Case Study
- AppDirect
- Back to Business with HBC
- Covenant Health
- Coventry University
- Coventry University Revisited
- Deep Insight for AWS Migration
- DELL / EMC
- Disaster Recovery
- Gainesville Regional Utilities (GRU)
- Gravity R&D
- Imperial College London
- Integrating Several Legacy IT Departments
- International Financial Services Provider
- Large Car Manufacturer
- Large Regional Bank
- Large U.S. Based Hospital System
- LeasePlan, AWS and Device42
- LINZ — Land Information New Zealand
- Maxihost Datacenter Ltd.
- MergeIT
- Migrating 40,000 Servers to a Private Cloud
- Netcetera Group Ag.
- SoftBank Corp.
- TP ICAP
- World’s Largest Virtualization Company
Device42 Evaluation by MergeIT
Introduction
MergeIT is a managed service provider with a proven history of deploying and supporting complex on-premises and cloud infrastructure. We’re continually investing our time and resources into making our internal processes as efficient as possible, using the latest technologies.
We have been evaluating Device42 software to incorporate it into our customer onboarding process and management.
To evaluate Device42 we deployed Device42 to manage two data center environments for two businesses (we will call them business A and business B) and conducted a test of Device42 across both environments.
The following report will cover the evaluation methodology and testing results.
About The Testing Environments
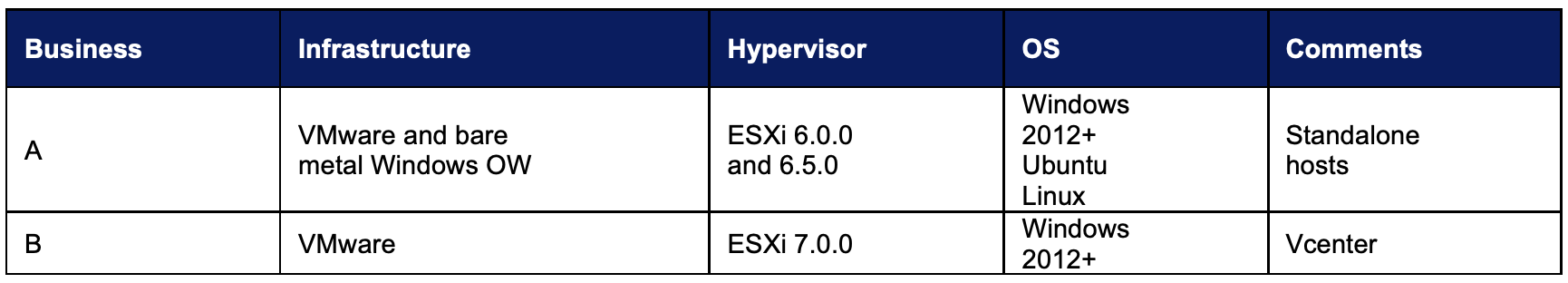
Business A is a well-established financial services company working within the recruitment industry. As such their focus is on having highly available IT systems with an emphasis on leveraging Device42 for uptime as well as governance, risk, and compliance.
Most recently Business A has asked us to take over full support of their in-house IT infrastructure.
The task at hand was a challenging one as the organization has next to no documentation of their IT infrastructure.
Another challenge was the time constraints, as we had been given 1 month to onboard this customer into our MSP service rather than the usual 2-3 months.
Business B is a travel and insurance company, managing a number of educational and travel programs centered on cultural exchange.
Business B is currently struggling with aging infrastructure, and we are tasked to help them during the transition period, to identify the resources that are at risk and require a refresh and update.
Testing Environment by Each Customer
Customer Challenge & Use Cases
Managing the Infrastructure: In one of the customer environments, the team had trouble with business-critical applications running awfully slow. It had affected the other VM’s on the hosts as well. They needed a way to get the visibility and dependency views of their critical applications to identify the issues and resolve them.
Maintaining compliance with security standards: One of the major challenges another business had was concerning security, as they use some business-critical applications like Sage and Credit Hound since they are a financial services company. When it comes to running a financial services company, being compliant and following strict security measures is critical and lack of it could lead to vulnerabilities.
Resource Utilization and Application Dependency: One customer was challenged with planning for capacity. They used Spreadsheets to track physical devices, but this did not allow them to get a detailed room, rack, or device visualization necessary for proper capacity planning. There was no application dependency map or network map that could be used for remediation and/or migration planning. There was a software inventory, but it was exceedingly difficult to get an up-to-date view of what software was running on what machines and what was authorized and unauthorized.
Customer Needs
Given three main issues across both customers, which were Infrastructure management, governance and compliance, resource utilization and application dependencies, and based on our professional experiences we quickly recognized that we need to approach this challenge in a new and different way.
Recognizing that these issues could only affect these companies even more as they grow, they needed a solution that can automate the inventory process and reduce or cut the manual effort. With respect to the market standards, we had to take a security based, IT operational efficiency approach to the product evaluation.
Understanding the infrastructure via Discovery Scans: For Business A, one of the root causes for business-critical applications like Sage and Credit Hound was the old infrastructure which was unable to support the applications seamlessly. This was brought into light by Device42 as it determined that the infrastructure was old and was low on space on most of the hosts through the discovery scans available. This made way for an added server to host and manage applications that are not business critical. Device42 helped document the IT infrastructure quickly, and the auto-discovery helped to keep that information up to date.
Meet CIS Security Control requirements: As mentioned earlier, as all the companies needed to be compliant and in line with security measures. Business A is no less interested in the these and would be up to date with the security standards outlined in CIS’ (Center for Internet Security) controls with a security-first mindset. This was a must for a winning solution.
Resource Utilization and Application Dependency: Device42’s Resource Utilization gathers statistics on a machine’s disk, network I/O, CPU, and memory utilization over time. One of the key functionalities of Device42 is up-to-date user data on the device and getting clear recommendations for sizing or right-sizing existing workloads for AWS, Azure, Google (GCP), Oracle, and VMWare Cloud on Amazon Web Services (AWS).
Application Dependency Mapping (ADM) capabilities enable Device42 to auto-discover application dependencies and service dependencies on a deeper level across the entire network. Device42 offered Application dependency diagrams visualizing application-to- device relationships. Map of applications to servers, servers to switch ports, and users to devices and applications, were provided.
Why We Decided to Look at Device42
At MergeIT we’re always looking for a solution of the highest possible standards to help us with challenges of efficient data center management (DCIM) and operational maturity.
The IT industry has a very long and not very glorious tradition of using weird and wonderful solutions to some problems we cause ourselves. Especially when it comes to monitoring and managing IT infrastructure. Google alone has about 344,000,000 search results for “server monitoring” phrase. All of these tools do a very good job looking at a very small part of the IT picture.
We, however, are on a constant lookout for something that would bring everything together. We think we’ve found exactly these two things in a gem that is Device42. And we have decided to road test it in our favorite way – using real life scenarios in a live environment. The Device42 Main Appliance (MA) is the kickoff point for all the discovery and
insights that will proliferate through the environment. It is a pre-configured virtual appliance (built on Linux) that is hosted by the end customer, enabling full protection under the client’s data center security architecture and policies.
During our first “soft onboarding” process, covering circa 140 points around end user software, printers, servers etc. we’ve discovered multiple, difficult to name infrastructure issues. Mainly around inter server connectivity and performance.
As mentioned before, end to end onboarding of a customer this size and complexity usually takes us 1 month with additional 1-2 months of discovering the “unknown- unknows”.
Thanks to Device42 we have been able to show 3 major infrastructure issues (Server age and part issues) and prevented them even during onboarding.
Fair to say, Device42 is here to stay and will be used as a part of our onboarding and support process.
Deploying & Using Device42
Deployment:
Device42 can, and in our case was, deployed by a 1st line engineer. And we feel we could as well stop here… is that simple!
Business A Deployment Process:
Business A had given a remote machine with domain credentials on the network for MergeIT to be able to login to the hosts and deploy Device42 MA. We were given access to a couple of ESXi hosts. ESXi1nd Holodeck, ESXi 2 is the main server, about having the main domain controller and Payroll and accounts servers. Payroll is used heavily for Processing Day to day and file storage of secure docs. Then Holodeck is running Sage and Credit hound. Plus, a VM for Spindle which is a program to send Pay slips and invoices.
We downloaded the Device42 Virtual appliance, converted the .Ovf file from the decompressed virtual appliance to .Ova file which is almost 18GB to be able to deploy using the vSphere client onto the hosts. We deployed it on both the hosts ESXi 1and Holodeck to start with and then gave the space as per the minimum Resource Configurations setup by Device42.
Device42 main appliance for a small to medium environments (<2500K Devices) requires 4 vCPU’s, 16GB RAM and 100GB vDisk. Whereas the Remote Collector needs 2 vCPU’s, 4GB RAM and 20GB vDisk.
The Device42 Main Appliance (MA) is the kickoff point for all the discovery and insights that will proliferate through the environment. It is a pre-configured virtual appliance (built on Linux) that is hosted by the end customer, enabling full protection under the client’s data center security architecture and policies.
Once the Main Appliance is deployed onto the host and powered on, we accessed the console using Username: device42, password: *******. Configured the IP address (Use a STATIC IP for all production Device42 VMs to avoid connectivity issues) followed by the proper NTP server and time zone. Once the configuration is finished, we logged into the web interface using https:// IP-address and user: admin password: *******.
Remote Collector Configuration:
Once the Main Appliance had been successfully deployed and accessed, we downloaded and installed the Device42 Remote Collector (RC) onto the remote machine and then deployed it onto the hosts ESXi 1 and Holodeck. We logged into the console using the default username. Configured the network settings to start with and a static IP, as D42 can lose contact with an RC with a changing (dynamic) IP address. We connected the RC to Device 42 via port 443, that is via the RC setup from the main console. Here we have used the IP address of the Main Appliance and the OTP generated from the Device42 admin web interface. After the first registration on port 443, all later communication occurs over a secure WebSocket channel between RC and MA.
Installing the Windows Discovery Service (WDS):
Once the RC and MA are configured, we then downloaded the Device42 WDS, ran the Device42 Discovery installer and pointed it to the Main Appliance or the RC endpoint using the RC IP and the OTP from the Device42 admin page. Accept the default installation directory for the WDS service and confirmed installation. Remote collectors in the Device42 UI should now be renamed to reflect that the WDS has been set up and connected, and the WDS Service indicator icon will be ‘green’, showing a WDS is connected and communicating
Business B Deployment Process:
Deployment for business B was even easier as we could deploy OVA template directly onto the hypervisor, without a need for converting it.
This was because Business B is using more up to date version of the ESXi software.
Using Device42:
Once the above steps are completed, Device42 is accessible in just a couple of steps. We head to the IP address of the main appliance from our browser and then log in with the default username or password. Once logged in, all the functions and features are on the admin page to be able to use.
Device42 discovers and connects all the IT assets into a single repository. It pulls data from physical servers, hypervisors, cloud, network devices, applications, and more, plus from external tools such as puppet, Chef, and able to receive data via Rest APIs.
Automated and built-in technology supplies cleansing, deduplication, and enriching of the data. Plus, automatic and intelligent mapping, visualization, event triggers, analytics, and more.
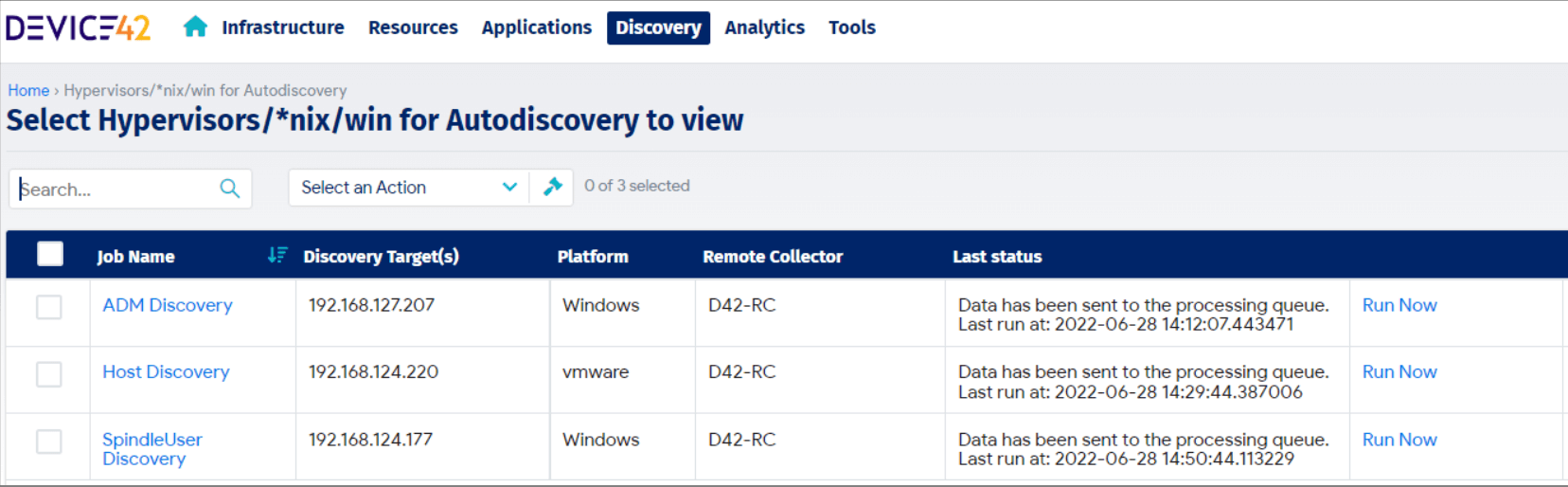
How It Works:
The Device42 Windows Discovery Service (WDS) is a lightweight service designed to allow Windows auto discovery jobs to be created and managed from the main Device42 appliance. The WDS only needs to be installed on a single Windows machine in the environment and will need access to WMI on any of the target machines.
Key Findings & Conclusion
Device42 is here to stay. It is a time saver and in a couple of cases also a lifesaver!
In both cases, Business A and Business B benefited tremendously from using Device42 as it gives us and internal IT teams an excellent insight into how the systems are configured and working together.
Often, we’re faced with IT systems that have organically grown over several years (and several IT managers) with zero or very limited documentation.
I’m tempted to say that now with Device42 we ALMOST don’t need documentation anymore as Device42 provides near real-time ongoing visibility.
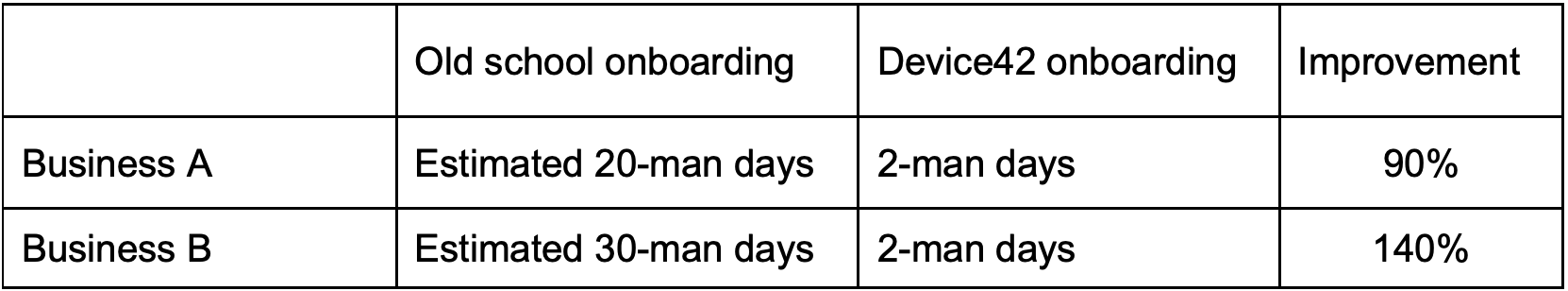
We’re estimating that Device42 is saving us a significant amount of man-days during initial contact with a new customer as well as managing their operations.
We were able to move 2 members of the service team to perform another job which saved us significant amount of time and resources.
We find it extremely useful in two major parts of our everyday life.
Customer Infrastructure Discovery & Onboarding:
The key metrics is that we were able to discovery and onboard a customer with a complex environment in a matter of days! And while there are many more metrics we could quote, the two major ones for us are:
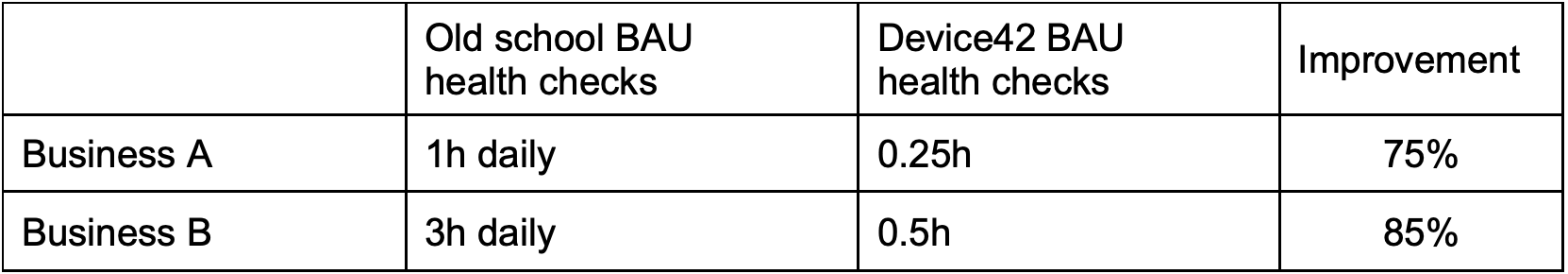
IT Operations & DCIM
-
-
Discovery tasks can be run on a schedule so you can stop playing catch-up.
-
Discovery can be also extremely useful when troubleshooting any minor or major system issues as it changes the narrative from “we think how these 2 servers talk to each other” to “we know exactly…”
-
Auditing is no longer a giant undertaking to find a ‘point in time’ state of the
infrastructure, since continuous compliance can be achieved
-
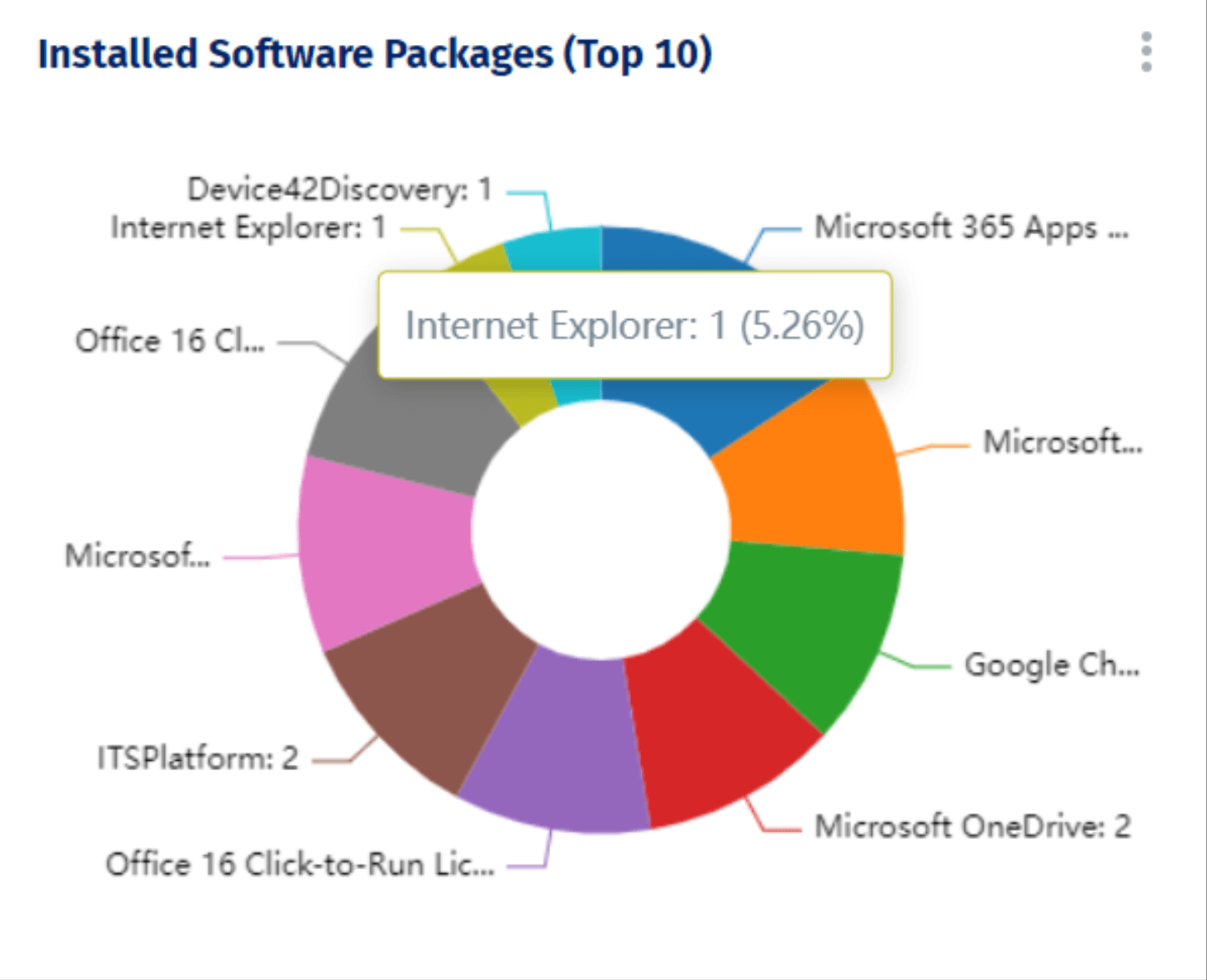
Figure 2 – Installed software widgets help quickly identify potential vulnerabilities
- 1. Less manual entry, reduced investment of time & labour, and fewer errors. 2 team members moved from operational to other more beneficial roles!
- 2. Brilliant network visibility including network changes
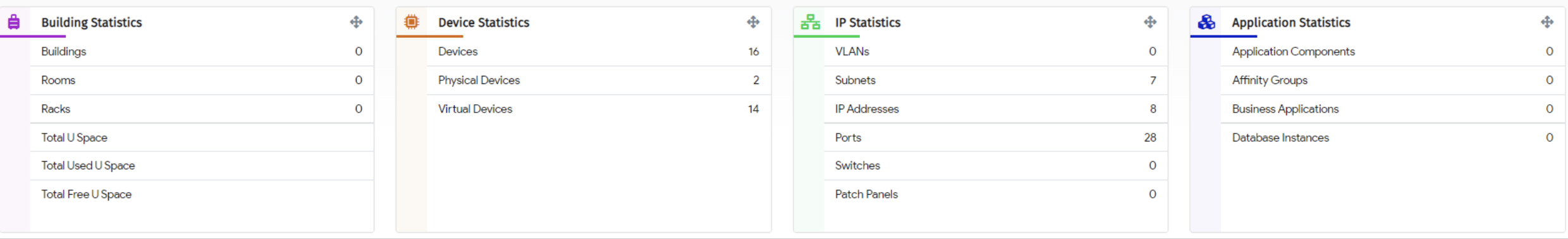
Figure 3 – Building, Device and network statistics help with Data Centre capacity planning
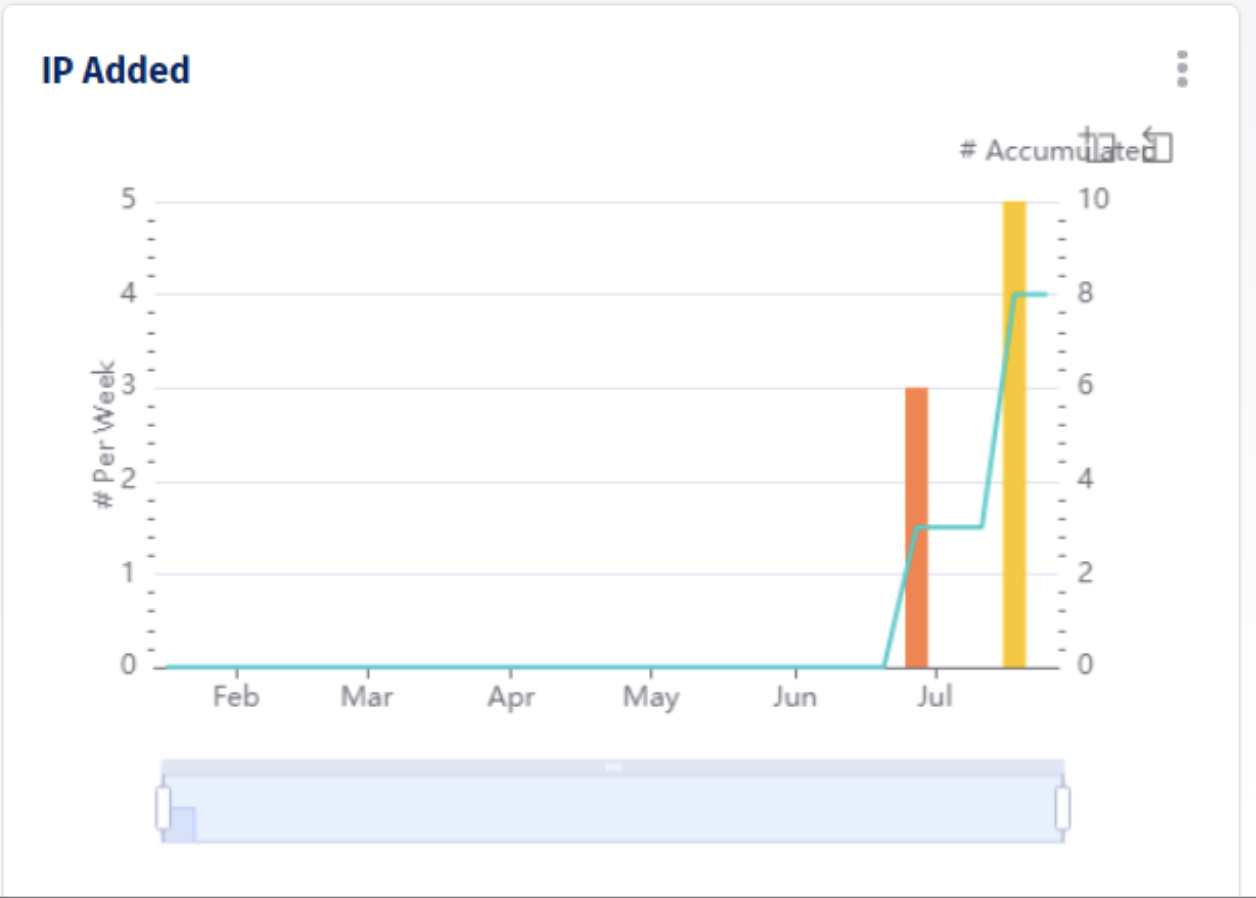
Figure 4 – Unique approach that helps identify “Shadow IT” that just “appears” on your network
Automatically see all application dependencies and communication paths.
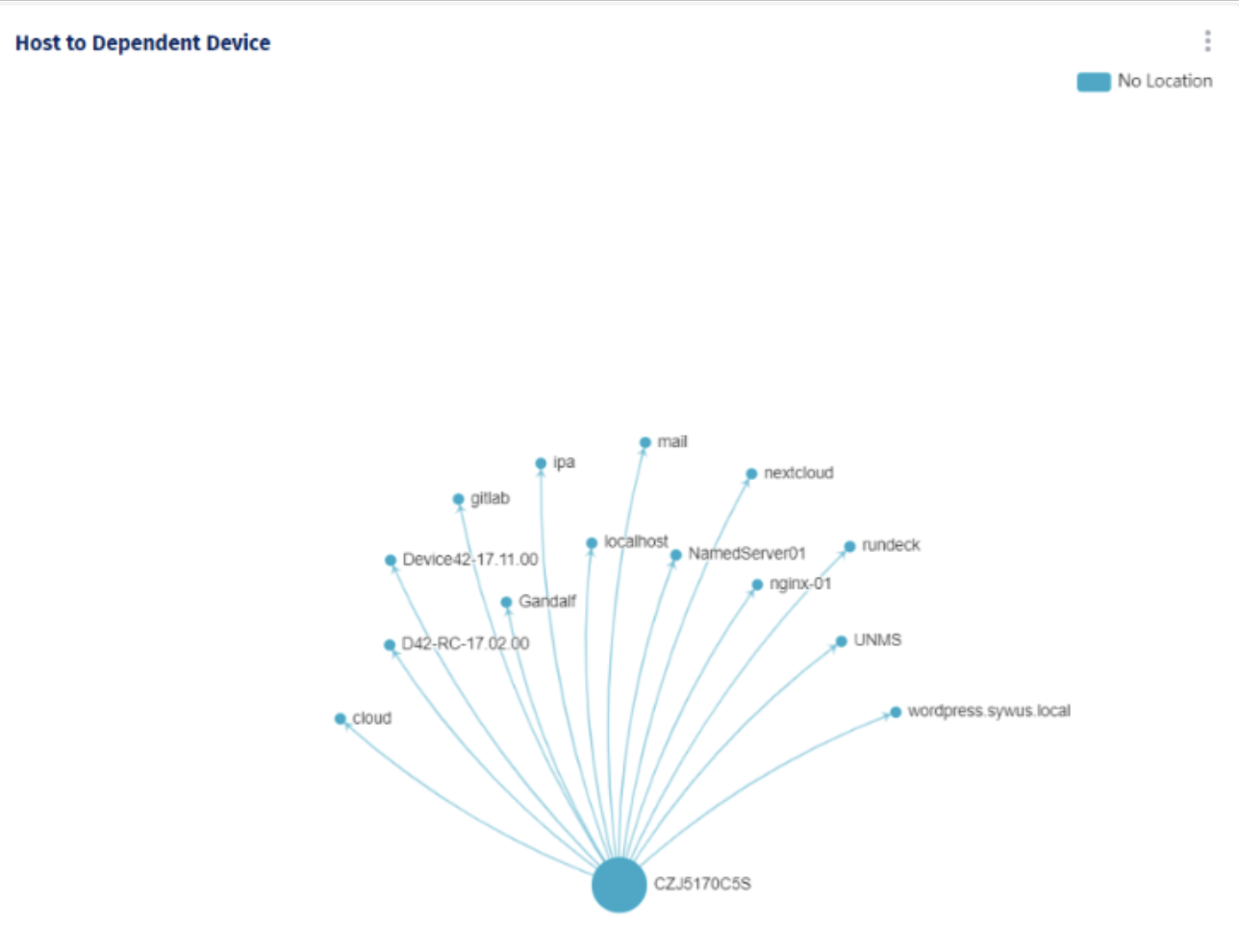
Figure 5- Best feature we’ve seen is the application dependency mapping
1. Agentless discovery uses native protocols, with optional agents available.
2. Visualizes application to device relationships. Maps applications to servers, servers to switch ports, and users to devices and applications.
3. Dynamically generated impact charts help reduce risk and potential downtime during cutovers, upgrades, and migrations by understanding application interdependencies and connections.
4. Automatically discovers application components such as Oracle, Postgres, MySQL, MongoDB, and IIS.
5. Supplies detailed configuration discovery for major applications such as Oracle, Microsoft SQL, MongoDB, PostgreSQL, MySQL, ColdFusion, IIS, Apache, and more.
I am giving it 10 out of 5 stars to Device42. First 5 for discovering significant issues with our customer’s environment even as the tool was being deployed. Another 5 for helping us convince the customer to act now.
—Chris Kopec, Managing Director at Merge IT
Device42 is the starting point for all the discovery and insights that will proliferate through the environment. It is a pre-configured virtual appliance (built on Linux) that is hosted by the end customer, enabling full protection under the client’s data centre security architecture and policies.
—Chaitanya Majeti – Service team leader at Merge IT