracked and reported. This should be directly linked with achieved business objectives such as improved service availability, performance, cost efficiency, or compliance resulting from configuration management information usage.
It is also prudent for other ITSM process owners to track CMDB value from their perspective. Key performance indicators, such as change success rate and timely incident resolution, can be enriched with attribution to the role that the CMDB played. The completeness, correctness, and trustworthiness of CMDB data should be reported in the context of how IT services and processes have benefited from them in meeting organizational goals and enhancing customer satisfaction.
Last thoughts
As a governance function, the configuration management practice is mainly concerned with supporting operational excellence. The CMDB facilitates this by tracking the attributes and relationships of IT services and their underlying components. ITSM practices thrive in an environment where the CMDB is comprehensively and accurately populated, it is trusted by stakeholders, and its capabilities are exploited fully. By adopting the best practices described in this article, organizations can benefit greatly in generating value from their CMDB investments through quality IT services and happier customers.