- Ansible
- Chef
- Cherwell
- Confluence
- CyberArk
- Foreman
- Foreman Smart Proxy
- Freshservice
- HPSM
- Infoblox
- Jenkins
- Jira
- Jira Cloud
- Jira Service Management Cloud
- Logstash
- Microsoft LAPS
- Microsoft SCCM
- OpsGenie
- PowerBI
- Puppet
- Rundeck
- SaltStack
- Samanage
- ServiceNow
- ServiceNow Express
- Splunk
- StackStorm
- VMWare VRealize
- Zapier
- Zendesk
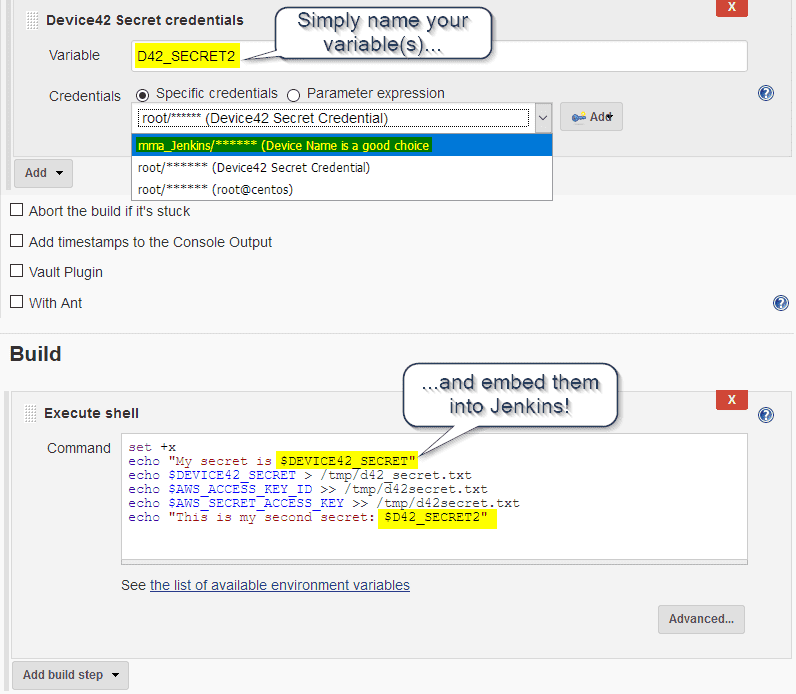
Device42 – Jenkins Credentials Integration
Leverage passwords and other secrets from Device42’s Secrets module in your Jenkins-powered automation!
Integrate Jenkins with Device42 and Leverage Existing Stored Secrets in your Processes!
With the Device42/Jenkins integration, you can extend Device42’s secure password/secret storage to Jenkins. The integration securely retrieves your credentials while Jenkins handles timing and manages processes execution.
Forget about updating saved passwords in multiple places. Simply update Device42, the integration pulls the updated credentials automatically.
Enjoy centralized, secure password management with the Device42 credentials plugin for Jenkins!
Easily add New Credentials or Pass Existing Credentials from Device42 to Jenkins
Authenticate all around your infrastructure:
Servlet containers like Apache Tomcat, Jetty, JBoss, or your favorite java-servlet. Version control systems: AccuRev, CVS, Subversion, Git, Mercurial. Execute: Apache Ant, Maven, or sbt -based projects.
…plus, Shell scripts, Windows Batch commands, and more!
Secure Jenkins-based Workflows!
By leveraging the Device42-Jenkins integration to pull credentials [passwords/secrets/etc.] from Device42, you eliminate the need to embed credentials in plaintext within your automation.
Protect passwords to your repositories, your build servers, etc. – even SSH certificates with Device42!
Run IT with confidence.®