NIST 800-37: Implementation & Best Practices
Two issues constantly pose challenges for organizations both big and small: risk and compliance. Each passing day provides more challenges to organizations as they navigate the information space while maintaining focus on supporting their businesses, especially mission-critical functions, and this is no different for federal agencies and the organizations that support them. This is where the NIST 800-37 Risk Management Framework (RMF) comes into play.
Any organization can use the RMF, but those that support the federal government and handle government data in any way must comply with the RMF regarding privacy and security risks that could impact the federal government and its data. The RMF works best when used in conjunction with other resources to provide a solid blueprint for managing the security and privacy risks of information systems, such as:
- FIPS 199: Standards for Security Categorization of Federal Information and Information Systems
- FIPS 200: Minimum Security Requirements for Federal Information and Information Systems
- NIST SP 800-53
- Other NIST guidelines
The NIST RMF is a great framework to use for several reasons:
- It facilitates the discussion of system-level risk and its impact on the enterprise’s essential functions.
- It integrates security and privacy requirements into other critical areas of the business.
- It streamlines the risk management process lifecycle.
This article describes the seven steps of the NIST 800-37 RMF and provides relevant best practices for success.
Summary of the NIST 800-37 RMF Steps and Best Practices
The NIST 800-37 RMF is made up of seven steps, as shown in the diagram below.
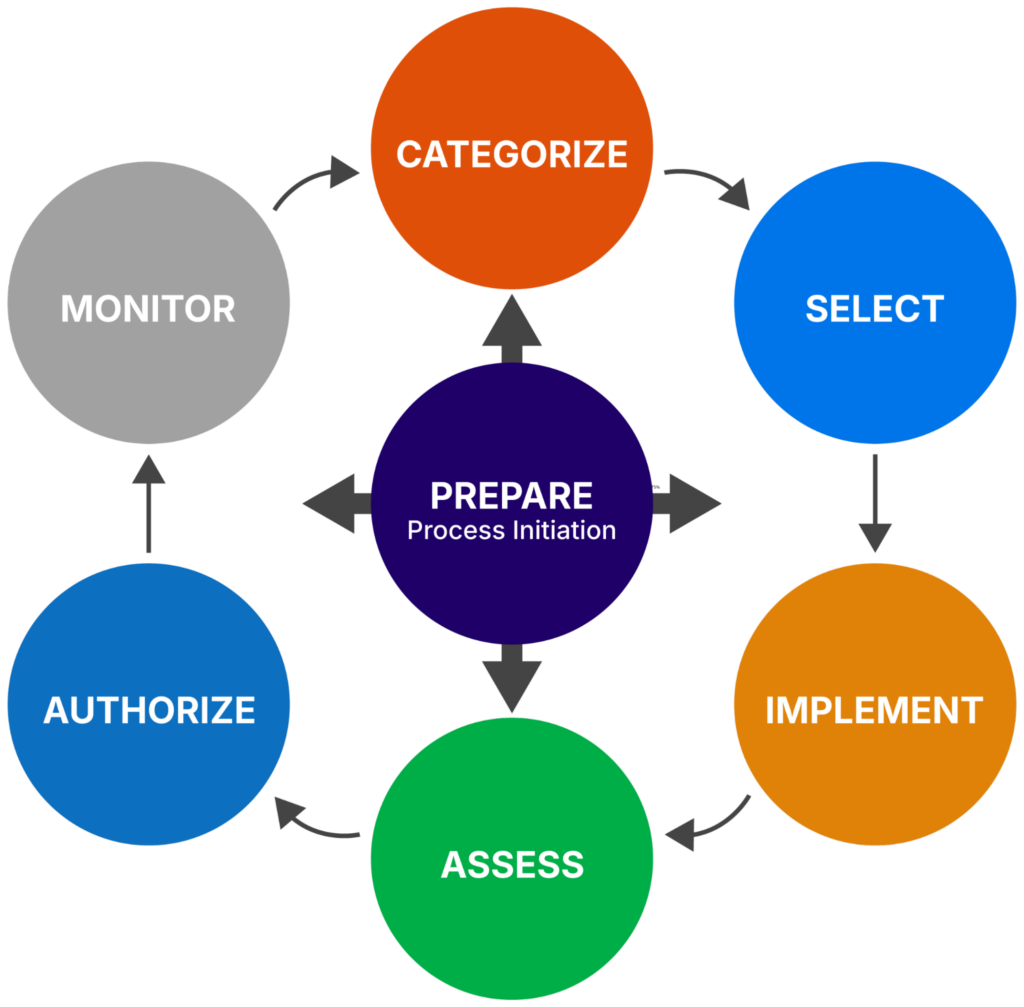
Risk Management Framework (source)
Without further context, these seven steps can seem confusing for the uninitiated. Here is a quick summary of each.
| RMF step | Description |
|---|---|
| Prepare | Establish a strong foundation for managing security and privacy risk. |
| Categorize | Identify the data your systems are processing, transmitting, and storing. |
| Select | Identify controls to reduce the risk to your systems, using a risk-based approach. |
| Implement | Configure the previously selected controls in your environment. |
| Assess | Perform an assessment of the effectiveness of the implemented controls. |
| Authorize | Authorize the systems to operate on the basis of risk acceptance. |
| Monitor | Continuously track the security and privacy of the systems and their controls. |
Step 1: Prepare
The adage says that “proper planning prevents poor performance,” and in the case of implementing and complying with the requirements of the RMF, it firmly applies. This step was added to NIST SP800-37r2 upon its release in December 2018.
Although identified as the first stage of the RMF process, Prepare is a step intended to be performed both before and throughout the process as a means of building the organization’s foundational security and privacy risk management strategy and essential activities, without which the rest of the RMF would be quite difficult to implement.
There are several key activities of the ‘Prepare’ step:
- Identification of key roles and stakeholders
- Identification of mission- and/or business-essential functions
- Establishment of an organizational risk management strategy
- Development of risk assessments for the organization and systems
- Identification of common controls
- Identification of information types processed, stored, and transmitted by the systems
- Development of a continuous monitoring strategy
Essentially, the Prepare step is used for the organization to build the main infrastructure that the rest of the RMF relies on to assist implementation and achieve
compliance. As such, it is critical to communicate with key stakeholders from the very beginning of the process at both the organization level and the system level. These discussions will look slightly different between the two levels because one involves a higher-level view of security and privacy risk, while the other dives into the individual systems that support the organization’s mission/business-critical functions.
Another item to consider when performing the Prepare step (and the RMF as a whole) is to use existing resources, policies, processes, and data when building out the key structure. Most organizations have pre-existing knowledge and processes that should provide key pieces of the puzzle when implementing the RMF.
Step 2: Categorize
This step focuses on identifying the sensitivity and criticality of the information and systems being assessed, which is necessary for determining the appropriate level of protection (i.e., security controls) required. The categorization process is performed in support of the organization’s mission and business objectives, linking them with the confidentiality, integrity, and availability (CIA) of the systems and the data being processed. While some organizations can do this through a manual data collection effort, it is best optimized by using an automated solution focusing on IT asset management, change management, and dependency mapping to identify and manage the information systems and data they process.
The Categorize step involves several key activities:
- Documenting the primary characteristics and information of the system, such as the system owner, technical description, purpose, etc.
- Categorizing the systems based on FIPS 200, Minimum Security Requirements for Federal Information and Information Systems
- Approval of the systems categorization, which is critical to conducting the selection of controls in the next step
The primary output of the Categorize step is a detailed security categorization that serves as the basis for selecting and implementing controls in subsequent steps of the RMF. This categorization is critical because it ensures that the organization’s resources are allocated effectively, focusing on systems and corresponding data with the highest impact on mission and business objectives that can be adversely impacted by any loss of confidentiality, integrity, or availability (CIA).
A crucial part of the Categorize step is determining the information types being processed, stored, and transmitted by the information system. Some examples of information types may be classified government information, customer data, and intellectual property such as trade secrets and patents. Impact levels are assigned for each of the three CIA security objectives that help guide the selection of cost-effective security controls that should be aligned with the organization’s risk strategy.
While effective communication with stakeholders across the organization is essential during the Categorize step, the activities required to implement it successfully are best addressed by system stakeholders such as the system owner (SO), information system security officer (ISSO), and business owner (BO) of the systems.
Step 3: Select
With the security categorization of the information system completed, the next step is to select controls based on the system categorization. This step is focused on identifying, tailoring, and documenting the security and privacy controls necessary to protect the system based on its categorization. These controls are selected from NIST Special Publication 800-53, which provides a comprehensive catalog of security and privacy controls.
Key activities within the Select step include:
- Reviewing and selecting the baseline controls associated with the system’s security impact level (low, moderate, or high) as defined in NIST SP 800-53, or choosing controls based on organization-generated control selection
- Tailoring the baseline or organization-selected controls to account for organizational policies, system environment, specific threats, and/or system-specific considerations
- Documenting the selected controls in the system security plan (SSP)
- Developing a strategy for continuous monitoring of the systems that aligns with the organization’s overall continuous monitoring strategy
- Reviewing and approving the SSP for the systems
The goal of the Select step is to establish a tailored control set that adequately addresses the risks identified during the categorization process while aligning with the organization’s broader risk management strategy. By tailoring controls, organizations can ensure that security and privacy measures are cost-effective and will appropriately mitigate the risks faced by the system and, therefore, by the organization at large.
An essential aspect of this step is the identification of common controls. These are controls that are implemented at an organizational level and can be applied across multiple systems, reducing duplication of effort and ensuring consistency. For example, an organization may implement a single incident response plan (IRP) that also applies to all downstream business units and systems, thus making it a common control. Proper identification and documentation of common controls help streamline the implementation process and support the organization’s overall security posture.
Engaging stakeholders ensures that the selected controls are agreed upon to implement and that they align with mission and business objectives. Leveraging existing tools, such as automated control selection platforms or pre-built control baselines, can also simplify this step and reduce the potential for errors.
Completing the Select step thoroughly and thoughtfully sets the stage for effective implementation of security and privacy controls in subsequent steps. This step keeps the organization’s resources focused on addressing the most significant risks and supporting the overall goal of safeguarding mission-critical systems and information.
Step 4: Implement
This step is where the selected security and privacy controls are configured and applied within the system to safeguard its information and operations. The effectiveness of this step relies heavily on the thoroughness and precision of prior steps, particularly the selection and tailoring of controls.
A key activity within the Implement step is configuring the previously selected controls within the system’s environment to align with the organization’s security and privacy requirements. Another is documenting the implementation of controls in the SSP to provide a clear and auditable record of compliance.
Best practices and industry standards should guide the implementation of controls. Organizations adhering to FISMA requirements and others who may choose to leverage well-known and trusted controls will use NIST SP 800-53. This resource works hand-in-hand with the RMF and supports the NIST CSF and other frameworks through well-documented crosswalks and mappings. Additionally, the NIST 800-53 controls catalog provides extensive implementation guidance and examples for organizations implementing security and privacy controls.
This step often involves collaboration across various teams—including system administrators, security engineers, and privacy officials—to ensure that controls are applied effectively and that there is no disruption of system functionality and business or mission operations.
An essential consideration during the Implement step is the documentation of control implementation. This documentation supports compliance efforts and provides valuable reference material for future audits, third-party assessments, and any system modifications that may occur. Organizations can streamline these processes by maintaining detailed and accurate records and reducing the time and effort required for subsequent reviews.
Step 5: Assess
Once the security and privacy controls are implemented and their configurations documented, the organization next needs to assess the effectiveness of these controls at reducing risk according to the organization’s documented risk management process.
Key activities within the Assess step include:
- Selecting an assessor with the appropriate level of independence to conduct an impartial review of controls
- Identifying and documenting the scope of the control assessment
- Leveraging pre-existing and/or automated means to conduct the control assessment
- Identifying and documenting any findings or weaknesses in the control implementation
- Developing a plan of action and milestones (POA&M) to address remaining identified deficiencies
- Remediating the deficiencies identified in the assessment
The applicable laws, regulations, policies, and/or standards the organization must adhere to will determine the level of independence required when choosing the appropriate assessment team. In some cases, this can be performed by an internal team, but many times, a verified third-party assessor is required to perform the controls assessment.
A detailed report should be delivered upon completion of the assessment, providing the organization with a list of findings and recommendations for those identified deficiencies. This report is the blueprint of risk that the organization must consult in conducting remediation activities for both immediate action and for those that require planning and resource commitment that can be captured as part of the POA&M process. Additionally, communication across the organization is critical during this step as it allows system stakeholders to address initial findings and begin planning for required changes and for continued risk discussion between system-level and organization-level stakeholders.
By completing the Assess step, organizations gain concrete feedback regarding the effectiveness of their security and privacy controls. This step ensures that the RMF process continues to be an effective mechanism for managing risk to the organization.
Step 6: Authorize
With the assessment of controls complete and remediation activities performed or planned as part of the POA&M process, the RMF transitions to the Authorize step. This step is focused on evaluating the system’s overall risk posture and making an informed decision about whether to authorize the system for operation.
The authorization decision is based on a thorough review of the assessment results as well as an evaluation of residual risks and their alignment with the organization’s risk tolerance. Additionally, the decision to authorize rests with a senior official, thereby assigning organizational accountability at a high level for the acceptance of risk. For federal agencies, this typically falls under the responsibility of the chief information officer (CIO), chief information security officer (CISO), or senior agency official for privacy (SAOP). Likewise, for most private companies, this role is typically served by the CIO or CISO.
The primary objective of the Authorize step is ensuring that the system’s residual risks are understood and accepted by organizational leadership. This requires a comprehensive understanding of the system’s role within the organization and its potential impact on its essential mission/business functions as well as the potential consequences of operating the system with identified risks.
Key activities within the Authorize step include making a determination of appropriate risk tolerance aligned with the risk management strategy and development of risk responses: avoid, mitigate, transfer, accept, and/or share.
One of the most important aspects of the Authorize step is the development of the authorization to operate (ATO) letter. This document serves as the formal record of the authorization decision, providing a necessary level of accountability in the risk management process.
Step 7: Monitor
With the systems authorized to operate, the organization next needs to maintain adequate ongoing monitoring. This provides regular input concerning the security and privacy posture of the systems in order to support the risk management decisions made at the organizational level.
Key activities within the Monitor step include:
- Executing the continuous monitoring strategy to monitor the information system and its environment, including ongoing assessments
- Analyzing the results of continuous monitoring to inform risk response
- Reporting continuous monitoring outputs to leadership
- Developing and implementing a system disposal strategy
It is important to make sure that the authorization of a system is not just a checklist exercise. A lot of work must go into implementing the RMF, and this continues with operationalizing the continuous monitoring strategy by way of maintaining situational awareness of the system and its operating environment.
Change is constant, and this extends to technology, business needs, and environmental factors that all play a part in the effectiveness of the controls put in place. Continuous monitoring ensures that the system and its environment can maintain an adequate level of security despite these constant changes. Attempting to do this manually can be an insurmountable task for most organizations. Fortunately, there are trusted tools out there that specialize in managing the IT asset lifecycle (including discovery) and configuration management, among other services. With a strong and effective tool in place to monitor the assets and services your organization relies on, it greatly simplifies the continuous monitoring process.
Conclusion
One of the best frameworks for addressing risk management in a structured and detailed manner is NIST 800-37, also known as the Risk Management Framework. The RMF lays out a standardized process that is both comprehensive in its material and flexible in its adaptation to any organization’s needs. While the RMF is intended as part of the federal space for agencies and organizations who do business with the US government, its flexibility means that any organization can implement it by adhering to its seven steps: Prepare, Categorize, Select, Implement, Assess, Authorize, and Monitor.
The RMF is one of the most effective mechanisms for enabling organizations to clearly communicate system-level risk to the organization, providing senior leadership the necessary view of its operations to understand and appropriately respond to risk. In today’s ever-changing technology environment, the RMF is battle-tested and proven for those in the federal space as well as other organizations looking to implement a thorough risk management process.