CMDB Business Service Mapping
From change planning to incident resolution, configuration audit or vulnerability treatment, the ability to understand how individual IT components and configurations come together to underpin the technology services is a critical capability. Even though most IT organizations agree about this, many struggle to put in place resources and governance elements to make this a reality. For any IT service provider, whether internal to an organization or as a 3rd party service provider, value to business and users requires functionality and performance that meets agreed requirements and service levels. That can only happen if the service provider has visibility of all the underlying components and associated dependencies.
This visibility challenge is the problem CMDB business service mapping solves. CMDB business service mapping dynamically visualizes all the configuration items (CIs) in a business service into a hierarchical model.
A user’s reference point for accessing a business service is an application. As such, a business service map may include multiple applications. And multiple business service maps may reference a single application.
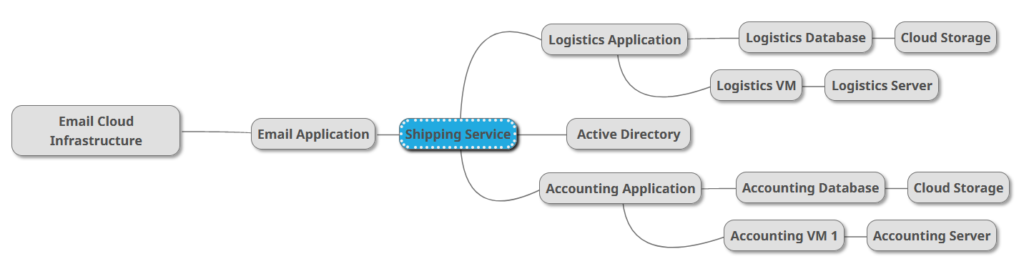
A shipping business service map displays the applications and servers in an email workflow.
This article will explore CMDB business service mapping in detail, including common techniques and use cases.
CMDB Business Service Mapping Uses The Customer’s Perspective
CMDB business service mapping techniques are similar to application mapping. The key difference is that the initial identification of the service is not tied to applications, but rather the business user’s perspective.
While application service mapping details service dependencies and components from a technical perspective, CMDB business service mapping defines a service from all dimensions.
For example, a customer relationship management (CRM) business service may be based on a CRM application and underlying databases and infrastructure, but that is only part of the overall business service. It may also require authentication systems, active vendor support contracts, and licenses. A business service map captures all of this information to provide holistic visibility.
Organizations obtain the customer perspective through a consultative engagement with the business owners who represent service users and product/service managers who represent the service provider. Service identification is based on the outcomes and the naming conventions that the users have adopted to identify a service. With this information, the associated applications and underlying infrastructure can be referenced.
An example of how the applications mapped to a business service are visualized is shown below.
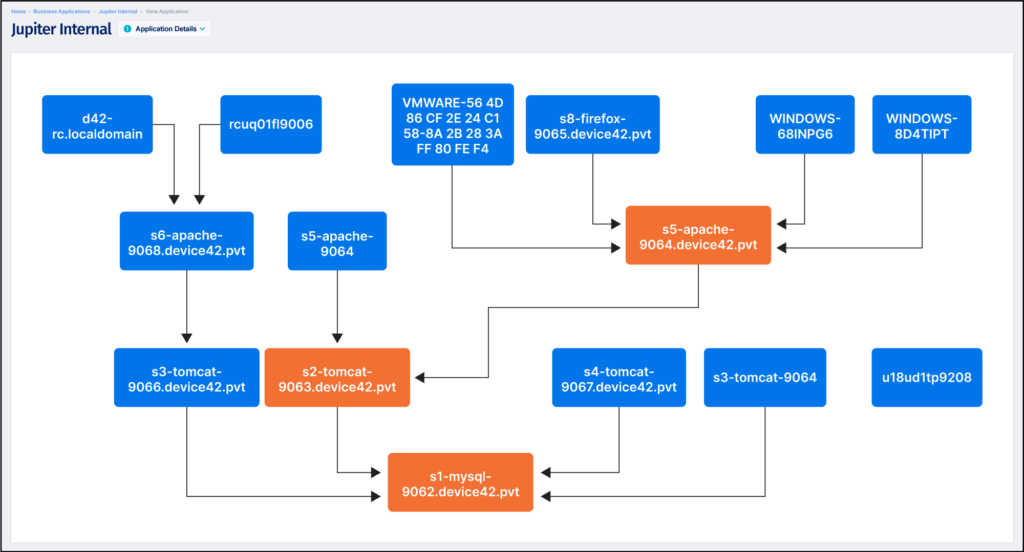
Underlying software applications supporting a business service.
CMDB Business Service Mapping Techniques
A summary of the techniques used for CMDB business service mapping — which are similar to application mapping — are listed below:
CMDB Business Service Mapping Techniques
| Service Mapping Technique | Description |
|---|---|
| Agentless | Agentless techniques involve accessing the host and executing commands to gather information on open ports and running processes or services. A CMDB solution can do this using a central or distributed approach. Agentless mapping techniques often require access that might be restricted due to information security controls. |
| Agent-based | Agent-based techniques involve Installing a lightweight program in each host to read configuration files and gather information on running processes or services. While this option offers more information than the agentless technique, it requires installation in each component associated with the business service. Installing and maintaining agents across a network often requires significant effort in itself. |
| NMAP | NMAP is a network mapper program to inspect raw IP packet headers to discover hosts, running services, open ports, operating systems, and other information. NMAP is lightweight, extensive and free, but being a command line utility, it has a steep learning curve. |
| NetFlow | NetFlow is a protocol that captures groups of IP packets using a collector to analyze network traffic and identify flow information, including ports and services. NetFlow has the advantage of being accessible in most firewalls and provides information that is useful for network monitoring, capacity planning, and security analysis. However, it may impact device performance due to bandwidth needs. |
| API | RESTful API requests and responses help retrieve application-layer information from endpoints. APIs have the benefit of seamless integration with other applications and services, and are easy to maintain. However, functionality is limited and they may pose a security risk if not effectively configured. |
| Packet capture | Network packet capture tools collect detailed information within the entire payload about hosts, services, and operating systems. Packet sniffers provide the greatest level of detail in network traffic, but are limited in customization or extension. |
| Tagging | Tagging involves capturing information added to public cloud assets by administrators as free-form key-value pairs that can contain CI information. While tags are recommended, it is important to use a standardized approach. Without uniform tagging standards, information might not effectively support the business service map. |
CMDB Business Service Mapping Approach
CMDB business service mapping takes a top-down approach by first identifying the business service with stakeholders. The steps can be summarized as follows:
- Identify the business service– Use available information from service catalogs and interviews with business/service owners to identify the business service. This step requires leadership commitment to drive the initiative and full participation by all involved.
- Determine business service priorities– Use input from business and technology stakeholders by reviewing strategy and business impact analysis information. Prioritization is often a delicate matter as conflicting objectives can arise when multiple parties with different opinions control services and components.
- Start with one or two critical business services– Don’t map all your business services at once. Instead, choose one or two and identify the main applications required to enable the service. Trying to map all services will likely result in bottlenecks and resource challenges. An agile approach helps gain buy-in by demonstrating value quickly.
- Perform CMDB application discovery and mapping– The mapping techniques listed earlier help you to capture additional information to support the map. For example, CMDB application discovery and mapping can help identify responsible parties, criticality, service levels, recovery time objectives, information security requirements, etc.
- Review and update maps regularly– Don’t let maps get stale. Perform regular updates based on information from technology subject matter experts who support the associated applications and underlying components. This requires discipline and ownership. Otherwise, you risklosing credibility and future support for mapping initiatives.
- Expose the service maps to all stakeholders– Providing stakeholders with access to the maps helps to maximize overall value. The more the business service maps are used, the higher the chance of positive outcomes.
CMDB Business Service Mapping Use Cases
Business service mapping has value beyond just visualizing the underlying components required to enable business outcomes. Many service management practices will reference service maps to support the entire service lifecycle and champion improvements to meet stakeholder needs, including compliance requirements.
The table below details common use cases for CMDB business service mapping.
CMDB Business Service Mapping Use Cases
| ITSM Practice | Benefits provided by CMDB business service mapping |
|---|---|
| Service Design | Business service mapping is a key input for stakeholders involved in service design as it outlines what applications and infrastructure can be reused to support new or changed services. |
| Change Enablement | While planning for changes to business services, the business service map serves as a good reference point when identifying the impacts and risks that could materialize. |
| Service Catalog | The service catalog becomes a more detailed description of service offerings when paired with an updated business service map. |
| Incident Management | Information on applications and dependent components can shorten the time to resolve incidents and facilitate communication with affected users and stakeholders. |
| Problem Management | Business service maps can be a useful reference point for identifying root causes in underlying applications and infrastructure components. |
| Service Level Management | When discussing service level requirements and targets, a business service map provides a vital reference point for promoting understanding and consensus. |
| Service Continuity | Business service maps within a well-established CMDB can serve as a reference for identifying the areas of the organization that are most likely to be negatively impacted by disruption to IT infrastructure. |
| Information Security | Identifying risks and planning associated controls can be greatly enhanced when reference information such as business service maps are available and updated within a CMDB solution. |
Recommendations For CMDB Business Service Mapping
A business service map is only useful when all stakeholders actively use it. As such, it is essential to market the capability and regularly audit the maps to ensure they are fit for use in service delivery practices. Service maps should be owned and managed just like other CIs; otherwise, they risk becoming obsolete.
Standardizing the approach to business service mapping also builds validity and buy-in from everyone involved in service delivery. A common approach to naming notation, as well as recommended mapping and relationships that are embedded in the CMDB, provides a basis to support business needs and operational excellence in service management. Frameworks like the Common Service Data Model (CSDM 3.0) and the TBM Taxonomy are valuable references.
Should organizations map every business service?
It’s tempting to believe that you should create a map for every business service. However, the effort required to build and maintain CMDB business service maps is significant. Organizations should define business needs and service criticality to determine which services require mapping. The best option is an agile approach that builds CMDB business service maps for high-priority services.
Conclusion
CMDB business service mapping delivers significant service management value. Identifying and mapping business services enhances performance, aligns business and technology needs, and drives strategic and operational improvement.
Maintaining business service maps requires commitment from all stakeholders. The maps should be supported by a robust CMDB solution that can capture all underlying components and provide the rich visualization and analytical capabilities necessary to support service delivery.




