SOC 2 Compliance Checklist: Trust Criteria, Audit Requirements and Examples
Processing customer data securely can make or break a business. For this reason, it’s essential to start with a solid assessment of your IT infrastructure and identify all the assets that are used directly or indirectly for this purpose.
SOC (Service Organization Controls) 2 is a widely recognized compliance standard that any IT solution provider can pursue to demonstrate its commitment to security and to build customer trust. In this article, we will go over frequent questions, provide a comprehensive SOC 2 compliance checklist, discuss how to prepare for the audit, and resolve some common challenges that this mission brings.
Quick summary of key questions and answers on SOC 2
| # | Question | Answer |
|---|---|---|
| 1 | What is the purpose of SOC 2? | SOC 2 provides customers with assurance that their data is processed securely. It increases credibility and customer trust and provides more business opportunities. |
| 2 | Is it mandatory? | No, but it is not uncommon for customers to ask for it. |
| 3 | What industries are in scope? | Any IT-related solution provider (products/ services), from SaaS tools to cloud platforms and data centers. |
| 4 | What are the benefits? |
|
| 5 | What are the evaluation criteria? | Five Trust Services Criteria:
Only the Security criterion is mandatory. You can scope SOC 2 to meet whatever applies to your business’s nature and objectives. |
| 6 | What controls are needed? | Controls are based on the Committee of Sponsoring Organizations (COSO) framework, an internal control framework for corporate governance. The controls are discretionary. |
| 7 | Where do I start? | Scope the criteria based on the nature of your business, then build your program as you see fit for the company. Design and implement the chosen controls, test them and close any gaps. |
| 8 | What are the SOC 2 types, and which one should I choose? | Type I evaluates the existence of controls at a point in time (on a certain date). This snapshot shows design effectiveness.
Type II evaluates the consistency of controls over a period of time (typically 12 months). Samples of controls and tests are assessed for design AND operational effectiveness. Most customers will want to see a Type II report. |
| 9 | Who can audit my company? | The third-party auditor needs to be accredited by the American Institute of Certified Public Accountants (AICPA) or have a certified public accountant (CPA) license. |
| 10 | Is a SOC 2 certification possible? | No. Unlike ISO 27001 compliance, the company does not get certified after the audit, though an assurance report is issued that can be shared externally. |
What controls are mandatory and optional for SOC 2?
SOC 2 is a flexible standard, so there are no clear-cut controls. Its Trust Services Criteria can be met by selecting controls tailored to the organization’s specific landscape and services.
As mentioned earlier, SOC 2 relies on the COSO framework. This establishes a direction for designing, implementing, and operating controls over each of the five Trust Services Criteria.
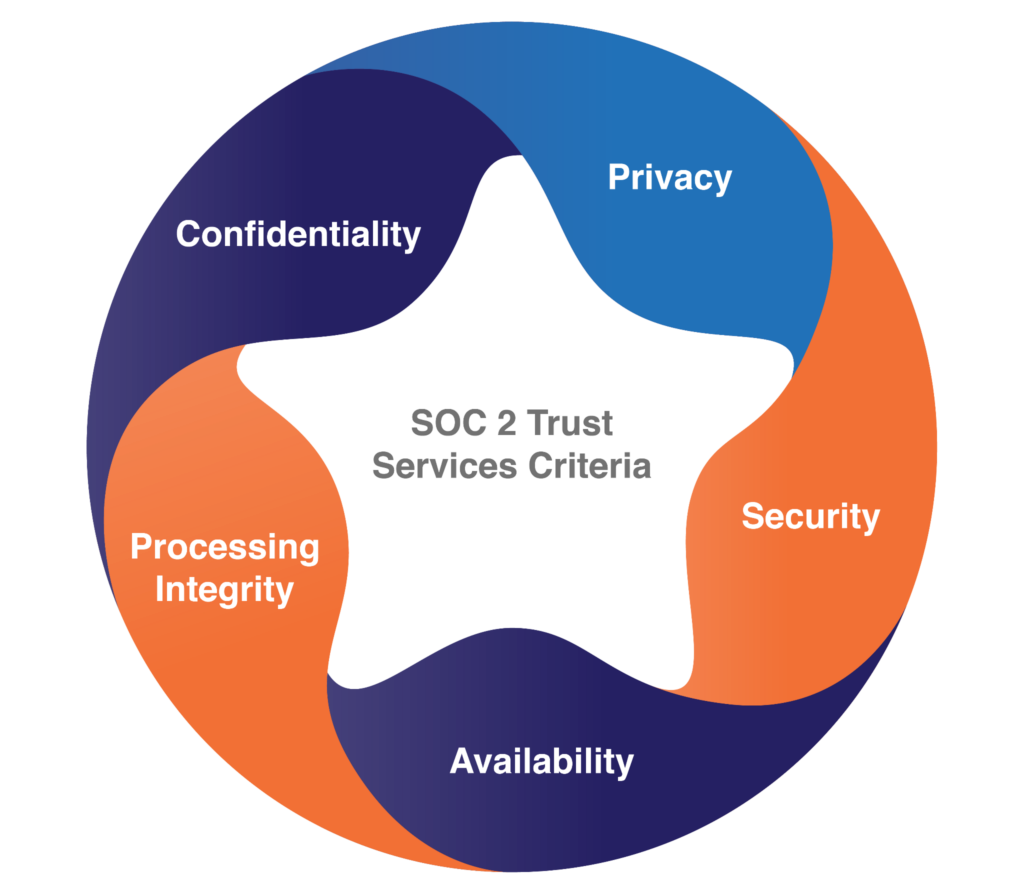
The SOC 2 Trust Services Criteria (source)
Note that the Security Trust Services Criterion is the only mandatory one, and even here, its controls are still discretionary. For any additional Trust Services Criteria you add into the scope, controls that meet those criteria’s objectives will need to be defined and implemented.
In determining scope, don’t exclude any relevant Trust Services Criteria. For instance, if you are processing personally identifiable information (PII), you should add the Privacy criterion. In other words, anything that is key to your clients should be included.
Controls, defined as “points of focus,” can be derived from the COSO framework, but do not expect them to be very prescriptive. For instance, you will see points of focus such as “Considers entity-specific factors.” Since this is very high-level, we have created this SOC 2 compliance checklist that keeps things simple and pragmatic. It is broken into five categories corresponding to each of the five Trust Services Criteria in the sections that follow to make it clearer and easier to digest.
As you review the checklist, keep in mind the ultimate focus: protecting customer data.
Summary of SOC 2 compliance checklist areas
| Checklist area | Description |
|---|---|
| Trust Services Criterion 1: Security (“Common Criteria”) | |
| Control Environment (CC1) | The audit looks horizontally at how security is being approached across the organization. This includes reporting lines, policies and procedures, and leadership commitment. |
| Communication and Information (CC2) | This area covers the communication outlook among the board of directors, management, and employees and between the company and external parties. |
| Risk Assessment (CC3) | An annual risk assessment should be performed, and identified security risks should be reported and treated in line with the company’s risk methodology. |
| Monitoring Activities (CC4) | CC4 encompasses a mix of evaluation methods of the existing controls, continuing to identify security threats and vulnerabilities. |
| Control Activities (CC5) | CC5 covers the design and implementation of new controls based on identified gaps. |
| Logical and Physical Access Controls (CC6) | Identity and access management is a key component of ensuring effective security. |
| System Operations (CC7) | This common criterion encompasses both written procedures and the hands-on operation of systems. |
| Change Management (CC8) | This area covers the implementation of controls for system development and changes. |
| Risk Mitigation (CC9) | CC9 deals with strategic decisions and tactical steps to mitigate company-wide risks. |
| Trust Services Criterion 2: Availability | |
| Capacity Management | Availability during normal operations is tied to the ability to plan, manage, and monitor system capacity. |
| Backup | Backing up customer data is a corrective type of control that enables data recovery in the case of system failures or unavailability. |
| Disaster Recovery (DR) | When all else fails, systems and their data should be restored through disaster recovery processes. |
| Trust Services Criterion 3: Processing Integrity | |
| Completeness, Accuracy, and Timeliness (CAT) | CAT controls are essential for integrity, on top of the secure design of data flows and system inputs and outputs. |
| Monitoring File Integrity | A process of monitoring file alteration, or attempts at alteration, should be both proactive and reactive to enable quick action. |
| Trust Services Criterion 4: Confidentiality | |
| Data Classification | Data classification plays a key role in determining how different types of customer data should be handled. |
| Data Leakage Protection (DLP) | Employees may send sensitive customer data out of your network, either accidentally or due to malice. DLP is all about preventing these leaks. |
| Data Encryption | Encryption ensures information confidentiality and should be used for data both at rest and in transit. |
| Data Retention and Disposal | Measures must be taken to protect information until it needs to be disposed of. |
| Trust Services Criterion 5: Privacy | |
| Regulatory Compliance | To ensure compliance, get acquainted with the requirements of jurisdictions relevant to your business, and derive controls from those requirements. |
| Personal Data Protection | Ensure that personal data is identified and protected based on the external needs of customers and regulatory requirements. |
Trust Services Criterion 1: Security (“Common Criteria”)
Since the Security Trust Services Criterion is mandatory, you should expect to have to define and implement controls for the following:
- The governance and management of security requirements
- Protecting information during its collection/creation, processing, transmission, and storage
- Protecting systems that process or store customer information and information relevant to the provided services
For this scope, nine Common Criteria (CC) sections are used, as reflected in the SOC 2 compliance checklist.
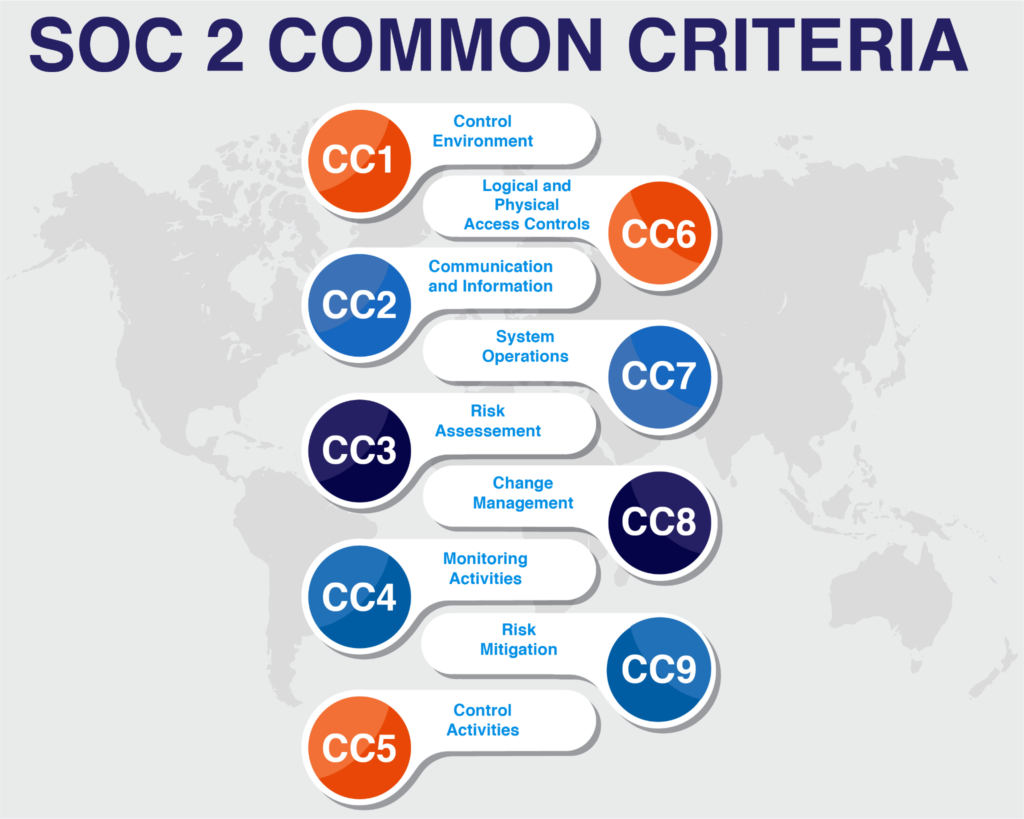
The Security “Common Criteria” (source)
Control Environment (CC1)
The audit looks horizontally at how security is being approached across the organization. This includes reporting lines, policies and procedures, and leadership commitment.
Recommendations:
- Have up-to-date organizational policies (updated at least annually).
- Define roles and responsibilities across the organization.
- Start early with embedding security in the company’s culture.
- Ensure management support for security efforts and transparency towards identified issues.
How software can help:
- A document management system can act as a single repository of documents.
- A board meeting tool can capture meeting minutes and store them centrally.
Communication and Information (CC2)
This area covers the communication outlook among the board of directors, management, and employees and between the company and external parties.
Recommendations:
- Demonstrate management oversight through meetings and associated minutes and reports.
- Publish documentation that specifically covers employee responsibilities (e.g., an acceptable use policy, employee handbook, and code of conduct).
- Conduct regular security awareness, training, and education activities.
- Implement communication methods with customers, which include communication on committed changes, customer support, system manuals, etc.
How software can help:
- It can provide collaboration sites for easy access to key documents.
- BI tools can enable consolidated reporting from various data sources.
- Platforms exist that support, or are dedicated to, training materials.
- A ticketing system can ensure traceable customer support.
Risk Assessment (CC3)
An annual risk assessment should be performed, and identified security risks should be reported and treated in line with the company’s risk methodology.
Recommendations:
- Use a risk framework such as NIST SP 800-37 or ISO 31000.
- Define system boundaries.
- Assess threats and vulnerabilities.
- Determine risks.
- Identify remediation plans.
How software can help: A compliance management tool can enable risk registration, a risk methodology with quantitative and qualitative variables, and capturing risk scores.
Monitoring Activities (CC4)
CC4 encompasses a mix of evaluation methods of the existing controls, continuing to identify security threats and vulnerabilities.
Recommendations:
- Perform scheduled vulnerability scans.
- Monitor network and endpoint activity.
- Conduct regular penetration tests.
- Request audit and test results from your third-party vendors.
- Follow up on any identified deficiencies.
How software can help:
- Tools use behavior analysis and alert on suspicious activity patterns.
- Logs can be integrated into a security information and event management (SIEM) system.
Tools such as Device42 can inventory IT assets and gather valuable information for assessing vulnerabilities, for example, servers and OS versions approaching End-of-Support or End-of-Life.
Device42 also offers integrated Data Center Infrastructure Management (DCIM), monitoring everything from environmental conditions to patch panel management, detailed device information, and even spare parts.
Control Activities (CC5)
CC5 covers the design and implementation of new controls based on identified gaps.
Recommendations:
- Use the framework of your choice to guide you in defining security controls (e.g., the NIST Cybersecurity Framework or ISO27001:2022).
- Employ a mix of preventive, detective, corrective, and recovery controls.
- Design controls in a scalable and standardized manner.
- Maintain a balance: Controls should be proportionate to the risks they are designed to mitigate.
- Do not leave any open gaps: Assess and respond to all risks, even if the answer sometimes will be to accept certain risks.
How software can help: Use a compliance management system to register your control taxonomy, monitor the control implementation progress, capture exceptions, and define control tests.
Logical and Physical Access Controls (CC6)
Identity and access management is a key component of ensuring effective security.
Recommendations:
- Centrally manage the provisioning and de-provisioning of identities.
- Implement role-based access control.
- Manage and limit privileged accesses.
- Implement stronger authentication for sensitive systems.
- Do not neglect physical security access control.
How software can help:
- Consolidate identity management and access through an automated tool.
- Implement SSO to your environment’s general resources and MFA for sensitive systems.
- Use a privileged access management (PAM) tool to centralize the management of administrators.
- Use a combination of card readers and PIN pads or biometrics for physical access to sensitive areas.
System Operations (CC7)
This common criterion encompasses both written procedures and the hands-on operation of systems.
Recommendations:
- Use standardized system configurations.
- Monitor infrastructure and detect any unknown components, activity, or changes.
- Detect and respond to incidents (incident response plan).
- Ensure capabilities to recover after an incident (disaster recovery plan).
- Ensure periodic training for roles involved in operations and incident response.
How software can help: Use network detection and response (NDR) or extended detection and response (XDR) solutions to monitor infrastructure and deploy an internal or outsourced security operations center (SOC).
Device42 provides a single source of truth for IT operations by integrating existing ITSM, SIEM, and configuration management tools.
Change Management (CC8)
This area covers the implementation of controls for system development and changes.
Recommendations:
- Follow secure development lifecycle (SDLC) best practices, such as code versioning and an independent testing suite before deployment.
- Use change templates.
- Implement a change approval board (CAB).
- Have a rollback plan.
How software can help:
- Code repositories and libraries can ensure controlled access and versioning.
- Automated workflows can be created through change tickets.
- Automating deployment and release processes reduces human error and wasted hours for staff.
Risk Mitigation (CC9)
CC9 deals with strategic decisions and tactical steps to mitigate company-wide risks.
Recommendations:
- Define business continuity plans (BCPs).
- Consider both types of risk response: mitigation (adding controls) and transfer (e.g., insurance).
- Manage third-party service risks.
- Learn from incidents and implement additional mitigation measures.
How software can help:
- Automated BCP workflows can assist with keeping plans up to date.
- Contract management tools can provide a one-stop shop for vendor relationship management.
Solutions provided by Device42 enable having real-time information for every asset and their relationships and interdependencies, giving you the power to understand your own environment better and achieve compliance automation.
Trust Services Criterion 2: Availability
This Trust Services Criterion should be included if your company explicitly ensures the availability of services, if you have strict service-level agreements (SLAs) to meet, or if availability is meant to bring a competitive edge to your product or service.
Note that availability is not solely focused on system uptime requirements: It also demands that data be accessible in a timely fashion.
Capacity Management
Availability during normal operations is tied to the ability to plan, manage, and monitor system capacity.
Recommendations:
- Plan for threats that can affect availability (e.g., DDoS attacks or calamities).
- Define realistic SLAs.
- Eliminate single points of failure.
- Design cluster failover, redirection, and restoration processes.
How software can help:
- Capacity management tools should measure current usage, forecast upcoming demands for scaling, and detect any risks of falling below the committed availability thresholds.
- Redundant arrays of independent disks (RAID) store the same data in different arrangements of hard disks or solid-state drives to eliminate single points of failure.
Device42 monitors the real-time activity of your data center infrastructure, enabling you to take immediate action.
Backup
Backing up customer data is a corrective type of control that enables data recovery in the case of system failures or unavailability.
Recommendations:
- Perform scheduled backups (full, incremental, or differential) appropriate for the data sensitivity and availability requirements and recovery point objectives (RPOs).
- Ensure the security and reliability of backups (encryption, offsite storage, and regular testing).
How software can help:
- Backup software can help ensure that your data is backed up efficiently and securely.
- A storage area network (SAN) eliminates single points of failure because it is separate from your main network.
- Backup tapes can be used for long-term data storage/archival.
Disaster Recovery (DR)
When all else fails, systems and their data should be restored through disaster recovery processes.
Recommendations:
- Create, maintain, and test a disaster recovery plan (DRP).
- Enable customers to have access to your DR test results and corrective actions.
- Test the DRP at least annually.
How software can help: A redundant data center enables disaster recovery.
Trust Services Criterion 3: Processing Integrity
If customers rely on your systems for the complete, accurate, authorized, and timely processing of their data, this Trust Services Criterion is also required. For instance, it is applicable to systems that process financial, tax, and HR information.
Data management principles for integrity should observe any regulatory requirements, such as the Sarbanes-Oxley (SOX) Act. They should employ controls that prevent the intentional or accidental alteration of data (such as database access and modification restrictions / nonrepudiation) and controls that validate the outputs as expected (such as checksums, data feed monitoring, and exception alerts and treatment).
Completeness, Accuracy, and Timeliness (CAT)
CAT controls are essential for integrity, on top of the secure design of data flows and system inputs and outputs.
Recommendation: Implement CAT controls in application designs, such as checksums, automated alerts to handle exceptions, input and output limits, etc.
How software can help: Running transactions through automated data testing can detect file and processing alterations.
Monitoring File Integrity
A process of monitoring file alteration, or attempts at alteration, should be both proactive and reactive to enable quick action.
Recommendations:
- Use processes and automation to capture unexpected or unauthorized modifications in transactions.
- Implement measures to identify and prevent errors or inaccuracies.
- Consider adopting digital certificates for transferring critical files; these provide integrity, authenticity, and nonrepudiation.
How software can help: Software that scans for suspicious changes in critical files can help with processing integrity.
Device42 can automatically discover unknown devices and software connected to your network that may pose a threat to processing integrity.
Trust Services Criterion 4: Confidentiality
This criterion may seem self-explanatory, but how do you actually best ensure the confidentiality of customer data? Controls can be many, such as the examples that follow in various areas:
- Governance controls: Segregation of duties, least privilege, need to know and Chinese walls principles, policies for data classification, and NDAs
- Technical controls: Access recertification, network hardening, data leakage prevention system, encryption at rest and in transit, multi-factor authentication (MFA) for access to sensitive information, data masking techniques, and separation of environments
- Physical controls: Minimizing visibility and information for areas that store sensitive information, storage media labeling and encryption, and defined physical perimeters
- People controls: Periodic people awareness and training on expected behavior and acceptable use of information and equipment as well as background checks before onboarding
Data Classification
Data classification plays a key role in determining how different types of customer data should be handled.
Recommendations:
- Define data classification and information asset management policies.
- Ensure that each asset is linked to an accountable data owner.
- Add classification and metadata labeling.
How software can help:
- Utilize a data classification and labeling tool.
A prerequisite of data classification is to identify all information assets that process the associated data. You can discover assets automatically with Device42, including hardware, software, and cloud infrastructure.
Data Leakage Protection (DLP)
Employees may send sensitive customer data out of your network, either accidentally or due to malice. DLP is all about preventing these leaks.
Recommendations:
- Identify data leakage protection controls.
- Sign NDAs and confidentiality agreements for information processing.
- Train employees and contractors on the acceptable use of information and devices, including the use of authorized tools, data transfer options, and remote working behavior.
How software can help:
- Employ a DLP tool.
- Add intrusion prevention systems (such as antivirus tools) and intrusion detection systems (such as malware detection products) to your network to quickly detect any attempts to access data without authorization and prevent data exfiltration.
Data Encryption
Encryption ensures information confidentiality and should be used for data both at rest and in transit.
Recommendations:
- Use standard encryption algorithms.
- Encrypt laptops and devices to protect data at rest.
- Use secure data transfer channels through SSL certificates and Transport Layer Security (TLS).
- Document and implement key management processes.
How software can help:
- Use authentication tools that work with strong symmetric or asymmetric encryption (tokens with one-time passwords, PKI environments, etc.).
- Use VPNs to secure remote connections.
- Key management systems enable secure key administration.
SSL certificate management is easy with Device42.
Data Retention and Disposal
Measures must be taken to protect information until it needs to be disposed of.
Recommendations:
- Observe legal requirements and customer requirements for data retention.
- Set an automated retention period upon document creation.
How software can help:
- Use system policy enforcement for maximum retention periods.
- When data is no longer needed, avoid data remanence through secure disposal: shredding, degaussing, or physical destruction.
Trust Services Criterion 5: Privacy
This Trust Services Criterion must be included for companies that access, store, transfer, and process personal data. Since this is such a broad term, there is a good chance that at least some personal data or personally identifiable information ends up being handled by your systems.
Protection here is closely tied to laws and regulations, such as GDPR in the EU or HIPAA, COPPA, and CCPA in the US. At the core of privacy laws lie requirements to handle this type of data responsibly, for a limited time, and only for business purposes and to use only the minimum amount of data necessary.
Personal data spanning through systems should have strict access control, data masking, retention, and disposal requirements.
Regulatory Compliance
To ensure compliance, get acquainted with the requirements of jurisdictions relevant to your business, and derive controls from those requirements.
Recommendations:
- Identify privacy requirements.
- Determine how, when, where, and why you are processing personal data.
- Seek legal advice as needed.
How software can help: Privacy compliance tools that provide access to regulatory resources can speed up your assessment.
Personal Data Protection
Ensure that personal data is identified and protected based on the external needs of customers and regulatory requirements.
Recommendations:
- Identify systems that process personal data and which types of PII or personal data are processed (e.g., name, location, cardholder data, and health data).
- Control access to personal data: Prohibit unauthorized access and do not put PII / personal data in non-production environments unless anonymized.
- Add privacy requirements in all supply chain contracts.
- Securely dispose of personal data when no longer needed.
How software can help: A test data management tool can have data masking functions, such as tokenization, pseudonymization, or anonymization.
The discovery of systems that process PII can be smooth sailing with Device42.
Preparing for the SOC 2 audit
Remember that although you are paying for the audit, the auditor is not working for you and will make an objective assessment of your implementation. The SOC 2 assurance report will confirm whether the control environment is appropriate and whether you have taken reasonable measures to protect customer data.
Here are 10 steps to help you prepare for this undertaking.
- Choose the appropriate scope: If something is out of scope for your organization type and business model, it makes sense to exclude it. For example, if you offer a work area recovery site with bare infrastructure and no data, you may not need the Processing Integrity criterion.
- Identify other external requirements: Ensure that you are aware of any other applicable standards and regulatory requirements with which your business must comply. These may be in the jurisdiction where you operate and those of transborder customers.
- Conduct a self-assessment: It’s wise to avoid wasting resources on a SOC 2 audit before you engage in a self-assessment. Get to know your threats and vulnerabilities, define your risks, and craft treatment plans for any gaps that fall outside your risk appetite.
- Define policies and procedures: Policies, processes, and procedures set the baseline for compliance and the direction for employees. They will be audited, and their absence is always a red flag.
- Implement controls: As part of the risk response, make sure that risks identified during the risk assessment are mitigated through new or adjusted controls.
- Test controls: Follow up on operational effectiveness through cyclic testing. Also, make sure that proactive processes are also in place; for example, replace or upgrade software that’s approaching End-of-Support and remove access rights for departing employees on time.
- Close any gaps: Capture control deviations and implement measures for remediation.
- Create internal awareness: Conduct targeted sessions on relevant security topics: phishing, incident reporting, secure coding, security on the go, etc. Also, consider doing SOC-2-focused training.
- Prepare for the audit: Engage promptly with a trusted company and set expectations for the SOC 2 audit. Prepare a document repository, ensure that you can extract relevant evidence, and confirm people’s availability.
- Continuously monitor: Generally speaking, your security program needs to be broader than working around the SOC 2 audit. Make sure you continue to improve policies, controls, and employee awareness.
Challenges and solutions
Keep the following in mind to have the best possible experience during the audit.
Remember that SOC 2 controls are not prescriptive
The five Trust Services Criteria rely on 17 principles of COSO controls that contain 87 points of focus. To complicate things, these are not mandatory controls nor black-and-white requirements. This can be converted into an advantage, though, because this is where flexibility and customizations come into play for each organization. The SOC 2 compliance checklist above is a practical tool to get started.
Identifying which systems process customer data is not always straightforward
Amid a hybrid environment with dozens of upstream and downstream data flows, customer data may be accessed or handled by a variety of systems and tools that may seem surprising. Protective measures must expand beyond the obvious core applications.
Device42 provides automated discovery, so you can populate your inventory quickly and effortlessly with an extensive range of autodiscovery tools that support physical, virtual, cloud, and hybrid infrastructures.
Manual processes are red flags
SOC 2 looks at sensitive processes and how they are operated because wherever there is the human factor, there is the potential for human error or misuse. For example, if application access is recertified manually, onboarding is not standardized, and information assets are added into the CMDB only if someone reminds themselves to do so, the audit outcome may not be that positive.
It’s important to automate as many processes and workflows as possible
Device42 can help you meet your compliance and audit requirements comprehensively and confidently, with extensive automation features built into all products.
Summary of key concepts
Although SOC 2 compliance is not mandatory, most customers will request it as evidence that their data is protected. The SOC 2 compliance report acts as the best assurance in this sense, building trust and giving companies a competitive edge. You can use the SOC 2 compliance checklist in this article to help you prepare for the audit.
Of the five Trust Services Criteria to potentially add to your scope, remember that Security is mandatory. Controls here span from operational requirements to governance and from configurations to company culture.
Manual processes are red flags for audit. Save time and reduce human error by automating as many processes as possible. Device42 offers diverse products that automate relevant tasks, including IT asset management and software license management, IT operations, transformation, and infrastructure migration.
While it’s not easy to master the requirements of each compliance standard, you now have the tools to pass through your first SOC 2 audit!