ISO 27001 Compliance Checklist: How to prepare for a successful audit
Passing an ISO 27001 compliance audit is an important milestone that requires good preparation to achieve. Before such an audit, companies must perform extensive groundwork, including comprehensive documentation creation, information security management system (ISMS) assessments, proof of control implementation, and even other precursory audits.
This article provides a checklist of audit expectations and explains how to manage ISO 27001 controls in a tailored fashion. It also includes a set of best practices for a successful audit.
Summary of ISO 27001 compliance checklist items
ISO issued a new version of the 27001 standard in October 2022 that contains 10 clauses and 93 controls. If your company wishes to become (re)certified or improve its ISMS to become audit-ready, the first step is to familiarize yourself with the updated version.
In this section, we cover the updated mandatory requirements per the ISO clauses. We discuss the new ISO control groups in the next section.
The table below lays out the ISO 27001 compliance checklist items of mandatory documents for compliance with clauses 4-10. These will be required during the first stage of the audit.
| Checklist item / action | Clause ID | Required evidence | |
|---|---|---|---|
| 1 | Determine the scope of the ISMS | 4.3 | ISMS scope |
| 2 | Develop the ISMS framework | 5.1; 5.2 | Information security policy* |
| 3 | Assess information security risks | 6.1.2; 8.2 | Information security risk assessment process/procedure;
risk assessment results |
| 4 | Treat information security risks | 6.1.3; 8.3 | Information security risk treatment process/procedure;
risk treatment plan* |
| 5 | Produce a statement of applicability (SoA) | 6.1.3 | Statement of applicability* |
| 6 | Set ISMS objectives | 6.2 | Documented information on the ISMS objectives |
| 7 | Assign information security roles and responsibilities | 7.2 | Records of personnel competence |
| 8 | Determine ISMS operational information | 8.1 | Documented information confirming that the ISMS is being applied and controlled |
| 9 | Establish security measurements | 9.1 | Security metrics and KPIs |
| 10 | Perform an internal audit on information security | 9.2.2 | Internal audit program;
ISMS audit reports |
| 11 | Conduct a management review of the ISMS | 9.3.3 | ISMS management review reports |
| 12 | Correct deviations | 10.2 | Records of nonconformities and corrective actions |
* Companies that hold a previous ISO 27001 certification should update the following to stay compliant:
- Risk treatment plans with new controls
- SoA
- Information security policies/procedures, where necessary
All of the ISMS steps are undertaken essentially to protect company assets. Device42’s asset documentation can be used extensively during the audit process, simplifying compliance.
Details on ISO 27001 compliance checklist items
1. Determine the scope of the ISMS
Your organization has specific information security requirements, which may be influenced by industry, size, stakeholders, and business objectives. These factors need to be considered to determine the ISMS scope, and this decision should be documented.
2. Develop the ISMS framework
In the context of developing the ISMS framework, information security policies are the “what” that sets the direction for “how” security gets implemented. They should be defined, approved, distributed, and maintained.
Also, the core of a compliant and effective ISMS implementation lies in the level of leadership support. At the very least, management commitment can be demonstrated by having an approved policy.
3. Assess information security risks
The company’s threat profile and the risks to which assets are exposed are determined in a risk assessment, employing a qualitative or quantitative methodology. The process and results of this assessment are necessary artifacts during the ISO 27001 audit. Threat modeling and vulnerability assessment are inputs for the risk assessment.
Information gathered by Device42 can be used to conduct thorough risk assessments.
4. Treat information security risks
Risks prioritized for mitigation will have treatment plans. There are four possible responses to threat risks: avoid, accept, transfer, and mitigate; the last of these will typically involve additional or strengthened controls. This process, risk responses, and treatment plans all need to be documented.
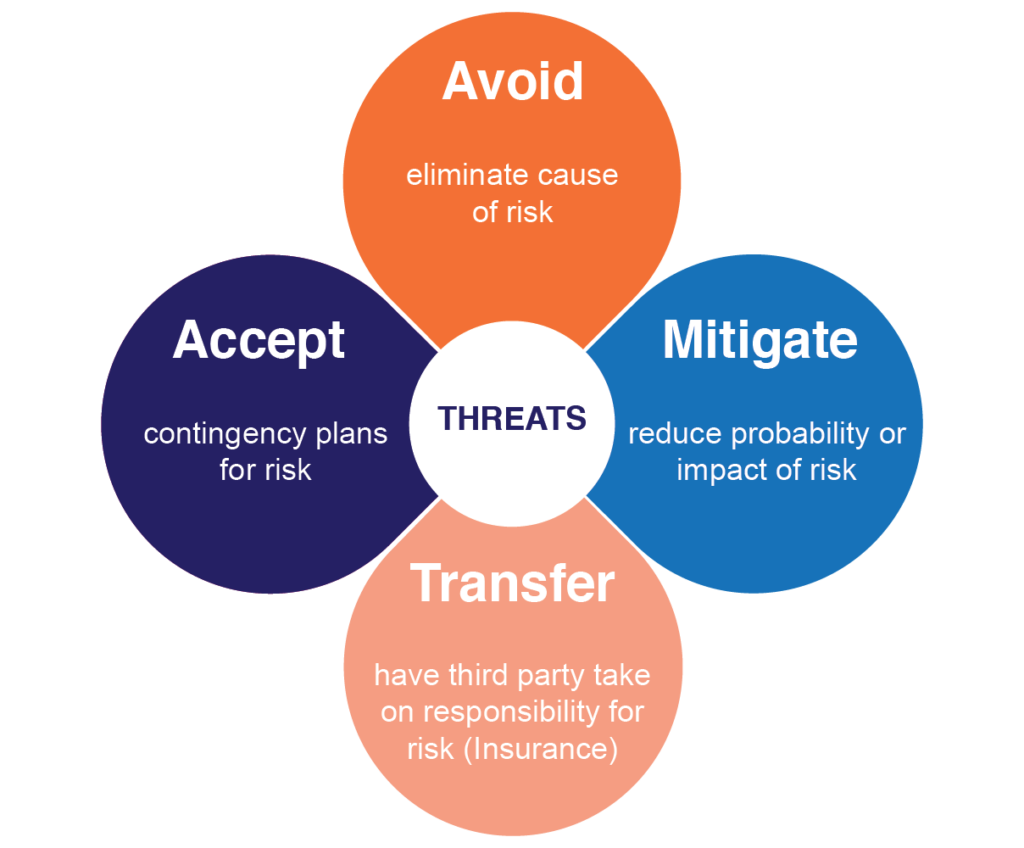
The four possible responses to a threat risk
5. Produce a statement of applicability (SoA)
The SoA is a core document for the audit and should include the list of ISO 27001 Annex A controls. It should indicate the ones selected for implementation as well as those excluded and the justification of their non-applicability. Furthermore, the current implementation status of each should be provided.
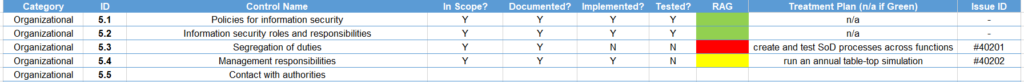
6. Set ISMS objectives
The objectives should be in line with the information security policy and should consider the risk assessment results. For instance, decisions should be made on what access control measures are sensible for personnel and systems processing confidential information, what the acceptable incident response SLAs are, and what the awareness and training program looks to achieve. Objectives can be part of the information security policy, other topic-specific policies, and/or a separate set of documentation.
7. Assign information security roles and responsibilities
Designated functions should have responsibilities and authority for implementing and reporting on the ISMS. Records of their competence (relevant experience and certifications) are required in the ISO 27001 compliance audit.
8. Determine ISMS operational information
Operational information refers to demonstrating the effective implementation of the ISMS and its objectives. Objectives can be met through documented processes and procedures, training responsible personnel, and periodic control testing. For example, for secure software development, you may have operating procedures, approved tools and repositories, regular on-the-job training for software engineers, change control measures, and regular testing of work samples.
Device42 features can be leveraged to monitor changes to configurations and other important aspects that could impact security goals.
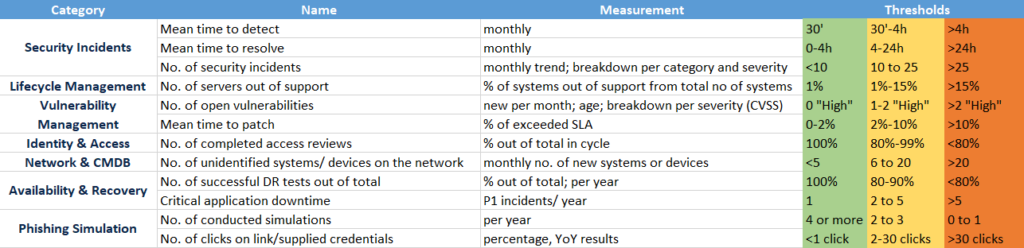
9. Establish security measurements
Security performance is assessed through metrics, KPIs, and trend analyses. These will have to be part of an ongoing monitoring of the ISMS, where its effectiveness is measured through meaningful data. Such metrics need to be available for the audit.
Example of security metrics:
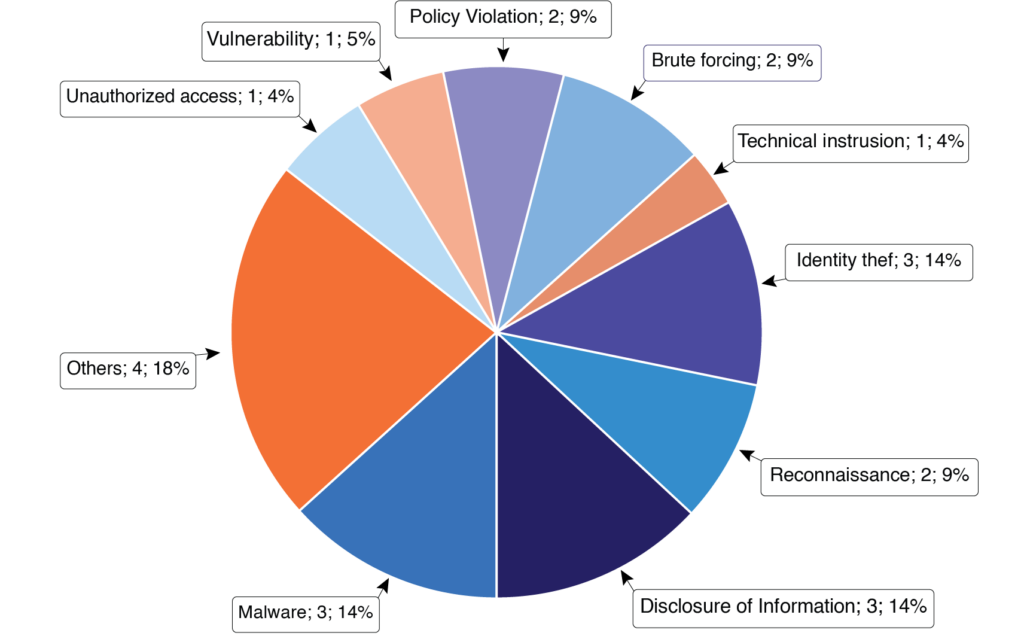
Example visualization of the “number of security incidents” metric
10. Perform an internal audit on information security
The ISMS needs to be subject to an independent internal review program. The internal audit results need to be available for consultation in the ISO audit.
11. Conduct a management review of the ISMS
Management needs to be informed regularly about ISMS progress to ensure that the program remains suitable, to stay aware of issues, and to offer any sponsorship needed. This includes reports, meeting minutes, decisions supporting improvement, and corrections.
12. Correct deviations
Nonconformities should be captured in an information security risk register. Deviations and breaches (incidents) need to be assessed and treated following a predefined process. Such records should also be available as part of the mandatory stack for the ISO 27001 compliance audit.
ISO27001 control implementation
Clauses are not the sole subject of a compliance audit. They go hand in hand with the design effectiveness of the ISMS, which is reflected by the ISO control implementation status.
In the new ISO 27001, the number of ISO controls is reduced from 114 to 93. They are grouped into four categories, as shown in the table below.
| Control group | Number of controls | Description |
|---|---|---|
| Organizational | 37 | These controls address managerial activities, such as having policies and connected documents, roles and responsibilities, inventory management, business continuity management, third-party management, compliance with laws and regulations, etc. |
| People | 8 | People controls focus on employee screening, awareness and training, disciplinary processes, and more. |
| Physical | 14 | These controls are designed to protect premises, information processing facilities, and (implicitly) data and equipment. |
| Technological | 34 | This set of controls represents technical safeguards for information security, such as incident response, network protection, identity and access, and secure development. |
Did you know that ISO controls are discretionary, even if you aim for certification? Your company does not need to implement them 1:1, which means the following:
- Some requirements may be irrelevant to your company (e.g., “secure coding” for a company that only uses off-the-shelf software).
- Controls should be applied in a way that is proportional to the risks. For instance, following a risk assessment, the company may choose to back up data from systems that process sensitive information and accept the risk of losing less critical data in the event of a disruption.
- Your controls may need to satisfy internal and external requirements that can overlap with ISO 27001:2022 but also add new controls. Blending these in an effective way for your organization is perfectly acceptable.
Adapting ISO controls
Even though the 93 controls listed in ISO 27002:2022 are divided into groups, as explained above, some of them may span all four areas. Let’s take “remote working” for example, which is suggested as a “people” control. Well, to secure information while working remotely, more considerations come into play:
- There’s the technological aspect that makes this possible (implementing the infrastructure that allows for remote work and providing additional measures such as VPN and MFA).
- There is the organizational part, such as a dedicated WFH policy, a BYOD registration and inventory process, and strong authentication standards.
- There’s the physical angle (security of off-site equipment, e.g., mobile devices).
- Of course, there’s certainly the people aspect since acceptable use rules and awareness training are necessary to ensure appropriate conduct.
Device42’s asset management can facilitate correlating resources and accesses, aiding in the creation and maintenance of remote access controls.
Many ISO controls are also interconnected; for example, threat intelligence goes hand in hand with vulnerability management. Your company may choose to consolidate them into groups such as the examples shown in the following table.
| Group | Controls |
|---|---|
| Policies and procedures | Information security policy is defined and enforced. Procedures are available and stored centrally. |
| Roles and responsibilities | Roles for managing information security in the organization are defined, mandates are approved, and responsibilities are made known. |
| External relationships | Contact with special groups and authorities is established, along with participation in knowledge sharing with peers and authorities. |
| Information asset management | Assets are managed throughout their lifecycles: identification, ownership, inventory, classification, protection, monitoring, and disposal. |
| Access control | The principle of segregation of duties is enforced at the physical and logical levels. Identity and access governance is put in place. |
| Acceptable use | This includes establishing rules for remote working and the use of email, the Internet, company software and hardware, social media, and acceptable communication channels. |
| Third-party information security risks | This area includes defining requirements for outsourcing, cloud, and other critical services as well as monitoring requirements. |
| Awareness and training | Employees, contractors, and other relevant groups are periodically trained and awareness sessions for targeted topics are held. |
| Laws and regulations | Industry regulations that contain provisions on securing information are observed, such as the Health Insurance Portability and Accountability Act (HIPAA), the Privacy Act, the General Data Protection Regulation (GDPR), the Digital Operational Resilience Act (DORA), copyright laws, license use terms, etc. |
| Business continuity management | A BCM framework is put in place, a crisis management team is appointed and trained, and redundancy strategies are tested. |
| Physical security | Building access is segregated into perimeters as reflected in different access control entitlements. Access to critical equipment is secured with extra layers and intrusion monitoring is put in place 24/7. This also includes policies such as the visible wearing of badges. |
| Human resources | This area spans defined job roles, background screening, NDAs, and disciplinary processes. |
| Auditing | This includes independent auditing of information security. |
| System and network security | This area covers activity logging and monitoring, network segregation, software installation processes, and intrusion detection and prevention systems (IDS/IPS). |
| Secure development | Secure architecture and engineering principles are enforced. Application security controls are addressed as part of project and change management. This also includes secure software development lifecycle (SDLC). |
| Incident management | Controls are put in place for detection, response, mitigation, forensics, and reporting, including lessons learned related to cybersecurity incidents. |
| Information protection | This includes controls for labeling, transfer, encryption, masking, DLP, and the deletion of information. |
| Backup and availability | This group includes proactive management of system capacity, ensuring that backups are made and securely stored, establishing redundancies for critical processes, and creating a disaster recovery plan. |
| Vulnerability management | Vulnerability-related actions include threat intelligence, vulnerability scanning, patch management processes, and penetration tests. |
| Hardware protection | This encompasses controls on ICT equipment siting, use, maintenance, storage, reuse, and disposal. |
Of course, you will want to tailor this to your company’s needs, but ensure that you can cross-reference your controls to the ISO controls. This will be needed in the mandatory statement of applicability.
Implementing ISO controls
Implementation guidelines for each control are in ISO 27002. Some may be too high-level for parts of your organization, so you may need to create designs (blueprints) for the implementation of controls.
These designs don’t need to be a copy of the ISO control guidelines, and this is not an expectation of the audit. The ISO control objectives should be met, but their implementation is often not managed one by one in isolation from the rest of the controls.
Let’s take asset management. This is touched by the controls “inventory of information and other associated assets,” “classification of information,” and “labeling of information” and partially by other controls. It might make sense for your company to design an information asset management policy and then a blueprint that follows a set of sequential processes, such as asset discovery, identification, ownership, inventory, classification, protection, and dependency mapping.
Device42 provides a centralized repository for all IT assets, helping you maintain an accurate asset inventory. Device42 can also identify and categorize data stored across assets, aiding in information classification.
Other examples of policies or process designs that you might need to create or enhance based on ISO controls are:
- Vulnerability management
- Secure SDLC
- Third-party security risk management
- Business continuity planning
- Incident response procedures
- Change management and change control.
Device42’s network discovery and mapping can help identify vulnerabilities and unsecured network connections.
Even with outsourced development, systems, infrastructure, or security processes, a company is still accountable for maintaining these as compliant. With insights into the hardware and software lifecycle, Device42 can support effective third-party security management.
Finally, by knowing asset locations, interactions, and interdependencies, Device42 can help in the faster identification and resolution of security incidents.
Audit best practices
Audit missions often fail to run smoothly due to the unavailability of people, problems retrieving system records, or miscommunication that leads to a surprise finding in the final report. Here are some best practices to keep the ISO 27001 audit on track from start to finish.
| Category | Best practice area | Description |
|---|---|---|
| Initiation | Auditor due diligence | Use internal processes to determine if the audit company meets legal and regulatory requirements as well as your company’s. |
| Contracts/NDAs | Do not start the engagement without a contractual arrangement in place. | |
| Scoping | Discuss the boundaries of the audit engagement. | |
| Logistics arrangements | Ensure that the audit will be properly accommodated if there will be a physical presence. | |
| Communication | Requirement management expectations | Establish communication channels and response timelines, and share lists of people who may be contacted. |
| Management support | Management should be on board with the engagement and needs to support the audit in obtaining necessary time and information from teams. | |
| SME availability | Announce the commencement of the audit as soon as it’s official, asking for relevant SMEs to be available or to have a delegate throughout the engagement. | |
| Administration | User accounts | If necessary, set up auditor user accounts in your active directory. |
| Information transfer | Set up a safe location for transferring sensitive documents, and ensure that only authorized personnel engage in information transfer. | |
| Access rights and limitations | Determine what access rights (physical, logical) are required for the audit fieldwork. | |
| Documentation | ISO 27001 mandatory document checklist | Ensure the availability of the mandatory records in the summary table near the start of this article. There is often more than one document required to demonstrate compliance with an ISO clause, so you can group them in ways that make sense (see below for examples). |
| Closure | Discussing findings | Be prepared to transparently discuss any observed nonconformities. |
| Issue management response | Take the time to verify if the findings result from a correct and complete evidence interpretation. Discuss any differing views on the findings and their severity. | |
| Remediation plans | Define measures of improvement that will treat the root causes and reduce risk gaps. | |
| Optimization | Continuous improvement | Constantly monitor and review the ISMS lifecycle and be ready for the next audit. |
The following list shows examples of ways to organize documentation and other artifacts prior to the audit:
- Information security policies:
- Physical security policy
- Acceptable use policy
- IT security policy
- Business continuity policy
- Information classification policy
- ISMS procedures, guidelines, standards, baselines:
- Backup management
- Password standards
- Patch management procedures
- Inventory review guidelines
- Secure disposal baseline
- Risk management:
- Information security risk assessments (including threat modeling and vulnerability assessments)
- Risk assessment process and results
- Risk treatment process and plans
- Risk register / security exceptions log
- Monitoring activities:
- Audit findings
- Self-identified issues
- Control test reviews
- Penetration tests
- Crisis management simulations
- Disaster recovery tests
- Vulnerability scans
- Physical security assessments
- Third-party assurance (e.g., SOC2 Type 2 reports).
- Measurements and reports:
- Defined security metrics and KPIs
- Management status reports (monthly/quarterly/yearly) on the ISMS
- Incident reports
- SLAs
- Awareness program:
- Phishing simulations and their results
- Reports of realized online mandatory training
- Awareness presentations for employees (e.g., at onboarding, in general, or targeted by role)
- Internal blogs, awareness emails, “open days,” etc.
Conclusion
An ISO 27001 compliance audit may sound daunting, but the list of documents and artifacts is actually not too complex. As with any audit, good preparation pays off.
We have hopefully made it easy for you by listing the mandatory requirements, breaking down controls, and offering good practices for approaching the audit. A few key takeaways:
- The ISO 27001:2022 release requires an update of the ISMS framework, which includes revised policies, SoA, and risk treatment plans.
- The number of ISO controls has been reduced from 114 to 93, and you are free to implement them using a risk-based approach and tailor them as suitable for the organization.
- Our checklists offer a solid baseline for the ISO 27001 audit. However, the minimum necessary does not guarantee a pass. Strive to implement an ISMS that adds value for your company and be prepared to justify your implementation choices.
- The work is not over once the audit passes. Continue to monitor and treat your information security risks and improve your ISMS.
By integrating Device42 into your ISMS, you can automate and streamline many tasks required for ISO 27001 compliance, thus making the audit process more manageable.
Good luck with your ISO 27001 audit!