IT Asset Management Best Practices
Return on investment (ROI) is a key metric determining organizational success. In the world of IT, ROI is heavily linked to the outlay of IT infrastructure and services that support the enterprise in achieving its strategic objectives. IT asset management (ITAM) is at the heart of business value since this discipline deals with the lifecycle of assets from their introduction through usage and ultimate disposal. The ISO/IEC 19770-1:2017 standard for IT asset management defines this practice as the coordinated activity of an organization to realize value from IT assets, which include equipment, software, media, license contracts, and associated tools and metadata. How do organizations benefit from effective ITAM? According to the ITIL 4 practice guide, ITAM can help the organization do all of the following:
- Maximize value
- Control costs
- Manage risks
- Support decision-making about the purchase, reuse, retirement, and disposal of IT assets
- Meet regulatory and contractual requirements
While organizations may take a one-size-fits-all approach to managing all assets, the way that software assets are treated is markedly different than hardware assets. Software asset management (SAM) is unique because the software domain goes beyond the physical dimension that characterizes hardware assets, meaning devices such as laptops, servers, and routers. Software assets will be valued differently depending on how they are deployed, how many users they have, the mode and scale of deployment (e.g., on-premises vs. cloud), versions, and associated licenses, among other factors. In the age of the cloud, when most organizations are deploying SaaS solutions and applications are built and deployed using distributed architecture such as containers and microservices, SAM is becoming a very specialized practice requiring a different approach. In this article, we will look at some best practices for IT asset management. When applied correctly, these techniques can go a long way toward properly accounting for all acquired IT assets, ensuring that their usage delivers value at an optimal cost throughout their life in the organization while complying with governance requirements.
List of best practices
The following are five best practices that will help IT organizations to improve their IT asset management processes and derive full value from their investment.
| Adopt a lifecycle approach | End-to-end management of the IT asset’s interaction with the service environment brings the benefits of visibility and control. |
| Ensure governance and accountability | Direction and monitoring of IT asset acceptable use (per COBIT and ITIL4 guidance) are vital in ensuring effective usage, coupled with assignment of ownership. |
| Automate and integrate | The right digital tool will enhance the visibility of the IT asset deployment and facilitate interconnection with other business systems for full value extraction. |
| Engage in proactive verification and auditing | IT asset compliance to internal and external regulatory and statutory requirements will only happen with planned periodic checks on status. |
| Tie ITAM to ITSM practices | Incident, change, configuration, problem, and information security management practices can only fulfill their full potential with a well run IT asset management practice. |
Adopt a lifecycle approach
A holistic approach to IT asset management is critical for maximizing value. IT organizations must implement mechanisms to track IT asset status from procurement through introduction into the service environment, usage, and ultimately disposal. A lifecycle approach offers the best chance of fully realizing IT asset value, accounting for assets, and ensuring their effective and efficient use. The six steps in the IT asset management lifecycle are as follows: 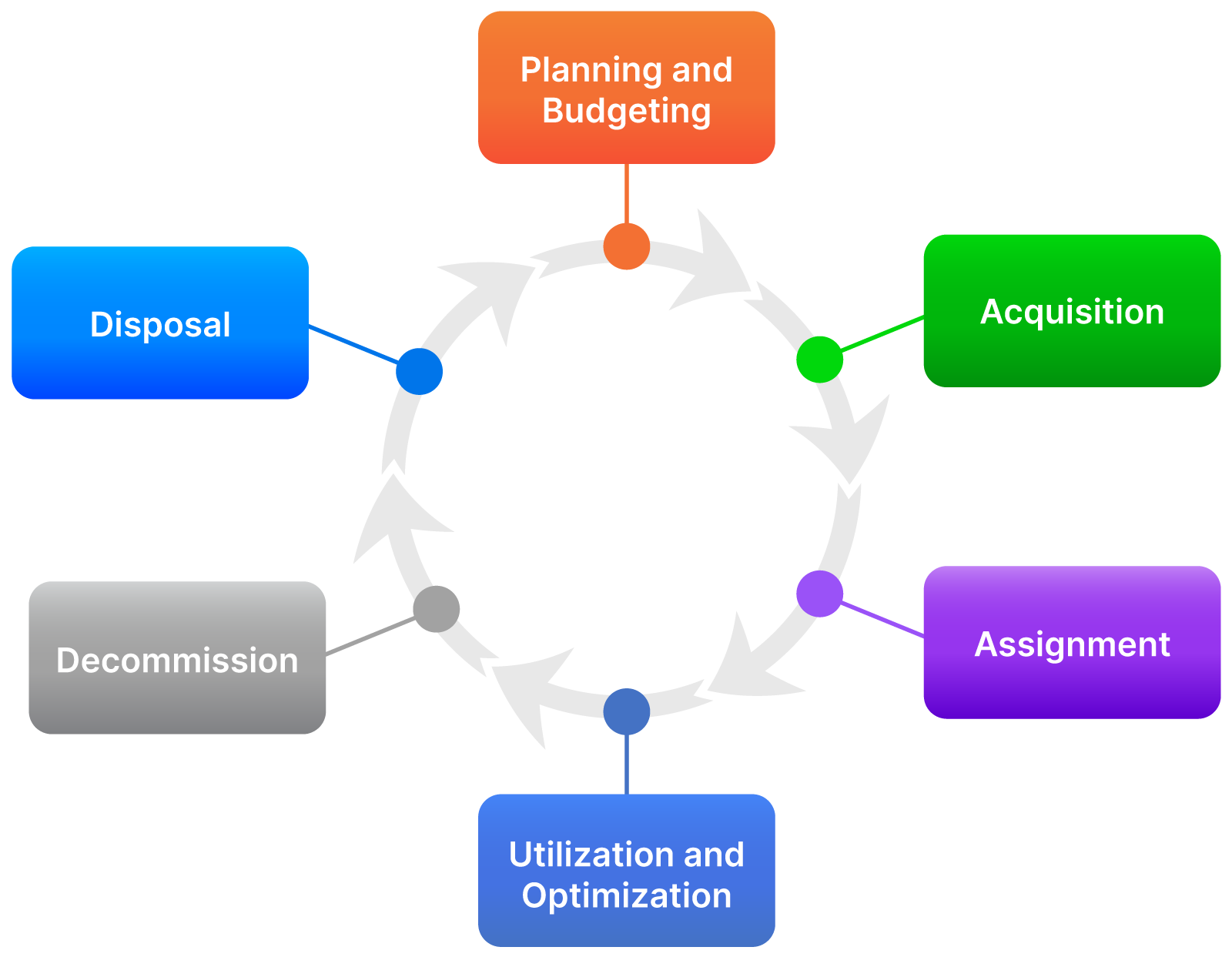
IT asset management lifecycle
- Planning and Budgeting: Planning involves working with stakeholders to understand their service requirements and identifying which IT assets are required to meet them. It also involves scouting the market and checking with vendors to identify options and costs. Budgeting involves aligning with organizational strategy by putting aside the funds required to source the IT asset in a timely and cost-effective manner.
- Acquisition: This step involves following the procurement process to guarantee value for money while purchasing the IT asset. An acquisition could mean outright buying of the IT asset or leasing it through a subscription model. Attention to detail is crucial so that the requirements for the IT asset and the associated vendor support are clearly spelled out, ensuring that what is acquired is fit for the intended use. The vendor contract must stipulate the warranty aspects required for effective value extraction throughout the life of the asset.
- Assignment: Responsibility is delegated to the asset consumer, be that a system administrator or end-user. The assignment record should be captured in a register to track ownership. For IT assets that are being assigned to end-users, the assignment will be tagged to service requests, while those supporting IT services will be tracked through change requests.
- Utilization and Optimization: Value is only realized when an IT asset is actually put to use. The IT asset should be monitored during utilization, tracking metrics such as capacity, performance, and depreciation; this includes when it changes hands through reassignment or redeployment. Optimization involves improving the capability of the IT asset through upgrades and configuration changes that extend the life and value realized.
- Decommissioning: Once the IT asset is no longer useful, and options for optimization have been exhausted, it is retrieved from the assigned user or removed from the active service environment. Decommissioning also involves deregistration of the IT asset if it is lost or stolen. Data, licenses, and configurations contained within the IT asset need to be properly transferred or erased based on organizational data management policies.
- Disposal: Finally, the decommissioned IT asset is permanently removed from the organization in a controlled manner. This could involve returning it to the vendor from whom it was leased, donating it to a charitable institution, or destroying it. Disposal includes formal termination of warranty contracts and ensuring that appropriate records are maintained that detail the sanctioning of the disposal as well as the actual disposal process.
The lifecycle approach applies to all types of IT assets, including both on-premises and cloud-hosted. Organizations that have gone the SaaS direction might wonder why they need to invest in a CMDB to manage the asset lifecycle when the cloud provider manages all their IT assets. A CMDB that maps cloud assets provides additional visibility into services supported, costs incurred, risks faced, and compliance requirements. As cloud-based assets are deployed or decommissioned, the CMDB will marry the data from on-premises devices to provide a holistic view of the entire service environment.
Ensure governance and accountability
The significant investment required for IT assets means that the lifecycle must be carefully managed to ensure that the promised value is actualized. Governance mechanisms are necessary to extract value from IT assets by executing the following activities:
- Directing: The IT governing body must provide direction on the lifecycle of IT assets by defining the strategy to be applied at every stage. Investment in and usage of IT assets must be aligned to business needs, and policies are required to direct all persons involved in the lifecycle. An IT asset management policy is a key tool for outlining the organization’s position and leadership commitment to proper asset management by outlining roles and responsibilities, controls and guidelines, and compliance requirements to be followed by all stakeholders.
- Monitoring: As the IT asset moves through the lifecycle, the governing body must keep tabs on the change in status and benefits realization. Dashboards and reports that track IT asset usage and valuation are useful tools for monitoring, while verification audits provide outside-in confirmation of whether the IT asset status is in line with strategy and policy.
- Evaluating: The IT governing body must constantly evaluate the internal and external operating environment to identify whether organizational direction will still result in extracting value from IT asset investments or if changes are required. Sustainability, assessment of costs versus benefits, and technology trends are some of the issues worth considering across the entire lifecycle.
Note: The three dimensions of IT governance, per COBIT and ITIL4 guidance are evaluate, direct, and monitor, corresponding to the bullets above. The use of “monitor” here should not be confused with performance monitoring, which is its own IT practice. From an accountability perspective, IT asset governance must be supported by the right roles to manage the lifecycle activities. Here are some of the more important roles:
- Asset owner: Keeps the rights to the IT asset and sponsors the asset, i.e., maintains responsibility for the budget for acquisition.
- Asset custodian: Ensures the right utilization of the IT asset. This individual is assigned the asset to use based on role for a particular time period and may not be the same as the asset owner.
- License manager: Handles all licensing issues related to software and cloud products.
Automate and Integrate
Keeping accurate IT asset records is the only way for an organization to manage the asset lifecycle effectively. An asset register, whether manual (spreadsheet) or automated, is a key governance tool: It maintains the required information that identifies each asset’s status, ownership, and other key characteristics. Of course, an automated system is better for any organization with more than 20 IT assets, since it provides capabilities that go beyond just recording the standard details while reducing the risk of errors that come with manual inputs. These capabilities include standardizing data formats, automated discovery of IT assets in the environment, generating labels, associating relationships (with other IT assets, for example, a hardware device hosting a software license), and data exchange with other systems. An example of such a register is shown in the figure below: 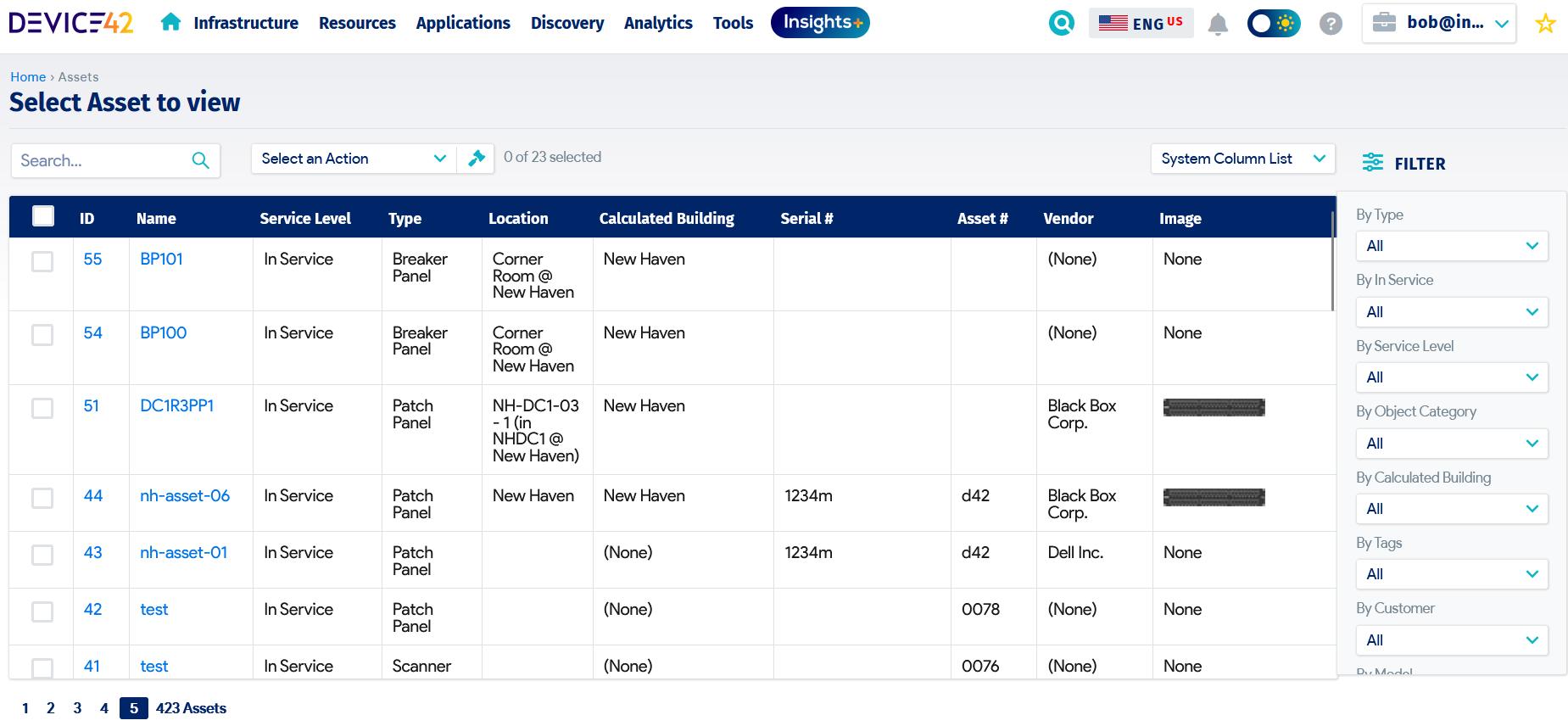
Automated asset register
Integrating the asset register with other organizational business systems extends the capabilities and benefits that would otherwise be missed when using a standalone system. For example, integration with the organization’s ERP permits the capture of financial information during acquisition, depreciation, and disposal, providing a single source of truth for more accurate and timely financial value computation. Monitoring systems integrated with the asset register will flag illegal assets and unwarranted license usage, which is critical for information security and service financial management processes.
Engage in proactive verification and auditing
An IT asset register is only as good as the quality of data within it: If the IT asset register is out of sync with the environment, the organization will be hampered when trying to determine and obtain full value from its investment. An ITAM best practice for managing IT asset information is to invest in regular proactive verification and audit activities. Taking advantage of automated systems can bring more efficiency to the process, but it is critical that a human eye verifies the output to capture any anomalies. Note that automation may improve the reliability of data and reduce the need for verification, but it does not remove the requirement entirely. Verification must be a continuous activity to identify gaps between the IT asset register and actual IT assets, with the organization then seeking to close the gaps quickly in order to increase accuracy. Auditing, on the other hand, is a planned endeavor that may involve external parties sampling the IT asset register information as part of governance, information security, or compliance requirements. Updates to the IT asset register following verification or audits must be done in a controlled manner to prevent erroneous information from being recorded that could hamper the effective use and management of the IT asset. Investigations and subsequent corrective actions must be reported and tracked comprehensively to completion.
Tie ITAM to ITSM practices
The IT asset lifecycle reaches its maximum potential when leveraged in combination with other IT service management (ITSM) practices. The asset information informs other practices mainly from a planning perspective since it serves as a base for other operational activities. Some of these practices include the following:
- Service financial management: Budgeting and accounting of IT assets and tracking their financial status in line with enterprise financial policies.
- Service request management: Fulfilling user requests related to IT asset assignment, reassignment, and decommissioning.
- Deployment management: Installing and uninstalling IT assets in line with deployment plans.
- Service configuration management: Transforming IT assets into configuration items and managing their attributes and relationships.
- Supplier management: Managing IT asset acquisition and maintenance through vendor contracts.
- Information security management: Assessing risks and implementing controls to address vulnerabilities that may impact IT assets.
- Change management: Assessing, authorizing, and scheduling changes to IT assets.
- Incident management: Addressing outages and performance degradation that impact IT assets.
Final Thoughts
Success in ITAM depends on having accurate information on the status of IT assets as well as continuously monitoring and optimizing IT asset utilization. Because IT assets directly link to business value, effective management increases the likelihood of positive ROI. This doesn’t come easily, however, and a lot of effort is necessary to manage the IT asset register to keep it up to date. Best practices in ITAM must be founded on governance and accountability mechanisms and then supported by the right automation tools.
What’s Next?
Mastering IT asset management requires an in-depth comprehension of many related facets of this topic, such as software asset management, software lifecycle management, asset disposal, the management and impact of of public cloud assets, and much more. To help you better understand IT asset management, we’ve created a set of guides in chapters that provide a deep dive into these and other important areas:
Chapter 1: IT Asset Management Reporting
Effective software asset management has become a critical business function. Learn the best practices for developing a SAM strategy and managing assets to enhance ROI with our free guide.
Chapter 2: Software Asset Management Best Practices
Effective software asset management has become a critical business function. Learn the best practices for developing a SAM strategy and managing assets to enhance ROI.
Chapter 3: IT Asset Disposition
Learn how to plan, sanitize, track, and dispose of IT assets by following best practices and seeing examples.
Chapter 4: IT Asset Lifecycle Management
Learn all about the six stages in the IT asset lifecycle and get tips and recommendations for managing each one in this free, comprehensive guide.
Chapter 5: Cloud Asset Management
As more organizations move to the cloud, proper cloud asset management is becoming a critical part of both strategy and execution. Learn more about the topic in our free guide. More chapters are coming soon, so please check back regularly!
Chapter 6: IT Asset Discovery
IT asset discovery is a fundamental part of overall IT asset management. Learn about various approaches to it and their benefits and risks in this free guide.