A Guide to Cloud Asset Management
Any organization with a strategic plan centered on digital transformation is likely to have public cloud assets as the foundation for accomplishing its objectives. The cloud is now seen as indispensable for most companies, whether they are hosting their own data and applications or accessing third-party ones. Given the need for flexibility and reliability, hosting on more than one cloud provider has become the default approach for enterprises around the world. Over 89% of organizations have a multi-cloud strategy, with 80% taking a hybrid approach of hosting on both private and public clouds. The growth in cloud adoption has also seen companies struggle with controlling cloud spending, with spending on public cloud services averaging 13% over budget.
Most organizations’ top cloud initiatives focus on migrating more workloads to the cloud or rationalizing their applications to take advantage of microservices architecture. As a result, cloud asset management is increasingly becoming a key capability that companies must improve to optimize their existing use of the cloud and deal with emerging issues such as cybersecurity and data privacy. It’s not enough to just be on the cloud: Having visibility into what infrastructure, applications, and licenses are deployed and then tracking their usage and costs is a substantial effort that requires governance and an all-hands-on-deck approach. This makes cloud asset management one of the key pillars of success in any digital transformation initiative.
By definition, cloud asset management is a coordinated organizational activity to realize value from cloud assets. This value will normally involve a balancing of cloud-related costs, risks, opportunities, and performance benefits. The activities within the scope include planning and acquisition of cloud assets, their use and optimization, controlling costs and licensing, addressing compliance and regulatory issues, and transitioning out of cloud environments.
In this article, we will tackle some of the major aspects to consider in cloud asset management as it relates to the activities above as well as associated trends and influences.
Executive Summary
The key concepts to consider in cloud asset management today include the following.
| Governance in a cloud environment | Applying governance policies, controls, and disciplines, including vendor governance |
| Onboarding cloud assets into the IT environment | Introducing cloud assets while managing risks through cloud migration and orchestration |
| Cloud asset management software considerations | Maintaining visibility and driving automation of cloud assets through software solutions |
| Cloud security considerations | Adopting good practices and standards for cloud security, including DevSecOps and Zero Trust |
| Managing cloud-related costs | Demonstrating business value by planning, tracking and optimizing costs while tackling budget overruns |
Governance in a cloud environment
Since an organization’s business strategy informs the deployment of cloud assets, top leadership must designate directions, constraints, and accountabilities for cloud asset management to ensure that the cloud supports the achievement of strategic objectives. Governance is implemented through the setting of appropriate policies, monitoring of adherence through audits, and evaluation of their impact on achieving objectives and outcomes. Within the cloud environment, failure to implement governance can result in risks materializing, such as security breaches, data loss, cost overruns, inefficiencies (including duplication), penalties for violation of data privacy regulations, and lopsided contracts in favor of vendors.
Scoping the extent of governance for cloud assets is a critical undertaking. Microsoft has identified five governance disciplines that can guide organizations in the right direction when it comes to setting policies regarding cloud assets:
- Cost management. Policies that address control of costs during the acquisition of cloud assets as well as the transfer of data across providers and environments.
- Security baseline. Policies that address the enforcement of cloud data security and privacy requirements across network, data, and asset configurations.
- Identity baseline. Policies that ensure that identity is consistently applied across cloud adoption efforts to minimize the risk of breach.
- Resource consistency. Policies that ensure that cloud resources are configured consistently to manage risks related to onboarding, drift, discoverability, and recovery.
- Deployment acceleration. Policies that drive centralization, standardization, and consistency in approaches to deployment and configuration.
Based on the selected cloud assets, governance also plays a key role in managing cloud service provider (CSP) relationships. There must be a clear definition of accountability for the consumer organization as well as the CSP, with the former largely responsible for business processes, access control, and integrations. Thorough scrutiny of cloud vendor contracts should be carried out to ensure a proper understanding of responsibilities for each party and clarity for any terms and conditions that may seem ambiguous. Addressing risks related to vendor lock-in and unsustainable switching costs must come from well-crafted cloud vendor procurement and management policies.
Onboarding cloud assets into the IT environment
Cloud migration
Replacing legacy applications and infrastructure with cloud assets is a significant undertaking rife with risks. Some of these systems carry mission-critical functions with years of inherent complexities baked into them. CSPs may lack the technology needed to support legacy systems in a lift-and-shift scenario, and the organizations themselves may be hesitant to disrupt the stability of these legacy systems, especially given that accountability for migration cannot be outsourced. These considerations end up contributing to barriers that bring hurdles to adopting cloud assets.
The ITIL 4 guidance on acquiring and managing cloud services highlights some typical risk factors and mitigations related to cloud migrations.
| Risk | Mitigation |
|---|---|
| Limited knowledge of legacy applications | Define a legacy migration strategy that thoroughly analyzes pros and cons for different options, including lift-and-shift vs rearchitecting. |
| Knowledge gap for existing IT staff on cloud assets | Conduct skills analysis and develop and implement a staffing plan and training program. |
| Lack of comprehensive understanding of system dependencies | Establish a formal configuration management approach that captures business services and associated component dependencies end to end in order to ensure that all bases are covered before migration. |
| Data loss due to transmission failures, software/hardware issues, environmental factors, or human error | Ensure that data is compliant with data retention policies pre-migration. Conduct pre-migration tests to identify any dependencies or points of failure. Define and test contingency plans, including full data recovery. |
| Vendor contract misalignment | Conduct due diligence to ensure that both parties understand accountabilities and terms. |
Any organization conducting a cloud migration should be ready to answer the following questions related to cloud asset management:
- What happens to the current assets—retirement, depreciation, or transfer of ownership?
- If the migration to the cloud is driven by a cost savings strategy, is this the current reality? How does it affect the financial balance sheet?
- Do legacy applications have the appropriate application architecture for optimal cloud usage?
- Does the organization have end-to-end visibility across hybrid environments including interdependencies before, during, and after migration?
For migration from one cloud provider to another, an exit strategy must be crafted in advance to cover matters related to contract terms, including data ownership, responsibilities, and post-migration cleanup.
Cloud orchestration
Cloud orchestration refers to the automated arrangement, coordination, and management of cloud assets. Onboarding cloud assets through orchestration saves time and facilitates effectiveness through standardization. Multiple computing, storage, and networking resources can be deployed faster, and adjustments to parameters can be made more responsive to environmental conditions (as opposed to human intervention). An example of such an orchestration capability is the Kubernetes Engine, which determines where to run Google Cloud containers, monitors their health, and manages the full lifecycle of VM instances.
Cloud asset management software considerations
Visibility and tracking of cloud assets are relatively easy when dealing with a single CSP. However, when it comes to managing hybrid environments where a mix of on-premises systems and multi-cloud services interact, this can be a difficult task. Effective governance of cloud assets requires investing in a solution that can span multiple environments, discovering these assets, and providing up-to-date status information that supports other service management activities, such as deployment management, incident management, and problem management. The figure below demonstrates such a cloud asset management solution, which can capture cloud asset information at the cluster and resource levels.
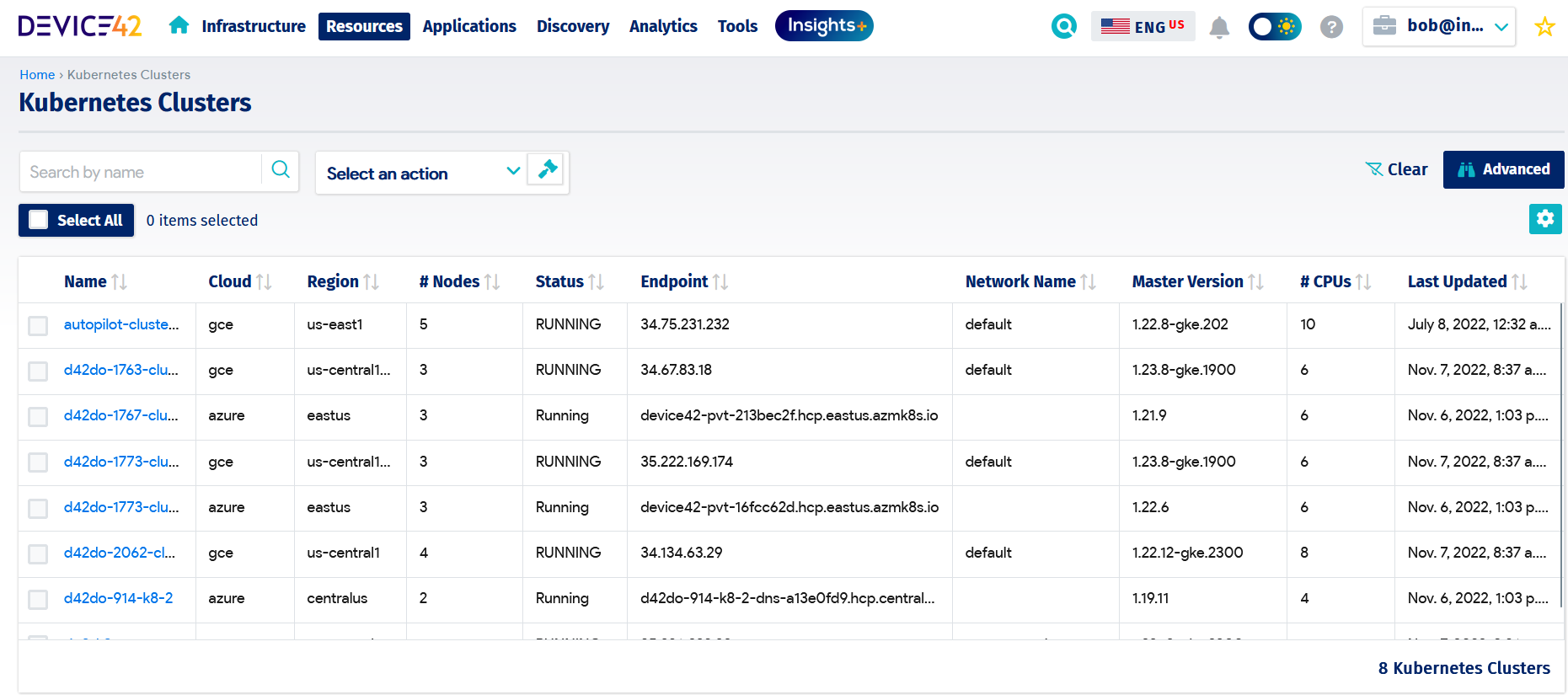
Cloud asset management solution
Pairing this capability with orchestration can go a long way toward ensuring effective cloud asset management. Automatic configuration management is concerned with the automation of tasks as well as templates to set up cloud services. Automation does not negate the need for governance, as these scripts and automated elements should be carefully managed, controlled, and reviewed. Failure to automate discovery, tracking, and configuration can lead to significant challenges with regard to cost management, compliance, and security.
Cloud security considerations
As mentioned earlier, the security of cloud assets and their associated data is paramount to extracting value from cloud systems. Some cybersecurity risks associated with migration and the recommended processes for their mitigation include the following:
| Risk | Mitigation |
|---|---|
| Theft of administrator and super-user credentials | Implement and test identity access controls and policies pre-migration. |
| Bypassing of authorized access to execute tasks or address issues | Create and check detailed operational procedures and security policies. Use CSP identity and access management tools, and test for non-standard access or activity. |
For the longest time, security controls have been seen as obstacles rather than enablers for cloud services, but approaches like DevSecOps are changing that perception. Here, security is treated like code, and security practitioners operate like developers to make security and compliance available to be consumed as services. DevSecOps practitioners attack cloud services like outsiders, through red and blue team exploit testing, and then work with DevOps teams to provide remediation actions.
One of the more recent approaches that has become a buzzword for securing cloud assets is Zero Trust, which Forrester defines as an information security model that defaults to denying access to applications and data. It addresses the assumption of implicit trust while inside a corporate network, something that threat actors and malicious insiders took advantage of. Zero Trust is based on three core principles:
- All entities are untrusted by default.
- Least privilege access is enforced.
- Comprehensive security monitoring is implemented.
Zero Trust has become a viable option for hybrid cloud environments since it provides a unified, holistic security posture across on-premises environments and multiple clouds. The diagram below from Microsoft outlines what an integrated Zero Trust architecture would look like, covering identities, endpoints, networks, data, apps, and infrastructure.
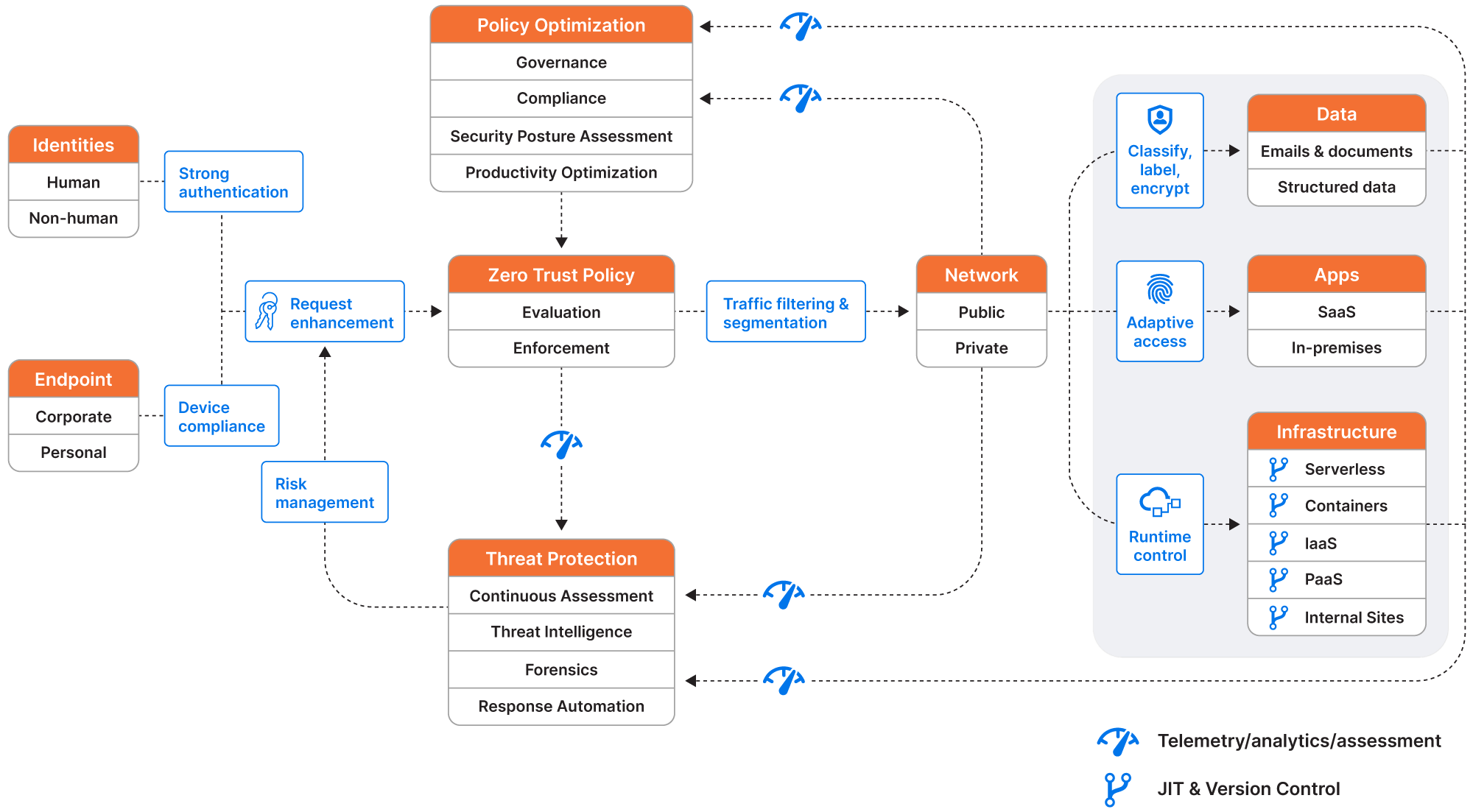
Zero Trust architecture
Other options for securing cloud assets include aligning existing security controls to international standards and good practices such as these:
- CSA Cloud Controls Matrix: A cybersecurity control framework for cloud computing that consists of 197 control objectives structured into 17 domains that cover all key aspects of cloud technology.
- ISO 27001:2022: The latest iteration of the information security management system standard that now includes cloud-centric security controls such as information security for the use of cloud services.
Managing cloud-related costs
One of the more discouraging aspects of using cloud services is the risk of bill shock. While CSPs have put mechanisms in place to help customers know their service costs and set thresholds for utilization, it always comes as a surprise to many organizations when they realize that sometimes cloud costs can spiral out of control. The original premise is still true: Cloud services are cheaper due to the substitution of OpEx-based cloud resources based on current demand in place of upfront CapEx for data center infrastructure and applications. Any investment in cloud assets must still follow the trusted model of a sound business case, which undergoes analysis and approval by key stakeholders to ensure a return on investment for the organization.
An article by Gartner lists seven reasons for cloud budget overruns:
- Ungoverned costs: Lack of scrutiny of cloud bills
- Unanticipated usage: Lack of controls to budget spending or demand management
- Not using commitments: Failure to take advantage of discount mechanisms for long-term use
- Dev/test waste: Overprovisioning resources and failure to turn off unused resources during off hours
- Too much production headroom: Lack of fine-tuning of autoscaling parameters
- Wrongsizing production: Failure to properly plan for capacity and track demand
- Suboptimal design and implementation: Bad architecture, design, or code that consumes more resources than necessary
This list boils down to a lack of effective governance and management of cloud assets. Billing reports must be scrutinized by a cross-section of stakeholders to check utilization trends and identify whether the costs of specific cloud assets are directly linked to value creation. Resources should be scaled up or down regularly and automatically to address demand and tackle costs if over budget. In addition, regular improvement of design and code can go a long way in addressing the oversizing of cloud assets.
Recommendations
The following principles apply, regardless of the implementation or environment, to any organization wanting to get the most out of its investment in cloud assets:
- Have a clear understanding of your requirements and evaluate multiple options before making a decision.
- Thoroughly scrutinize licensing structures as well as discounted offers to find the best options while limiting long-term cost impacts.
- Invest in the capability to understand and track scaling of demand over time.
- Align subscriptions with deployment/release schedules to prevent resource waste due to poor timing.
- Constantly analyze and refine solution designs and code to gain more efficiencies from cloud resources.
Conclusion
Cloud asset management is a discipline that requires commitment across the entire spectrum of the organization. Enterprise leaders must take the lead in ensuring that governance mechanisms are robust and that value for money is the paramount reason for investing in cloud resources. Regular monitoring and review of cloud costs and demand for services should not be left to technology teams only but should involve stakeholders from all relevant business domains. Technical excellence must apply in the design, development, deployment, and support of cloud services so that the return on investment is anchored on efficient and effective solutions that deliver strategic objectives.