SOC 2 Controls: Best Practices
SOC 2, established by the American Institute of Certified Public Accountants (AICPA), is a compliance framework designed to help organizations safeguard information, establishing the protection of client interests and privacy.
At its core, SOC 2 evaluates businesses based on five Trust Services Criteria (TSC), each focusing on critical aspects of security, availability compliance, and operational integrity. These criteria define the key principles that organizations must adhere to for data protection, operational reliability, and trustworthiness.
SOC 2 controls are processes, practices, and policies used by organizations to establish the security of their systems and data and to both prevent and detect security problems. In this article, we explain what SOC 2 controls are and provide a number of best practices for effectively setting them up and maintaining them.
Summary of key SOC 2 controls best practices
The table below summarizes the best practices described in the remainder of the article.
| Best practice | Description |
|---|---|
| Get familiar with the SOC 2 control types | In order to have a structured approach for later control implementation, learn to categorize controls by scope and function. |
| Start with the basics: policies and procedures | Policies and procedures are the foundation for your security posture and control implementation. |
| Test control effectiveness | Test new SOC 2 controls in real-world settings and fine-tune them for better integration. |
| Monitor and update SOC 2 controls continuously | Regularly review and adjust controls to keep them effective. |
| Build a culture of compliance | Engage the entire team to ensure unified compliance efforts. |
| Establish clear roles and responsibilities | Assign accountability for consistent compliance task management and for proactively addressing potential risks. |
| Implement effective evidence management | Maintain thorough and organized records of control activities to demonstrate consistent application and adherence. |
| Leverage compliance tools | Use automated solutions to streamline evidence collection, monitor processes, and reduce human error. |
Get familiar with the SOC 2 control types
Understanding the Trust Services Criteria
Here is an overview of each TSC and its significance:
- Security: Often referred to as the “Common Criteria,” this includes measures designed to protect information from unauthorized access. (Your SOC 2 report will always include Security by default.)
- Availability: Controls that evaluate whether systems and information are operational and accessible when needed.
- Processing Integrity: Ensuring that system and information processing is accurate, timely, and authorized.
- Confidentiality: Safeguarding sensitive data from unauthorized disclosure.
- Privacy: Handling personal information in accordance with privacy policies and regulations.
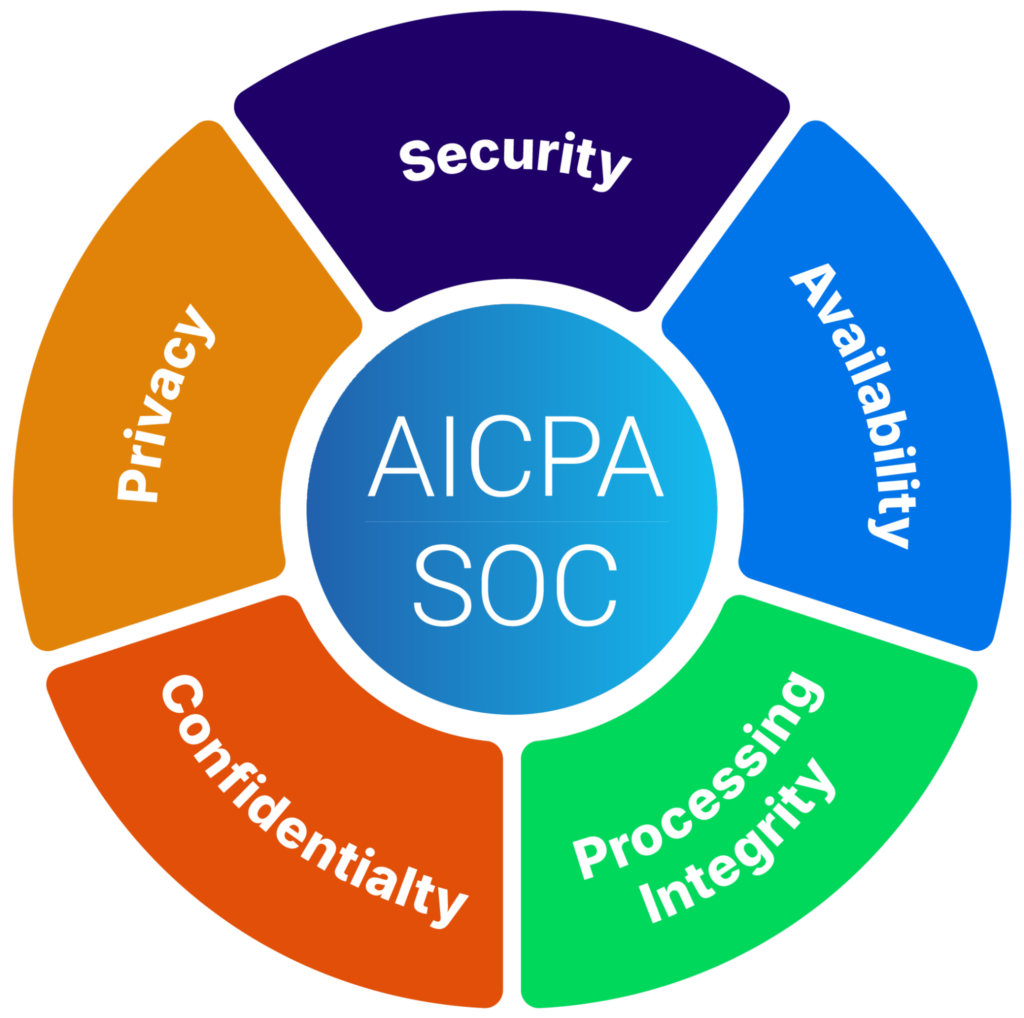
Trust Service Criteria (source)
Scope-based control grouping
SOC 2 controls can be categorized by their scope in meeting TSC requirements into Common Controls and Criteria-specific controls, each playing a distinct role in achieving compliance and security.
Common Controls refer to controls that apply across all TSCs, forming the foundation of your compliance efforts.
Examples of Common Controls:
- Access management: Granting access exclusively to authorized personnel to protect sensitive data and systems. This may include user authentication, role-based access, and periodic access reviews.
- Incident response: Establishing protocols for identifying, reporting, and responding to security incidents to protect organizational assets across all TSCs.
- Employee training and awareness: Conducting regular security training and awareness programs to make sure staff understand policies and procedures and their role in protecting organizational data.
Criteria-specific controls are designed to address the unique requirements of individual TSCs, providing tailored protections where they are most critical. These controls require that specialized processes and safeguards be in place to meet the objectives of each criterion.
Examples of Criteria-specific controls:
- Availability controls: System redundancy and failover mechanisms. These support the continued availability of systems during unexpected failures, using backup servers or mirrored data centers to maintain continuity.
- Processing integrity controls: Error-detection protocols that identify and correct data processing errors to meet the Processing Integrity requirement for accurate and timely data handling.
- Confidentiality controls: Data encryption is the most common of these controls. Encrypting sensitive information in transit and at rest demonstrates protection against unauthorized access or disclosure.
Privacy controls: This area is about ensuring that personal data is collected, processed, and stored in accordance with user consent and privacy policies. An example would be consent management.
Function-based control grouping
To fully grasp SOC 2 compliance, it’s helpful to see how controls are categorized not only by their scope but also by their function. While Common Controls and Criteria-specific controls focus on meeting the TSCs, grouping controls into operational, governance, and technical functions helps address your organization’s daily activities.
- Operational controls are those that relate to the day-to-day management of security and availability, such as incident response, system monitoring, and access control processes. These controls ensure that procedures are in place to respond promptly to security incidents, monitor system health, and manage user access effectively.
- Governance controls establish the organizational policies and procedures that define and enforce security standards. These include oversight roles, compliance documentation, periodic risk assessments, and employee training initiatives. Governance controls provide the framework and accountability necessary to maintain a consistent security posture.
- Technical controls focus on specific technologies and security mechanisms, such as encryption, network segmentation, multi-factor authentication, and vulnerability scanning. They are essential for securing the organization’s infrastructure, supporting data privacy, and protecting against unauthorized access or breaches.
Start with the basics: policies and procedures
The first logical step in this SOC 2 journey is crafting your policies and procedures. These documents will form the backbone of your security posture, guiding all subsequent control implementations.
Think of your policies as the yardstick by which your organization will be measured during the audit. They outline the rules, expectations, and processes that define your compliance efforts, serving as a benchmark for assessing whether controls are adequately designed and effectively implemented.
A well-crafted policy does more than fulfill a requirement—it becomes a reference point for the audit, providing clear evidence that your organization is committed to maintaining security, availability, and integrity.
One important recommendation to keep in mind is to avoid overloading your policy with excessive restrictions or setting unrealistic expectations. For instance, committing to address critical vulnerabilities within 24 hours might sound ambitious, but is it practical? Instead, take a critical look at your policies and procedures before finalizing them, and involve relevant stakeholders across the organization. Your IT team, for example, might suggest revising that 24-hour commitment to a more achievable 72-hour timeframe based on their expertise and capacity. Leveraging your team’s insights and experience is essential for your policies to be not only aspirational but also actionable, aligning with real-world capabilities.
Test control effectiveness
Once your policies are in place, it’s time to get the ball rolling by testing control effectiveness in real-world scenarios. This means assessing how seamlessly the new controls and activities integrate into daily operations and identifying any areas for adjustment.
For example, SOC mandates certain controls such as background checks, access request protocols for systems, and personnel non-disclosure agreements (NDAs). Incorporating these controls in your recruiting process serves the dual purpose of ensuring compliance, and testing control implementation.
For instance, an onboarding checklist can help confirm that background checks are completed, access requests are duly approved, and NDAs are properly signed and documented.
By embedding SOC controls into daily operations, you set the stage for consistent practices, making it easier to demonstrate compliance and confidently address auditor questions.
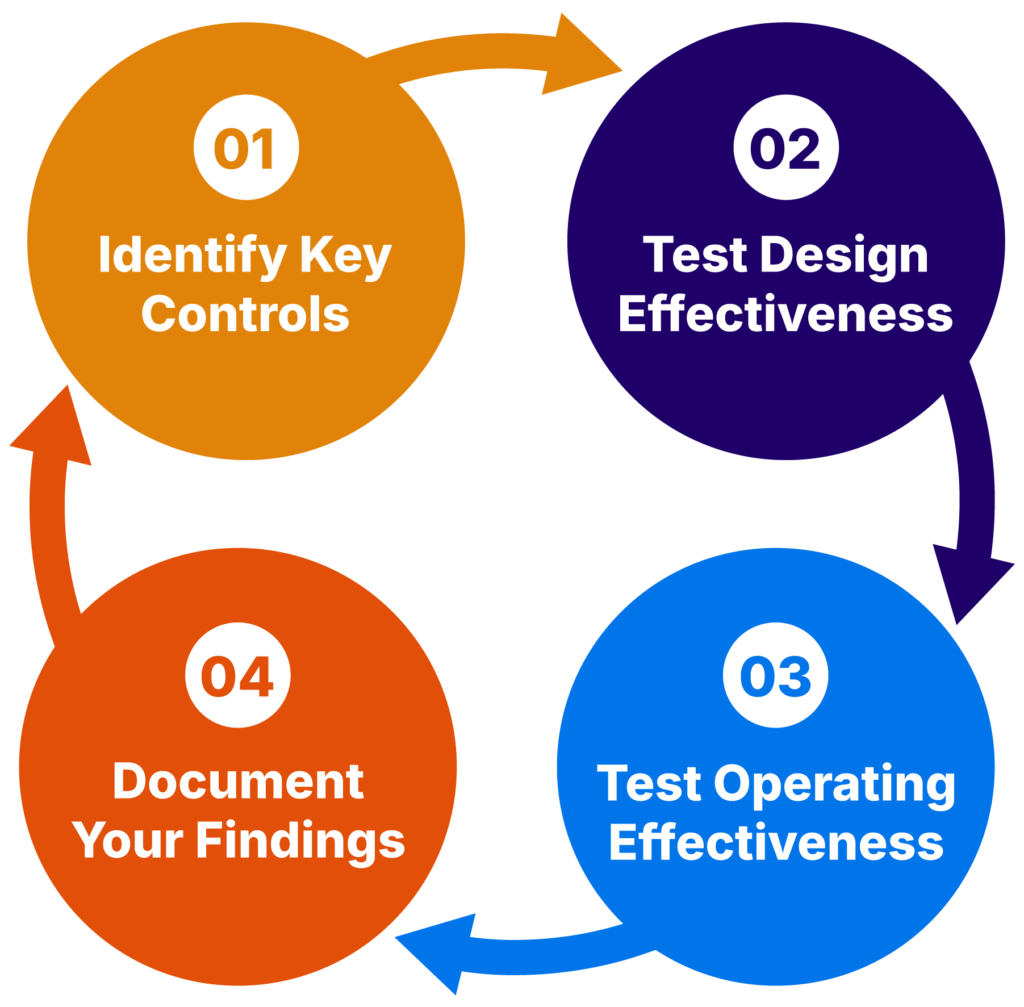
Control Testing (source)
Monitor and update controls continuously
A one-point-in-time check is seldom enough for control testing if your company is striving to be truly secure and not just to achieve tick-mark compliance.
An example of a common weakness in SOC 2 is personnel security, which often becomes the Achilles’ heel for many companies when it comes to SOC 2 compliance. This area is a frequent source of exceptions in SOC 2 reports, especially with access control management. Common issues include delays in deactivating access for employees who leave the company or changes in roles that require adjusted access permissions.
Consider the case of a contractor hired to build your cloud infrastructure. Months later, during the audit, their name still appears as a privileged user in your cloud service provider’s records. The result? An exception in your SOC report and a critical security weakness.
To avoid such gaps, companies should establish a regular control testing schedule and treat testing as an ongoing process.
For the example given, this may include periodic system reviews to remove outdated accounts, using offboarding checklists to ensure access is promptly revoked, or automating alerts for privileged accounts that remain active without justification.
Build a culture of compliance
Getting all personnel on board with compliance is essential to making SOC controls effective. If not everyone is committed to compliance efforts, even well-designed controls can fall short.
Without team-wide commitment, enforcing policies and tracking responsibilities can become incredibly challenging, especially when roles and accountability aren’t clear. For companies aiming for SOC compliance, a strong culture of security and accountability isn’t just a benefit—it’s a requirement. When the entire team is engaged, implementing and maintaining controls becomes not only easier but also far more effective.
Implement effective evidence management
Controls are only as robust as the evidence supporting them. While SOC controls provide flexibility and room for customization, it’s crucial for every control activity to be thoroughly documented.
For example, documenting a user access review might involve taking and saving screenshots of critical systems showing the list of users and their roles during the review. Similarly, documenting the assessment of critical vendors can include keeping records of vendor risk questionnaires, signed contracts, or emails that demonstrate that the company evaluates their vendor’s performance.
Organizations may opt to use governance, risk and compliance (GRC) solutions that facilitate the implementation of controls, continuous monitoring, evidence collection and staying up to date with changes in regulatory requirements.
For smaller companies with manual processes, leveraging spreadsheets to track control activities or saving audit trails in shared drives can be an effective and practical way to ensure compliance. The key is to demonstrate that processes are not only in place but also consistently followed, with clear oversight and continuous monitoring to verify their effectiveness.
Establish clear roles and responsibilities
One tip for overcoming SOC 2 challenges is to assign clear roles and responsibilities. Each role holder should fully understand their accountability and the specific expectations set for them. While having a dedicated HR team may not be feasible for smaller companies, establishing clear accountability is essential to avoid common pitfalls.
For example, your organization may hire contractors who come on board to assist with specific projects. Without clear ownership of access management, these individuals might still have privileged access long after their contracts end, creating unnecessary risks. Defining roles and appointing accountable persons for promptly revoking access—whether it’s IT, management, or another team—can prevent these oversights and reinforce personnel security practices.
Leverage compliance tools
Automate wherever possible; using compliance tools can streamline control tracking, evidence collection, and reporting, reducing the risk of human error and supporting consistency across processes. Automation is especially valuable for repetitive tasks like user access reviews, annual security training, and maintaining an up-to-date asset inventory.
Solutions with advanced discovery, dependency mapping, and asset management features take this a step further, simplifying the monitoring of hybrid environments. These tools help maintain data accuracy and ensure that your organization stays audit-ready with minimal manual effort.
Takeaway
Every SOC 2 audit is unique, with auditors often interpreting control requirements in slightly different ways. The key to success in implementing SOC 2 controls lies in thoroughly documenting and evidencing each control activity, seamlessly integrating each control into your day-to-day operations, and monitoring adherence through control testing.
More than just a one-and-done checklist, SOC 2 is a powerful tool for identifying gaps, strengthening your security posture, and driving continuous improvement.
By treating compliance as an evolving journey rather than a static goal, companies can adapt to emerging threats and regulatory changes.
By embracing SOC 2 as an ongoing process, organizations not only ensure compliance but also foster a culture of security and innovation, building lasting trust with clients and stakeholders.